Communication Systems/Time-Division Multiplexing
Consider a situation where there are multiple signals which would all like to use the same wire (or medium). For instance, a telephone company wants multiple signals on the same wire at the same time. It certainly would save a great deal of space and money by doing this, not to mention time by not having to install new wires. How would they be able to do this? One simple answer is known as Time-Division Multiplexing.
Time Division Multiplexing
[edit | edit source]Time-Division Multiplexing (TDM) is a convenient method for combining various digital signals onto a single transmission media such as wires, fiber optics or even radio. These signals may be interleaved at the bit, byte, or some other level. The resulting pattern may be transmitted directly, as in digital carrier systems, or passed through a modem to allow the data to pass over an analog network. Digital data is generally organized into frames for transmission and individual users assigned a time slot, during which frames may be sent. If a user requires a higher data rate than that provided by a single channel, multiple time slots can be assigned.
Digital transmission schemes in North America and Europe have developed along two slightly different paths, leading to considerable incompatibility between the networks found on the two continents.
BRA (basic rate access) is a single digitized voice channel, the basic unit of digital multiplexing.
North American TDM
[edit | edit source]The various transmission rates are not integral numbers of the basic rate. This is because additional framing and synchronization bits are required at every multiplexing level.
In North America, the basic digital channel format is known as DS-0. These are grouped into frames of 24 channels each. A concatenation of 24 channels and a start bit is called a frame. Groups of 12 frames are called multiframes or superframes. These vary the start bit to aid in synchronizing the link and add signaling bits to pass control messages.
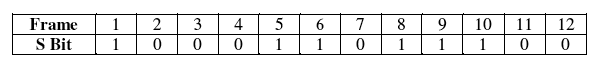
S Bit Synchronization
[edit | edit source]The S bit is used to identify the start of a DS-1 frame. There are 8 thousand S bits per second. They have an encoded pattern, to aid in locating channel position within the frame.
This forms a regular pattern of 1 0 1 0 1 0 for the odd frames and 0 0 1 1 1 0 for the even frames. Additional synchronization information is encoded in the DS-1 frame when it is used for digital data applications, so lock is more readily acquired and maintained.
For data customers, channel 24 is reserved as a special sync byte, and bit 8 of the other channels is used to indicate if the remaining 7 bits are user data or system control information. Under such conditions, the customer has an effective channel capacity of 56 Kbps.
To meet the needs of low speed customers, an additional bit is robbed to support sub-rate multiplexer synchronization, leaving 6 x 8 Kbps = 48 Kbps available. Each DS-0 can be utilized as:
- • 5 x 9.6 Kbps channels or
- • 10 x 4.8 Kbps channels or
- • 20 x 2.48 Kbps channels.
In the DS-2 format, 4 DS-1 links are interleaved, 12 bits at a time. An additional 136 Kbps is added for framing and control functions resulting in a total bit rate of 6.312 Mbps.
Signaling
[edit | edit source]Signaling provides control and routing information. Two bits, called the A and B bits, are taken from each channel in frames 6 and 12 in the multiframe. The A bit is the least significant bit in each channel in frame 6, and the B bit is the least significant bit in each channel in frame 12. This provides a signaling rate of 666 2/3 bps per channel.
The quality of voice transmission is not noticeably affected when 2% of the signal is robbed for signaling. For data, it may be a different story. If the data is encoded in an analog format such as FSK or PSK, then robbing bits is of no consequence, but if the data is already in digital form, then robbing bits results in unacceptable error rates. It is for this reason that in North America, a 64 Kbps clear channel cannot readily be switched through the PSTN. This means that data customers are limited to 56 Kbps clear channels. This simple condition has a profound effect on the development of new services such as ISDN. In most facilities, the A and B bits represent the status of the telephone hook switch, and correspond to the M lead on the E&M interface of the calling party.
ESF
[edit | edit source]CCITT has modified the North American digital hierarchy for the deployment of ISDN, by means of recommendation G.704. ESF consists of 24 DS-0 channels in a frame, but groups them into a 24-frame multiframe instead of the usual 12-frame multiframe.
The S bit is renamed the F bit, but only 1/4 of them are used for synchronization. This is possible because of improvements in frame search techniques and allows more signaling states to be defined.
Bit robbing is still used for signaling over an ESF link, but with the advent of ISDN, it will not be permitted. Instead, channel 24 is used to support a D channel.
Typical T1 CPE Application
[edit | edit source]The large telecom carriers are not the only ones who deploy high-speed TDM facilities. In many cases, heavy users of voice or data services can reduce their transmission costs by concentrating their numerous low speed lines on to a high speed facility.
There are many types of T1 multiplexers available today. Some are relatively simple devices, while others allow for channel concatenation, thus supporting a wide range of data rates. The ability to support multiple DS-0s allows for easy facilitation of such protocols as the video teleconferencing standard, Px64.
Multiplexers
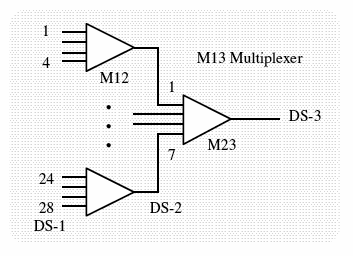
[edit | edit source]Multiplexing units are often designated by the generic term Mab where a is input DS level and b is the output DS level. Thus, an M13 multiplexer combines 28 DS–1s into a single DS–3 and an M23 multiplexer combines 7 DS–2s into a single DS–3.
ZBTSI
[edit | edit source]ZBTSI (zero byte time slot interchange) is used on DS–4 links. Four DS-1 frames are loaded into a register, and renumbered 1–96. If there are any empty slots [all zeros], the first framing bit is inverted and all blank slots are relocated to the front of the frame. Channel 1 is then loaded with a 7-bit number corresponding to the original position of the first empty slot. Bit 8 used to indicate whether the following channel contains user information or another address for an empty slot.
If there is a second vacancy, bit 8 in the previous channel is set, and the empty slot address is placed in channel 2. This process continues until all empty positions are filled.
The decoding process at the receiver is done in reverse. Borrowing 1 in 4 framing bits for this system is not enough to cause loss of synchronization and provides a 64 Kbps clear channel to the end-user.
European TDM Carriers
[edit | edit source]European systems were developed along slightly different principles. The 64 Kbps channel is still the basic unit, but signaling is not included in each channel. Instead, common channel signaling is used. In a level 1 carrier, channels 0 and 16 are reserved for signaling and control. This subtle difference means that European systems did not experience the toll fraud and 56 k bottlenecks common to North American systems, and they experience a much larger penetration of ISDN services.
Zero Substitutions
[edit | edit source]In order to prevent transmission systems from loosing lock on the data stream, it is necessary to avoid long strings of zeros. One of the most effective ways of doing this is to replace the zeros with a predetermined code. This substitution must be done in such a way that the receiver can identify it and strip it off before passing the data stream to the client.
AMI provides a simple means of detecting substitutions. In the normal course of events, alternate marks are inverted. Therefor, deliberately inducing a bipolarvariation at the transmitter can alert the receiver of a substitution. However, a single violation is indistinguishable from a transmission error. Consequently, some additional condition must also occur.
There are two common methods to create a second condition:
- · Create a second bipolar violation in the opposite direction, within a specified time. This has the effect of keeping the average signal level at zero.
- · Count the number of marks from the last substitution to predict the next type of violation
B6ZS
[edit | edit source]B6ZS (binary six zero substitution) is used on T2 AMI transmission links.
Synchronization can be maintained by replacing strings of zeros with bipolar violations. Since alternate marks have alternate polarity, two consecutive pulses of the same polarity constitute a violation. Therefore, violations can be substituted for strings of zeros, and the receiver can determine where substitutions were made.
Since the last mark may have been either positive (+) or negative (-), there are two types of substitutions:
These substitutions force two consecutive violations. A single bit error does not create this condition.
B8ZS
[edit | edit source]This scheme uses the same substitution as B6ZS.
B3ZS
[edit | edit source]B3ZS is more involved than B6ZS, and is used on DS–3 carrier systems. The substitution is not only dependent on the polarity of the last mark, but also on the number of marks since the last substitution.
HDB3
[edit | edit source]HDB3 (high density binary 3) introduces bipolar violations when four consecutive zeros occur. It can therefore also be called B4ZS. The second and thirds zeros are left unchanged, but the fourth zero is given the same polarity as the last mark. The first zero may be modified to a one to make sure that successive violations are of alternate polarity.
HDB3 is used in Europe. Violation, or V pulses are injected after three consecutive zeros. The fourth zero is given the same polarity as the last mark. In the event of long strings of zeros occurring, a succession of single polarity pulses would occur, and a dc offset would build-up.
To prevent this, the first zero in a group of 4, may be modified to a 1. This B or balancing pulse assures that successive violations are of alternate polarity.
Block Code Substitution
[edit | edit source]These schemes operate on bytes rather than a bit at a time. Some transmit the signal as binary levels, but most use multi-level pulses. Some authors categorize these as line codes.
A binary block code has the designation nBmB, where n input bits are encoded into m output bits. The most common of these is the 3B4B code.
In Europe 4B3T, which encodes 4 binary bits into 3 ternary levels, has been selected as the BRA for ISDN. In North America, 2B1Q which encodes 2 binary bits into 1 quaternary level has been selected for BRA.
Some block codes do not generate multilevel pulses. For example, 24B1P or 24B25B simply adds a P or parity bit to a 24 bit block.
Benefits of TDM
[edit | edit source]TDM is all about cost: fewer wires and simpler receivers are used to transmit data from multiple sources to multiple destinations. TDM also uses less bandwidth than Frequency-Division Multiplexing (FDM) signals, unless the bitrate is increased, which will subsequently increase the necessary bandwidth of the transmission.
Synchronous TDM
[edit | edit source]Synchronous TDM is a system where the transmitter and the receiver both know exactly which signal is being sent. Consider the following diagram:
Signal A ---> |---| |A|B|C|A|B|C| |------| ---> Signal A Signal B ---> |TDM| --------------> |De-TDM| ---> Signal B Signal C ---> |---| |------| ---> Signal C
In this system, starting at time-slice 0, every third time-slice is reserved for Signal A; starting at time-slice 1, every third time-slice is reserved for Signal B; and starting at time-slice 2, every third time-slice is reserved for Signal C. In this situation, the receiver (De-TDM) needs only to switch after the signal on each time-slice is received.
The data flow of each input connection is divided into units where each input occupies one input time slot. Each input connection has a time slot alloted in the output irrespective of the fact whether it is sending data or not.
A -----|A3|A2|A1|---> |---| .............|C3|B3|A3|C2|B2|A2|C1|B1|A1| |------| ---> A
| | | | | | |
B -----|B3|B2|B1|---> |MUX| -------------|--------|--------|----------> |De-MUX| ---> B
| | | | | | |
C -----|C3|C2|C1|---> |---| | | | |------| ---> C
<--> <-------->
Bit Interval Frame (x seconds)
Sync TDM is inefficient when one or more input lines have no data to send. Thus, it is used with lines with high data traffic.
Sampling rate is same for all signals. Maximum sampling rate = twice the maximum frequency all the signals.
Statistical TDM
[edit | edit source]Synchronous TDM is beneficial because the receiver and transmitter can both cost very little. However, consider the most well-known network: the Internet. In the Internet, a given computer might have a data rate of 1kbps when hardly anything is happening, but might have a data rate of 100kbps when downloading a large file from a fast server. How are the time-slices divided in this instance? If every time slice is made big enough to hold 100Kbps, when the computer isn't downloading any data, all of that time and electricity will be wasted. If every time-slice is only big enough for the minimum case, the time required to download bigger files will be greatly increased.
The solution to this problem is called Statistical TDM, and is the solution that the Internet currently uses. In Statistical TDM, each data item, known as the payload (we used time-slices to describe these earlier), is appended with a certain amount of information about who sent it, and who is supposed to receive it (the header). The combination of a payload and a header is called a packet. Packets are like envelopes in the traditional "snail mail" system: Each packet contains a destination address and a return address as well as some enclosed data. Because of this, we know where each packet was sent from and where it is going.
The downside to statistical TDM is that the sender needs to be smart enough to write a header, and the receiver needs to be smart enough to read the header and (if the packet is to be forwarded,) send the packet toward its destination.
Link Utilization
[edit | edit source]Statistical multiplexing attempts to maximize the use of a communication path. The study of this is often called queuing theory. A queue is simply a line of customers or packets waiting to be served. Under most circumstances, the arrival rate is unpredictable and therefor follows a random or Poisson distribution pattern, whereas the service time is constant.
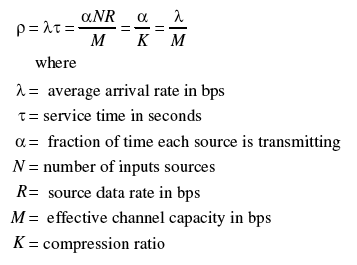
The utilization or fraction of time actually used by a packet multiplexing system to process packets is given by:
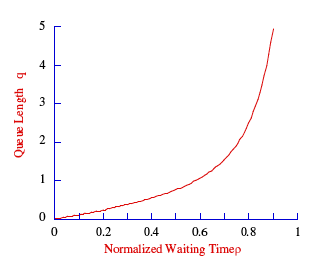
The queue length or average number of items waiting to be served is given by:
- Example
- A T1 link has been divided into a number of 9.6 Kbps channels and has a combined user data rate of 1.152 Mbps. Access to this channel is offered to 100 customers, each requiring 9.6 Kbps data 20% of the time. If the user arrival time is strictly random find the T1 link utilization.
- Solution
- The utilization or fraction of time used by the system to process packets is given by:
- A 24 channel system dedicated to DATA, can place five 9.6 Kbps customers in each of 23 channels, for a total of 115 customers. In the above statistical link, 100 customers created an average utilization of 0.167 and were easily fitted, with room to spare if they transmit on the average 20% of the time. If however, the customer usage were not randomly distributed, then the above analysis would have to be modified.
This example shows the potential for statistical multiplexing. If channels were assigned on a demand basis (only when the customer had something to send), a single T1 may be able to support hundreds of low volume users.
A utilization above 0.8 is undesirable in a statistical system, since the slightest variation in customer requests for service would lead to buffer overflow. Service providers carefully monitor delay and utilization and assign customers to maximize utilization and minimize cost.
Packets
[edit | edit source]Packets will be discussed in greater detail once we start talking about digital networks (specifically the Internet). Packet headers not only contain address information, but may also include a number of different fields that will display information about the packet. Many headers contain error-checking information (checksum, Cyclic Redundancy Check) that enables the receiver to check if the packet has had any errors due to interference, such as electrical noise.
Duty Cycles
[edit | edit source]Duty cycle is defined as " the time that is effectively used to send or receive the data, expressed as a percentage of total period of time." The more the duty cycle , the more effective transmission or reception.
We can define the pulse width, τ, as being the time that a bit occupies from within its total alloted bit-time Tb. If we have a duty cycle of D, we can define the pulse width as:
Where:
The pulse width is equal to the bit time if we are using a 100% duty cycle.