A-level Computing/CIE/Advanced Theory/Communication and Internet technologies
|
Specification link protocols
Circuit switching, packet switching and routers
Local Area Networks
|
Protocols
[edit | edit source]A protocol is a set of rules which govern how data is meant to be sent, received, transmitted, and interpreted. A collection of protocols which act together is known as a protocol suite.
The TCP/IP Protocol Suite
[edit | edit source]The Physical Layer
[edit | edit source]The physical layer is concerned with sending data through a physical medium from one device to another. Physical-layer protocols are typically low-level.
Physical-layer protocols may be subcategorised into:
- Mechanical protocols
- Protocols about the size and shape of the connector.
- Electrical/Optical protocols
- Protocols that determine which voltage levels represent the data values of 0 and 1.
- Functional protocols
- Protocols which determine what each pin of the connector is responsible for.
- Procedural protocols
- Protocols which define the sequence of actions that need to take place in order to send data.
For a given network, physical-layer protocols may determine:
- Data rate
- The number of bits to expect in a given amount of time.
- Bit synchronisation
- A method of ensuring that the sender and receiver are at the same data rate.
- Configuration
- Whether the links between systems are point-to-point or multipoint connections.
- Topology
- How the end-systems in a network are connected to one another.
- Mode
- Whether the connections are simplex (one way), half-duplex (both ways, but not at the same time), or full-duplex (both ways simultaneously).
The Data-Link Layer
[edit | edit source]The data-link layer is responsible for framing data so that it is ready to be transmitted in the physical layer. The data-link layer adds both a header and a trailer to the data coming from the network layer.
The frame header consists of the physical addresses of the source and destination devices. These physical addresses are usually Media Access Control (MAC) addresses, which uniquely identify a Network Interface Card (NIC) that is used to connect a device to the network. The frame trailer may contain an error control mechanism, such as parity checking.
When data is transmitted across a network, frames are used to bring data from one system to the next. This is known as hop-by-hop forwarding. When data is sent through many intermediate systems, each intermediate system receives a frame, removes the original frame header and trailer, frames the data with a new header and trailer for the next hop, and forwards it to the next system.
The Network Layer
[edit | edit source]The network layer is concerned with sending packets across many links in a network. Whereas the data-link layer transmits data from system to system, the network layer sends data from end to end.
To do so, the network layer adds a packet header to the data which consists of:
- The source network address
- The destination network address
- The version of the network protocol being used
The network address of a system is not to be confused with the physical address that the data-link layer uses. Each network address identifies an end-system, whereas physical addresses uniquely identify every system connected to the network.
On a large network, packets are sent from end-system to end-system via a series of intermediate systems. Each intermediate system forwards the packet from one system to the next through hop-by-hop forwarding of frames, resulting in end-to-end delivery of the packet.
The Transport Layer
[edit | edit source]The transport layer is in charge of process-to-process delivery: it makes sure the sender and receiver both know what to do with the packets being sent. It is also responsible for making sure that packets do not exceed their maximum allowable size.
The transport layer's header consists of:
- The sender port address
- The receiver port address
- The packet sequence number
- Error control information
The port addresses tell the receiver what application was responsible for sending the data and what application should be used for receiving the data. Some common examples include: the port :80, used for HTTP; the ports :20 and :21, used for FTP; and the port :25, used for SMTP.
The sequence number is used when a large message needs to be split into pieces. This will tell the receiver if all packets have been received, and what order to put the packets in to assemble the message.
Transport-layer protocols are responsible for the following:
- Process addressing and multiplexing
- Determining which process originated the message and which process should receive the message. (This is accomplished using the port addresses)
- Segment handling
- Assigning sequence numbers to packets so that the message can be reassembled at the other end.
- Connection control
- Sending control signals to establish a connection before sending data. (This applies if the protocol is connection-oriented)
- Flow control
- Ensuring that fast senders do not overwhelm slow receivers when data is sent between two different systems.
- Error control
- Detecting and correcting errors which occur during transmission.
The Application Layer
[edit | edit source]The application layer is the interface between the user and the network. It determines what the message is.
For instance, when using the application HTTP to access a website, the message is a GET request. This means that you want to GET data from the server. Thus, the message that is sent to the transport layer is GET www.example.net 1.0:
GETis the method.www.example.netis the URL of the target.1.0is the version number of the protocol being used.
Using the TCP/IP Protocol Suite
[edit | edit source]Suppose we wanted to access a website. To do so, we typically either key in the URL or click a bookmark in the browser. The application protocol, HTTP, then forms the message: GET www.example.net 1.0␍␊.
This message is then sent to the transport layer, where it will likely be handled by TCP. TCP will, if necessary, split up the message into packets, assign each packet a sequence number, then give the packets to the network-layer protocol. If the transport protocol being used is connection-oriented, the first packet is used to establish a connection before sending other packets.
In order for the network-layer protocol to send the message, it first needs to know the network address of the destination. To find this, it uses the Domain Name System (DNS) to find the address which corresponds with the URL www.example.net. Once it finds the address, it then attaches the packet header to the packets so that they end up at the correct destination.
The data-link layer sends these packets from system to system using hop-by-hop forwarding. The physical layer is where the data is actually sent.
At the server end, the first packet is received by the network-layer protocol, then forwarded to the transport layer. If a connection-oriented protocol is being used, the server will send an acknowledgement to establish the connection. Once the connection has been established, the remaining packets are sent.
The request is thus received and reassembled, so the server needs to respond to it. It sends the response to the client in much the same way the client sent the request to the server.
The BitTorrent Protocol
[edit | edit source]The BitTorrent Protocol is a way of sharing files in a decentralised peer-to-peer model, as opposed to the traditional, more centralised, client and server model.
Whereas the client and server model has clients downloading files from a central server, the BitTorrent protocol has a swarm of peers who provide regular uploads and downloads for each other. This has the advantage of preventing a single device from being overwhelmed, as all devices share with only a few others.
In order to use BitTorrent, a peer loads a .torrent file into a BitTorrent client, which provides a connection to a tracker. The tracker is a device which keeps a list of peers connected to the tracker and keeps track of which peers have which chunks of what files. The tracker does not store files, it only keeps track of them. Periodically, peers will update the tracker so that they are not sent chunks that they already have.
A peer that has all of the chunks of a desired file is a seed. Seeds distribute chunks of the file to peers that do not have all of the file. Once a peer obtains every chunk of the file, it becomes a new seed, and can then send more chunks to other peers. To ensure that the speed of downloads is high, rarer chunks are prioritised.
The main advantage of using BitTorrent is that it scales well. If you have thousands of people trying to download a file from the same server, that server may become overwhelmed and crash, which slows down the speed of downloads; whereas with BitTorrent, a larger swarm can actually result in faster downloads.
Application Layer Protocols
[edit | edit source]HyperText Transfer Protocol (HTTP)
[edit | edit source]HTTP is a request-response protocol for transferring webpages across the internet. It is based on the client-server architecture. There are two main methods associated with HTTP: GET & POST.
GET is for retrieving data from a server.
POST is for putting data into a server's database
File Transfer Protocol (FTP)
[edit | edit source]FTP is a protocol for transferring files in a client-server architecture. An FTP server hosts files, and clients can upload, download, or remove files if they have permission.
Mail protocols (SMTP & POP3)
[edit | edit source]The Simple Mail Transfer Protocol (SMTP) is for sending mail to a mail server, and Post Office Protocol version 3 (POP3) is for receiving mail from a mail server.
There is another mail protocol, the Internet Message Access Protocol (IMAP), which is sometimes used in place of POP3, and serves roughly the same function.
However, it is common for mail to be sent and received using other protocols, such as HTTP. SMTP is still used for moving mail between mail servers.
Circuit Switching, Packet Switching, & Routers
[edit | edit source]Circuit Switching
[edit | edit source]Circuit switching is where a connection across the network is a dedicated link that lasts for the duration of the transmission. This is how phone calls tend to operate: a phone is connected to a switching station, either by a landline or by radio transmissions; that switching station is connected to other switching stations; the final switching station is connected to the phone of the person you are contacting.
In a circuit-switched system, all data is transmitted from node to node across the same connections. This means that for the duration of the communication, those links cannot be used by other data.
Packet Switching
[edit | edit source]Packet Switching is where the data is transmitted without establishing a circuit, but by splitting the message into packets before sending it. Each packet travels through the network in its own path to the destination.
The main advantage of circuit switching is that packets can be routed along the most efficient path to their destination, which makes the transmission faster as data is not forced into slow or high-traffic connections.
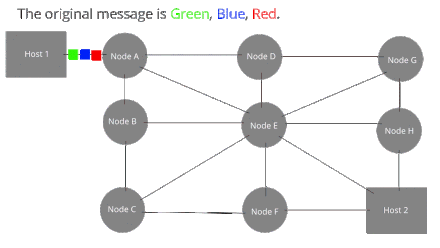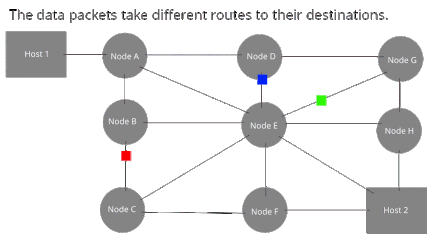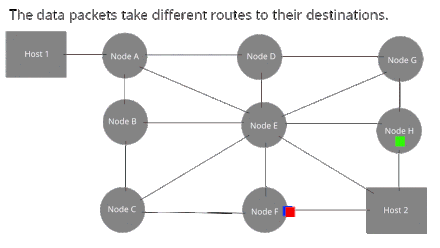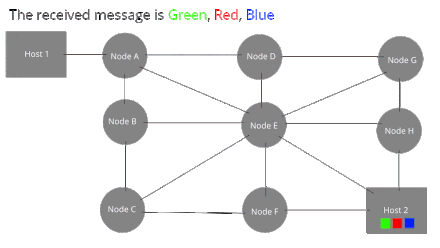
Local Area Networks
[edit | edit source]Bus topology networks
[edit | edit source]
A bus topology network is where all systems have a multipoint connection with a common backbone cable. There is no direct connection between any two end-systems.
Advantages
[edit | edit source]- It requires minimal cable length
- New systems can easily be added
- A bus topology has a simple and reliable architechture
Disadvantages
[edit | edit source]- Data collisions are more likely, resulting in data loss
- A divide in the backbone cable affects the entire network
- It is difficult to isolate faults in a bus network
Star topology networks
[edit | edit source]
A star topology network consists of a central device that all end-systems are connected to.
Advantages
[edit | edit source]- It is easy to add new devices to a star network.
- Security software (e.g. Firewalls) can be stored on the central device rather than on each individual end-system.
- If one node or connection fails, it does not affect other connections.
Disadvantages
[edit | edit source]- A star network needs a cable for every device which is connected to it.
- If the central device fails, the whole network fails.
- Extra hardware (e.g. hubs, switches, servers) is necessary to build the star network, raising costs.
Wireless networks
[edit | edit source]Wireless networks are, unsurprisingly, networks that don't have wires. Wireless networks instead use electromagnetic radiation to transmit information.
Bluetooth
[edit | edit source]Bluetooth is a protocol for transmitting information using short-range radio waves. Bluetooth is an ad hoc network: there is no defined infrastructure, and connections are made spontaneously. Bluetooth is commonly used for simple applications, such as using a wireless keyboard or mouse.Bluetooth devices contain small , low power radio transmitters and receivers. When devices are in a range of other bluetooth devices, they detect each other and can be paired or connected in order to share data or connect hardwares to a computer.
WiFi
[edit | edit source]WiFi is a wireless LAN protocol that uses radio waves to transmit data. Commonly, WiFi networks are centred on a wireless access point, a device which communicates wirelessly with nearby devices to connect them to the internet, and thus are not ad hoc.
WiMAX
[edit | edit source]WiMAX (Worldwide Interopreability for Microwave Access) is a wireless WAN protocol. It uses microwaves, rather than radio waves, to transmit data without having to lay underground cables. This allows data transmission in remote areas that would otherwise need a large amount of cable to reach.
Cellular networks
[edit | edit source]
A cellular network is a network that covers a large geographic area using cells. At the centre of each cell is a base station. A wireless device can connect to a base station of a given frequency using wireless signals. Adjacent cells have different frequencies so that they do not interfere with one another. Non-adjacent cells can use the same frequency.
LAN hardware
[edit | edit source]Network Interface Card (NIC)
[edit | edit source]A network interface card is a necessary component for connecting a system to a network. It allows the system to interface with the network, and uniquely identifies the system using a MAC address.
Hub
[edit | edit source]A hub is an obsolete physical-layer device that broadcasts all of the data sent to it to every device on the network. Hubs were made obsolete by the introduction of switches and routers.
Bridge
[edit | edit source]A bridge is a connector between two networks. It sends data from one network to the other only if the data is intended for a recipient in the other network. Bridges were made mostly obsolete by the introduction of switches and routers.
Switch
[edit | edit source]A switch is a data-link layer device which sends data from its source to its intended recipient. A switch does so using the MAC address of the recipient which is noted in the frame header of the message.
Router
[edit | edit source]A router is a network-layer device which sends data through a network along the most efficient possible route. A router can analyse network traffic and pick the route with the least traffic to send the data through.
CSMA/CD
[edit | edit source]Carrier Sense Multiple Access with Collision Detection is a collision-detection protocol used with Ethernet connections. It works by monitoring the voltage of the wire at all times. If a frame is being transmitted on the wire, there will be a voltage change on the wire.
If a frame is being transmitted while another system is trying to send a frame, a jam signal is sent down the wire, which tells both sides to wait for a random amount of time before sending the next frame. This ensures that there won't be a collision when sending the next frame.
CSMA/CD is only used on half-duplex links between systems. On full-duplex and simplex links, it is unnecessary.
