Ethical Hacking and Penetration Testing
| A Wikibookian suggests that this book or chapter be merged into Hacking. Please discuss whether or not this merge should happen on the discussion page. |
Author:Tinashe
We are living in a digital world. A world where people are becoming more trustworthy to technology. But then the truth is that the more we are able to improve our technology, the more the new technology becomes vulnerable. Pretty much everyone has access to a smartphone or personal computer(PC). The question on everyone's mind should be "Am I safe". We tend to use a smartphones without even thinking whether someone is lurking through the phones camera or something. We are living in a world where hacking has become part of our open lives
Types of Hackers
[edit | edit source]Believe it or not but hackers are actually divided into groups but specifically now we will look into the basic ones. Hackers as shown below have different things that they do depending on their motives
| Type of hacker | Example | Description | |
|---|---|---|---|
| Black hat hackers |
|
These are the cyber criminals who only hack for their own malicious and personal gain. | |
| White hat hackers |
|
These are the good guys who hack in order to detect vulnerabilities in order for them to be patched, these are basically the hackers that make the internet a better place. | |
| Grey hat hackers |
|
These are the people that are somewhere between Black hats and white hats. |
Teams used in hacking
[edit | edit source]In Ethical hacking we have different types of teaming. This would specifically describe the two sides in which hacking is performed, which is either as a threat or as a defence. Below are the two teaming used in Ethical hacking.
| Team Name | Description | ||
|---|---|---|---|
| Red Team | These are known as the offender's of security or the attackers | ||
| Blue Team | These are the defenders of security | ||
Information Gathering
[edit | edit source]Information Gathering refers to the collection of raw data on a certain target individual or system. This is done by collecting public information and scanning the system thus far receiving data and information about the target. For example if an information gathering scan technique was to be performed on the Microsoft web domain, it would reply back with information like the operating system that the domain runs on.
Types of methods used in information gathering
[edit | edit source]In information gathering many methods are used, but each method used will result in different type of information being retrieved. Below are some examples of them
Whois
[edit | edit source]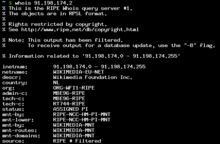
In particular WHOIS is a type of GET script used to retrieve information on specific target domain. WHOIS can be done to retrieve information like, finding the owner of a specific domain and probably more
Nmap and Zenmap scanning
[edit | edit source]Nmap scanning is one great example of information gathering, it's known to be the most commonly used. Nmap is an application that was built for information gathering and footprinting. Nmap was created to be a CLI application ( command line application)
Nmap comes with a GUI (Graphic users interface) called zenmap which is specifically created for those who find it a bit intense using the CLI end of the app.


