Networks
For many years, computers have played as important a role in communication as they do in computation. This communication is accomplished using computer networks. Like complex highway systems that connect roads in various ways to allow cars to travel from their origin to their destination, computer networks form an infrastructure that allows data to travel from some source computer to a destination. The computer receiving the data may be around the corner or around the world.
Network fundamentals
[edit | edit source]A computer network is a collection of computing devices that are connected in various ways to communicate and share resources. Email, instant messaging, and web pages all rely on communication that occurs across an underlying computer network. We use networks to share both intangible resources, such as files, and tangible resources, such as printers.
Usually, the connections between computers in a network are made using physical wires or cables. However, some connections are wireless, using radio waves or infrared signals to convey data. Networks are not defined only by physical connections; they are defined by the ability to communicate.
Computer networks contain devices other than computers. Printers, for instance, can be connected directly to a network so that anyone on the network can print to them. Networks also contain a variety of devices for handing network traffic. We use the generic term node or host to refer to any device on a network.
A key issue related to computer networks is the data transfer rate, or bandwidth, the speed with which data is moved from one place on a network to another. We are constantly increasing our demand on networks as we rely on them to transfer more data in general, as well as data that is inherently more complex (and as a consequence larger). Multimedia components such as audio and video are large contributors to this increased traffic.
Types of Networks
[edit | edit source]Computer networks can be classified in various ways. One method of categorizing the different types of networks is by their scope or scale, and as such the "area" they cover. Consequently, and as a result of tradition, networks in this sense are called area networks. Other methods of categorization include the network configuration such as topology of area networks, for example ring, star, and bus configurations.
3.1.1 Identify different types of networks.
Local Area Network
[edit | edit source]A local-area network (LAN) connects network devices over a relatively short distance. A LAN is usually owned, operated, and managed by a single organization, such as a business, school, or government agency. A networked office building, school, or home usually contains a single LAN, though sometimes one building will contain a few small LANs (perhaps one per room), and occasionally a LAN will span a group of nearby buildings. A LAN allows multiple devices such as computers, printers, and servers, to connect and communicate with each other. This enables the sharing of resources and data. In contrast, a wide area network (WAN) covers a larger area and may be composed of multiple LANs. A LAN is composed of routers, switches, hubs, access points, all enabling devices to connect to different types of servers.
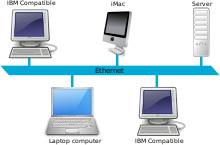
The most famous and widely used LAN technology is Ethernet. Ethernet was developed in the 1970s at Xerox Parc in Silicon Valley as a way for devices to communicate. Unlike wireless communication, communications pass through wires in an Ethernet network. Every device, referred to as a node, is connected via Ethernet cables. Nodes communicate using protocols that construct frames. Frames carry information between a sender and receiver. Since signals sent by one node to another tend to get lost across long distances, repeaters are located along Ethernet cables to re-amplify signals on the way to their destinations.
In TCP/IP networking, a LAN is often but not always implemented as a single IP subnet and tend to use a physical connection between nodes, such as that via Ethernet cables.
Virtual Local Area Network
[edit | edit source]A virtual local-area network (VLAN) is a network of computers that behave as if they are connected to the same topology, but are actually physically located in different segments of a LAN. VLAN configurations are generally comprised and maintained via software rather than hardware. This makes the network extremely flexible as it allows computers to be removed from the VLAN and located elsewhere without having to physically rewire the whole system to fit the new configuration.
Wide Area Network
[edit | edit source]A wide-area network (WAN) is a geographically-dispersed group of two or more LANs. A WAN permits communication among smaller networks. Often one particular node on a LAN is set up to serve as a gateway to handle all communication going through that LAN and other networks.
Storage Area Network
[edit | edit source]Overview
A storage-area network (SAN) is a type of local area network (LAN) designed to handle large data transfers. A SAN typically supports data storage, retrieval and replication on business networks using high-end servers, multiple disk arrays and Fibre Channel interconnection technology.
Devices they work with
SANs can work with many peripheral devices, such as disks, magnetic tape or optical storage. They also include both hardware (hubs, switches, gateways, routers…) and software (such as the SAN management software) components to ensure connection between storage devices and servers.
Scale
SANs are also in a way that they can be used in both short and long distance connections: in the first case, local communication can be established thanks to traditional copper-based cables, and in the second long range connections function with optical fiber.
Use case
SANs are often used in enterprise computing: in a data center for example, composed of hundreds of servers, virtual machines can overflow if the workload is superior to what the local storage can handle. Instead of losing the data, or attempting to organize data repartition using physical disks, the enterprise might choose to use a SAN where the data can be transferred, collectively managed and protected.
SANs can also help in the case of improving storage availability: this network offers a central location for all data storage, and can enable administrators to pool and manage storing devices in a simpler way.
Advantages
In such ways, we can understand the many advantages of a SAN:
- they improved application availability: as SANs enable storage to exist independently of applications, they ensure that these apps can access data through multiple paths (increasing overall reliability, availability and serviceability
- they better application performance: as SAN greatly help in limiting app overflow, their performance is not altered by important data processing
- they consolidate and centralize data: SANs make data management simpler as they increase retrieval flexibility and ensure high availability
- they protect data from malware: SANs protect data from malicious attacks
Drawbacks
The main flaw of SANs is their price: these installations are very expensive and difficult to maintain, making them a good networking option for big companies only.
Wireless Local Area Network
[edit | edit source]A wireless local-area network (WLAN) provides wireless network communication over short distances using radio or infrared signals instead of traditional network cabling.
A WLAN typically extends an existing wired local area network. WLANs are built by attaching a device called the access point to the edge of the wired network. Clients communicate with the access point using a wireless network adapter similar in function to a traditional Ethernet adapter.
Internet
[edit | edit source]Extranet
[edit | edit source]Virtual Private Network
[edit | edit source]A virtual private network (VPN) is a type of WAN such that it supplies network connectivity over a possibly long physical connection. The key feature of a VPN, however, is its ability to use public networks like the Internet rather than rely on private leased lines using a method called tunnelling, a VPN use the same hardware infrastructure as existing Internet or intranet links. VPN technologies includes various security mechanisms to protect the virtual, private connections. VPN technologies implement restricted-access networks that utilise the same cabling and routers as a public network, and they do so without sacrificing features or basic security.
Peer-to-Peer Network
[edit | edit source]A peer-to-peer (P2P) is an approach to computer networking where all computers share equivalent responsibility for processing data. Peer-to-peer networking (also known simply as peer networking) differs from client-server networking, where certain devices have responsibility for providing or serving data and other devices consume or otherwise act as clients of those servers.
Open Systems
[edit | edit source]3.1.2 Outline the importance of standards in the construction of networks.
Early in the development of networks, commercial vendors came out with a variety of technologies that they hoped businesses would adopt. The trouble was that these proprietary systems were developed with their own particular nuances and did not permit communication between networks of differing types. As network technologies grew, the need for interoperability became clear; we needed a way of computing systems made by different vendors to communicate.
3.1.3 Describe how communication over networks is broken down into different layers.
An open system is one based on a common model of network architecture and a suite of protocols used in its implementation. Open-system architectures maximise the opportunity for interoperability.
The International Organisation for Standardisation (ISO) established the Open Systems Interconnection (OSI) Reference Model to facilitate the development of network technologies. It defines a series of layers of network interaction.
| OSI Model | ||||
|---|---|---|---|---|
| Data unit | Layer | Function | ||
| Host layers |
Data | 7. Application | Network process to application | |
| 6. Presentation | Data representation, encryption and decryption, convert machine dependent data to machine independent data | |||
| 5. Session | Interhost communication, managing sessions between applications | |||
| Segment | 4. Transport | Reliable delivery of packets between points on a network. | ||
| Media layers |
Packet | 3. Network | Addressing, routing and (not necessarily reliable) delivery of datagrams between points on a network. | |
| Bit / Frame | 2. Data link | A reliable direct point-to-point data connection. | ||
| Bit | 1. Physical | A (not necessarily reliable) direct point-to-point data connection. | ||
Each layer deals with a particular aspect of network communication. The highest level deals with issues that relate most specifically to the application program in question. The lowest layer deals with the most basic electrical and mechanical issues of the physical transmission medium (such as types of writing). The other layers fill in all other aspects.
It is important to know that networking technology as we know it today is only possible through the use of open-system technology and approaches such as the OSI Reference Model.
3.1.4 Identify the technologies required to provide a VPN.
VPNs require a protocol that emphasises authentication and encryption. Authentication allows VPN clients and servers to correctly establish the identity of people on the network and encryption allows potentially sensitive data to be hidden from the general public. Several network protocols have become popular as a result of VPN developments, such as IPSec, SOCKS.
3.1.5 Evaluate the use of a VPN.
A VPN is one solution to establishing long-distance and/or secured network connections. VPNs are normally deployed by businesses or organisations rather than by individuals, but virtual networks can be reached from inside a home network. Compared to other technologies, VPNs offers several advantages, particularly benefits for wireless local area networking.
A VPN can save an organisation money in several situations:
- Eliminating the need for expensive long-distance leased lines.
- Reducing long-distance telephone charges.
- Offloading support costs.
However, despite their popularity, VPNs are not perfect and limitations exist as is true for any technology. Organisations should consider issues like the below when deploying and using virtual private networks in their operations:
- VPNs require detailed understanding of network security issues and careful installation / configuration to ensure sufficient protection on a public network like the Internet,
- The reliability and performance of an Internet-based VPN is not under an organisation's direct control. Instead, the solution relies on an ISP and their quality of service.
- Historically, VPN products and solutions from different vendors have not always been compatible due to issues with VPN technology standards. Attempting to mix and match equipment may cause technical problems, and using equipment from one provider may not give as great a cost savings.
Data transmission
[edit | edit source]Network Protocols
[edit | edit source]3.1.6 Define the term protocol.
Another key issue in computer networks is the protocols they use. A protocol is a set of rules describing how two things interact. In networking, we use well-defined protocols to describe how transferred data is formatted and processed. Protocols are defined as a code that prescribes strict adherence to correct etiquette and procedure -- a diplomatic exchange. Computing terminology has borrowed the word to describe the correct etiquette for computers to use when communicating with one another. Thus, protocols allow for the control of data, can prevent congestion, deadlocks, check for errors.
3.1.7 Explain why protocols are necessary.
Following the general concepts of the OSI Reference Model, network protocols are layered such that each one relies on the protocols that underlie it;
| Simple Mail Transfer Protocol | File Transfer Protocol | Telnet | |||
| Transmission Control Protocol | Datagram Protocol | ||||
| Internet Protocol | |||||
This layering is sometimes referred to as a protocol stack. The layered approach allows new protocols to be developed without abandoning fundamental aspects of lower levels. It also provides more opportunity for their use, in that the impact of new protocols on their aspects of network processing is minimised. Sometimes protocols at the same level provide the same service as another protocol at that level, but do so in a different way.
A protocol is, in one sense, nothing more than an agreement that a particular type of data will be formatted in a particular manner. The details of file formats and the sizes of data fields are important to software developers who are creating networking programs. The importance of these protocols is simple to understand; they provide a standard way to interact among networked computers.
The lower two layers in the above example form the foundation of Internet communication. Other protocols, sometimes referred to as high-level protocols, deal with specific types of network communication. These layers are essentially one particular implementation of the OSI Reference Model and correspond in various ways to the levels described in that model.
Network Connections
[edit | edit source]One can use any of several technologies to connect to other nodes in a network, or between networks. The most popular techniques include phone modems, digital subscriber lines, cable modem, and fibre optics.
3.1.10 Outline the characteristics of different transmission media.
The telephone system had already connected homes throughout the world long before the desire for Internet connections came along. Therefore, it makes sense that the first technique for home-based network communication was a phone modem. The word modem stands for modulator/demodulator. A phone modem converts computer data into an analog audio signal for transfer over a telephone line, and then a modem at the destination converts it back into data again. One audio frequency is used to represent binary 0 and another to represent binary 1.
This approach was fairly simple to implement because it does not require any special effort on the part of the telephone company. Because the data is treated as if it were a voice conversation, no special translation is needed except at either end. But that convenience comes at a price. The data transfer rate available with this approach is limited to that of an analog voice communication, usually 64 kilobits per second at most.
A phone line can provide a much higher transfer rate if the data is treated as digital rather than analog. A digital subscriber line (DSL) uses regular copper phone lines to transfer digital data to and from the phone company's central office. Because DSL and voice communication use different frequencies, it is even possible to use the same phone line for both purposes.
A third option for home connections is a cable modem. In this approach, data is transferred on the same line that your cable TV signals come in on. Several leading cable TV companies have pooled their resources to create Internet service providers for cable modem services.
Fibre-optic communication cable is a network cable that contains strands of glass fibers inside an insulated casing. These cables are designed for long distance and very high bandwidth (gigabit speed) network communications. The fibre-optic cables carry communication signals using pulses of light. While expensive, these cables are increasingly being used instead of traditional copper cables, because fiber offers more capacity and is less susceptible to electrical interference.
3.1.8 Explain why the speed of data transmission across a network can vary.
All type of physical connections, be it digital subscriber line (DSL), cable modem, or even phone modems fall into the category of broadband connections. Depending on the location and whether access is by satellite, phone wire, video cable, or fiber optics, it is possible to obtain broadband transfer speeds that range from 384 kilobits per second to 1 gigabits per second. Increasingly more households are moving away from the use of phone modems to a broadband solution for their computing network needs. Debate between the DSL and cable modem communities continue to rage to see who can claim the dominant market share.
3.1.9 Explain why compression of data is often necessary when transmitting across a network.
Data compression is the reduction of bits by encoding data using fewer bits than the original representation. File compression is commonly used when sending a file from one computer to another. It makes the file smaller and the transfer faster with no data loss.
Packet Switching
[edit | edit source]3.1.6 Define the term data packet.
To improve the efficiency of transferring data over a shared communication line, messages are divided into fixed-size, numbered packets. These packets are sent over the network individually to their destination, where they are collected and reassembled into the original message. This approach is referred to as packet switching.
3.1.11 Explain how data is transmitted by packet switching.
The packets of a message may take different routes on their way to the final destination. Therefore, they may arrive in a different order than the way they were sent. The packets must be put into the proper order once again, and then combined to form the original message. A packet may make several intermediate hops between computers on various networks before it reaches its final destination. Network devices called routers direct the packets as they move between networks. Intermediate routers don't plan out the packet's entire course; each router merely knows the best next step to get it closer to its destination. Eventually a message reaches a router that knows where the destination machine is. If a path is blocked due to a down machine, or if a path currently has a lot of network traffic, a router might send a packet along an alternative route.
If a communication line spans a long distance, such as across an ocean, devices called repeaters are installed periodically along the line to strengthen and propagate the signal. Digital signal loses information only if it is allowed to degrade too much. A repeater keeps that from happening.
Wireless networking
[edit | edit source]3.1.12 Outline the advantages and disadvantages of wireless networks.
Some of the advantages of wireless networks include the flexibility of their ad-hoc situation when additional workstation was required, the implementation cost is cheaper than wired network, they are ideal for the non-reachable places such as across river or mountain or rural area, and they are ideal for temporary network setups.
However, as the digital signals have to penetrate through the permeable air, there is a reduction in speed compared to wired networks, they are less secure because cracker's laptop can act as access point. If you connected to their laptop, they'll read all your information sensitive information. They are greatly affected by their surrounding and as a consequence signal strength affected by objects blocking its path, interference, and attenuation.
Note that The use of wireless networks has resulted in a change in the way that we use computers. As wireless networks are far more easily and readily available, its easier to work from home, or from facilities such as Cafes with wi-fi connections. Also it has allowed more and more people to access the internet more regularly and in the western world, lead to internet being a cheaper, more common and widespread commodity
3.1.13 Describe the hardware and software components of a wireless network.
Hardware devices needed:
[edit | edit source]a modem
[edit | edit source]a wireless router
[edit | edit source]a wireless antennas
[edit | edit source]a wireless repeater
[edit | edit source]Wireless Network Interface Cards (NICs)
[edit | edit source]Access Points
[edit | edit source]Ethernet
[edit | edit source]...and devices that are able to connect to wireless networks.
Software devices needed:
[edit | edit source]software firewall
[edit | edit source]NIC drivers
[edit | edit source]OS
[edit | edit source]Security Software
[edit | edit source]SSID (Service Set Identifier)
[edit | edit source]DHCP (Dynamic Host Configuration Protocol)
[edit | edit source]3.1.14 Describe the characteristics of wireless networks.
Students should know the main characteristics/features of various networks (e.g.: speed of data transfer, frequencies used, range, security features, use).
Numerical values will not be asked, but students should be able to compare relatively between different types of networks. Connectivity between different locations. Networks should include: • WIfi • Worldwide interoperability for Microwave Access (WiMAX) • 3G/4G mobile • Future networks • Bluetooth • IR • Microwave.
Students should be aware of new developments/technologies that may occur during the life of this course.
Network Security
[edit | edit source]3.1.15 Describe the different methods of network security.
Different protocols are passed through different ports of a firewall. Firewalls can both protect and hide loosely administrated machines.
• Authentication (userID/password, biometrics, smart cards) • Firewall: gateway that filters traffic allowed to pass • trusted media access control (MAC) addresses (filtering): allowing only specific MAC addresses to a private network by entering them in a MAC access table in a router. Also access is controlled by allowing only specific types of network protocols to access the protected network.
3.1.16 Evaluate the advantages and disadvantages of each method of network security.
Firewalls
[edit | edit source]A firewall is a machine and its software that serve as a special gateway to a network, protecting it from inappropriate access. A firewall filters the network traffic that comes in, checking the validity of the messages as much as possible and perhaps denying some messages altogether. The main goal of a firewall is to protect (and, to some extent, hide) a set of more loosely administered machines that reside "behind" it.
A firewall enforces an organisation's access control policy. For example, a particular organisation may allow network communication only between its users and the "outside world" via email, but deny other types of communication, such as accessing websites. Another organisation may allow its users to freely access the resources of the Internet, but may not want general Internet users to be able to infiltrate its systems or gain access to its data.
Whilst the advantage of using a firewall is protection from malicious content that exists "outside" of the protected network, its major disadvantage exists with regard to the exploitation of such filtering. The entire topic with regard to censorship arises. Be it a internet service provider (ISP), an organisation, or even a government may take the opportunity to implement a firewall in order to prevent users from accessing specific content.
Data Encryption
[edit | edit source]Encryption is the process of converting ordinary text, referred to as plaintext in cryptography terminology, into a form that is unreadable, called cipher text. In its simplest terms, such implementation allows users to encrypt their data using a key and send it along a network to another node, who has access to another key which can "unlock" said data. This allows for a network-based security problem known as the "man-in-the-middle" attack to be circumvented. Network communication goes through many locations and devices as it moves from its source to its destination, usually such communication is passed along as appropriate without a problem. A man-in-the-middle attack occurs when someone has access to the communication path at some point in the network and "listens," usually with the help of a program, to the traffic as it goes by. The goal is to intercept vital information, such as a password being transmitted as part of an email message. Encryption is a method of guarding against these problems.
One disadvantage that may exist with encryption lies with its implementation. Using complex algorithms to encrypt and decrypt data may prove slow and tedious to the ordinary end-user whose ultimate goal is to access resources from alternate nodes in a network. Consequently, encrypting and decrypting may take unwelcome time. Additionally, not all nodes may have the protocol to accept an encrypted stream of data, and as such may not know what to do with the data, and only accept plaintext. As a result, the client may have to transmit unprotected data as a result of another node's failure.
