Introduction to Computer Information Systems/Computer Networks
Networking Applications
[edit | edit source]
There are many different types of network applications. First and foremost is the internet, the largest network of networks in the world. Second, there are our phones, the oldest of which is POTS (plain old telephone service), which one day could be replaced by the newer technology, mobile phones. Mobile phones have been around for a few years now, and are beginning to replace home phone lines. Mobile phones can be separated into two groups, cellular phones and satellite phones. Cell phones work by communicating with cell towers in order to function. There are some dual mode phones which allow you to make phone calls through a WIFI signal, and switch to cell signal when out of WIFI range. Satellite phones work by communicating with satellites in space, this is primarily used with the military, where cell tower coverage is nearly impossible in some locations. While satellite phones can be used in rural and mountainous areas, the drawback to them is when there is a storm or heavy clouds, you can lose your signal. Satellites are also used with a GPS(global positioning system). GPS functions by transferring data between your device and satellites in space. They work similarly to sonar waves. After the signal leaves the satellite, your exact location will be determined based on the time it takes to get to you.
In addition to tracking subjects, satellites and networks are beginning to play a larger part in the field of search and rescue (SAR). Most ocean going boats and all airplanes carry some kind of emergency beacon on board. Aircraft carry an emergency location transmitter (ELT) and boats carry an emergency position-indicating radio beacon (EPIRB). Before the mid 2000’s these devices transmitted on 121.5 mhz, the international emergency frequency, which was monitored by SAR satellites. However, in 2009 [1], SAR satellites stopped monitoring 121.5 beacons in favor of the newer 406 mhz beacons. These devices guide SAR team to the site of a crash, but the signal is also embedded with data. This data includes the name of the owner of the beacon, the aircraft or vessel identification, and a precise GPS location. These capabilities are also being used on personal locator beacons (PLB). These devices are small enough to carry in a pocket, but powerful enough to send an emergency signal to a satellite. Hikers can use these if they are going to a remote area. The use of a satellite network allows for very precise tracking of these devices, and can bring rescue team to the site within two hours.

Computer networks consist of two or more computers or hardware devices linked together to enable connections between shared hardware, software, and data. A combination of networks that consist of telephone networks and computer networks are also becoming more commonly used in this generation.[2] The data is able to be passed along to other networks due to networked computing devices along data connections. A datagram, segment, or block is a unit of communication over a digital network, commonly known as a packet. The data breaks down into smaller units of data when needed. Once the data travels along the data connections, the pieces of data are reassembled into the original data chunk. Data is structured differently, depending on the protocol enforcing the data. The structure of a packet consists of a header and a payload. The header consists of titles regarding transmission-related information. The payload, however, consists of the actual data the packet is carrying.[3] Computer networks range from small private networks, to large computer networks. The Internet, or the World Wide Web, is the largest computer network, consisting of a system of interlinked hypertext documents accessed via the Internet. Via hyperlinks, a user of the Internet can access images, text, videos, etc.
Monitoring Systems are another form of networking applications. These systems specialize in locating a specific person, vehicle or device rather than pulling up geographical information like a GPS does. However, most monitoring systems use GPS in locating their targets. Radio Frequency Identification (or RFID) for example, can be used to locate a person or animal with an RFID chip embedded inside of it. Most commonly recognized for its ability to track pets that have the chip implanted, RFID has also moved into the human medical field. In fact, some breast implants in the United Kingdom have been chipped so that a physician can read information about the implant years after the surgery has been completed.[4] While this is the social reasoning for this type of chipping, it seems that medical records housed on inexpensive servers would suit this purpose just fine. The fact remains that RFID chips, which are about the size of a grain of rice, operate using a small silicon chip and a copper antenna which emit personal information about its owner. This information is then picked up by electronic networks feeding back information about the product, the person carrying it, and its location to the network. It is currently being used to track cattle and Alzheimer's patients as well as merchandise produced by manufacturers.[5] Other monitoring systems include vehicle tracking software such as the famous OnStar. This type of networking application has been expanded so that employers can spy on employees using company vehicles. With a simple installation, the latest vehicle tracking applications can feed information about the geographic location of a company vehicle, the speed of the vehicle, and even "hard breaking" events. Mobile phones aren't omitted either. Since most of the current mobile phones have stand alone GPS systems a person can track the movements of the individuals under their plan as well as their own phone if it is stolen.[6]

Multimedia networking has exploded as well. This type of networking offers digital multimedia content such as movies, music, and recorded t.v. shows to be viewed over a phone, p.c., or television. While most devices already have the required capabilities built in, some devices need may need a receiver. Placeshifting is common with this type of network which will allow an individual to download content from one place and view it in another, i.e. from a t.v. to a mobile phone. Similarly, VideoConferencing allows people to interact remotely from separate locations. Instead of streaming a movie in real time, a person can stream a video feed from a relative or business part who might be across the globe. They can then interact and speak as they normally would while viewing the mannerisms of others in real time. Also, through the use of videoconferencing Telemedicine has been used to diagnose and treat patients who are unable to access a doctor in person because of their poverty level, geographical area, or physical condition. Physicians, with the assistance of a member on site with the patient, use videoconferencing to conduct tests such as simple ear and throat checkups to procedures as complex as actual surgery in some cases.[7]
One relatively new use of networking is telesurgery, or remote surgery. As the name implies, this is surgery that takes place over distances: that is, the surgeon is not actually in the same room as the patient. A surgeon controls robotic arms that in turn perform surgery on the patient. Some advantages of this kind of procedure are that it mitigates the potential effect of a surgeon's hands shaking, the surgeon's arms rest comfortably throughout the entire procedure, and the surgeon can specify a task that (s)he wishes to have performed and ensure it is safe before the robotic arms actually carry it out. Initially, there was just computer-assisted surgery, where the surgeon sat only a few meters away, but now longer-distance telesurgery has been developed: the first telesurgical procedure was known as Operation Lindbergh and involved a New York doctor performing on a French patient across the Atlantic. Telesurgery still isn't especially widespread, but in time, it may see such uses as performing on astronauts in long-term space travel, performing on soldiers on or near battlefields, or working alongside or training surgeons in remote, developing countries. Time will tell how useful these kinds of procedures turn out to be, but they are definitely an example of a networking technology that would have been unthinkable just a few decades ago.[8]
Network Characteristics
[edit | edit source]Networks can contain many different characteristics that define how they function as well as their capabilities. These characteristics include certain factors such as topology, scalability or size, architecture, and media.[9]
Network Topology
[edit | edit source]
Network topology is how different nodes in a network are connected to each other and how they communicate. The five most common topologies are mesh topology, star topology, bus topology, ring topology, and tree topology. In a mesh topology, devices are connected with many excessive interconnections between network mode. In a star topology, the devices are connected to a central computer, and the nodes communicate across the network by passing data through the hub, which is the central computer. In a bus topology, it connects all devices on a local-area network called LAN. Bus networks are not very pricey, and they are easy to install. In a ring topology, it consists of a local area network whose topology is a ring. The messages travel around the ring. In a tree topology, it is considered a "hybrid" topology that combines characteristics of the bus and star topologies.[10]
Network Architecture
[edit | edit source]
Network architecture is the layout of the network. The hardware, software, communication protocols, and mode of transmission in the network architecture.[11] Two main types of network architectures are server-based, or client-server networks, and peer-to-peer (P2P) networks. Server-based networks consist of clients and servers. Servers are powerful computers that are able to transfer data and information among personal computers within the local network or even to other computers across the Internet.[12] Some server-based networks can be designed for certain purposes such as to connect all computers within a given area to a printer (print server) or to even contain data such as documents or other types of files (file server). A peer-to-peer network is a network that doesn’t utilize a central server. Instead, each computer (or peer) within a peer-to-peer network allows itself to use some of its resources to share with the entire network. For example, computers can give some of their processing power or bandwidth and share it with the network participants.[13] The network architecture plays an essential role in today's society; therefore, one should be aware of the network architecture, and the different types of network topologies as well.
Network Size
[edit | edit source]Network sizes are defined by a few three-letter acronyms: PANs, LANs, MANs, and WANs. Personal Area Networks (PANs) are networks that connect an individual's devices, such as bluetooth headsets and speakers. Local Area Networks (LANs) are networks that are used within larger areas such as corporate buildings but can also be used in hospitals or even college campuses. Some people, however, prefer to title networks on a college campuses and hospitals as Campus Area Networks (CANs) if they contain more than one LANs interconnected. A Metropolitan Area Network (MAN) is used to connect computers within cities. Lastly, a Wide Area Network (WAN) is a network that contains numerous LANs and is able to connect computers across continents. The largest Wide Area Network is the Internet. Some people use other terms such as Global Area Network (GAN) which is a single network with connection points across the globe, usually used to connect large corporation, or Solar System Area Network (SSAN), which is numerous GANs, combined to connect planets within a single solar system. This technology, however, is not yet available.[14]
Network Media
[edit | edit source]Network media is the actual path which the signals travel to and from different components. These paths can either be physical wires, wired media, or radio signals, wireless media.[15]
Wired Networking Media
[edit | edit source]The wire used for networking media is called cable. The most common types of wired media include twisted-pair, coaxial, and fiber-optic cable.[16]
Twisted-Pair Cable
[edit | edit source]Twisted-pair cable is exactly what it sounds like: two wires twisted together. This design works because it creates an electrical current that flows through the wire, which creates a circular magnetic field around the wire that increases performance. Having the wires twisted, as opposed to being adjacent, helps there to be no crosstalk (the noise/interference sometimes generated by the wires). There are two sub-types of twisted-pair cable: unshielded twisted pair (UTP) and shielded twisted pair (STP). Twisted-pair cable is most used for LANs such as telephone communication.[17]

Coaxial Cable
[edit | edit source]Coaxial cable is made of three components: the inside wire, the insulation, and the outside shield. The inside wire is made of two conducting elements, mainly copper and covering this is the layer of flexible insulation. A second layer of woven (braided) copper or metallic foil that acts as a second wire and as a shield that reduces that amount of outside interference. Lastly, there is a cable jacket to cover the second wire.[18]
Fiber-optic Cable
[edit | edit source]Fiber-optic cable is made of hundreds of clear glass or plastic fiber strands that are the size of a human hair. Data is transferred by light pulses at speeds of billions of bits per second. This is the newest and fasted type of cable, and while it is the most expensive, it is starting to replace the other types because its high-speed advantages are considered to be worth it.[19] They provide higher bandwith and can transmit data over longer distances than wired cables. They are also less susceptible to interference and doesn't require special shielding to avoid it. Also, since fiber-optic cables use light to transmit information, they lessen the need for signal boosters; light can travel longer distances without losing strength.
Wireless Networking Media
[edit | edit source]
Along with wired networks, there are also wireless networks. Wireless networks are networks that use radio signals to transmit data through the air in order for two or more devices to communicate, rather than physical cables. This gives people the opportunity to use e-mail or browse the internet from almost any location, provided there is a wireless network available. Many devices today are able to use this technology such as PCs, laptops, mobile devices, servers and printers. Wireless networks can be found almost everywhere including the home and public locations such as libraries, restaurants, coffeehouses and airports. Many people needing Internet access on the go will commonly take advantage of wireless hotspots. A wireless hotspot is a small range area with a usable connection that allows access to the internet.
There are also different types of wireless networks. Wireless Local Area Networks (WLANS) are networks that give access to the Internet to a small local area such as a college or library. Wireless Personal Area Networks (WPANS) allow connectivity of devices in smaller ranges, typically around 30 feet. This includes Infra Red technology which may be in a television remote, or Bluetooth. A Wireless Metropolitan Area Network (WMANS) allows for the connection of many networks in a metropolitan area such as in high-rises or big buildings. Wireless Wide Area Networks (WWANS) are networks that spread over much larger areas such as cities or countries and are available through the use satellite systems or antenna sites.
Wired Vs. Wireless Networking Media
[edit | edit source]
While the world may be going towards a wireless route when it comes to networking, is it really the best direction when it comes to connectivity? Let’s break it down to the benefits and disadvantages of each type of network media.
The benefits of having wired connection are that it it’s secure, reliable, and fast. They are also very much cheaper than having wireless connections. Another perk, especially for businesses or enterprises, is that wired connections can be controlled. This has security and productivity benefits. Disadvantages of wired connection are the sacrifice of space and portability or mobility, as well as actual physical safety and maintenance.[20]

The benefit of having a wireless connection is the actual lack of cables. This gives the actual physical freedom to use personal and office devices and has the advantage of a tidier environment. However, there is also a downside in terms of security, speed and reliability.
The best combination might be a system that has some wired connections and some wireless connections. Having a hybrid environment can balance out the disadvantages and take advantage of the benefits of having two types of network media.[21]
Types of Cables
[edit | edit source]There are different types of cables. The cable that connects a computer or network to a server or router or modem is called an Ethernet cable. The evolution of Ethernet cables began with the apparent that coaxial cables could not keep up with the demands of a growing and evolving network. The cables are listed in categories or "Cat" for short. The Cat 1 cables were primarily used for telephone modems and had a data transfer rate of up to 1Mbps. Cat 2,3,and 4 can all support computer networks and telephone traffic, and have maximum capacities of 4Mbps, 10Mbps, and 16Mbps respectively. When these cables are taken out of their casing, they look very similar. The same wires are present in all types of Cat cables; however, the number of wraps per inch increase in each version of Cat cables, therefore decreasing the amount of electromagnetic interference in the signal being transfered. The introduction to Cat 5 revolutionized networking because Cat 5 became the standard and it was classed as "ethernet" which means that it has the capability for high speed and high capacity data transfers (of 10Mbps - 100Mbps), as well as the ability regulate the transfers in order to prevent simultaneous transfers which would cancel out. After Cat 5, Cat 5e was introduced. The "e" stands for "enhanced". The Cat 5e "gigabit" cable - in theory - had the capacity for 1000Mbps (1 gigabit) transfer rates. This was accomplished by wrapping the strands of wire tighter, therefore cutting down on "crosstalk" or interference that caused disruptions in the data transfer. Later, Cat 6 was introduced with the addition of a physical isolator between line segments in the cable, which reduces interference to a greater extent, with a transmission capacity of 1000 Mbps (1 Gigabit per second).[22] Since 2013, Cat 7,8, and 8.1 have been introduced, but are only practical in a small amount of industrial settings.

Network Architecture & Network Topologies
[edit | edit source]
Network architecture is the layout of the network. The hardware, software, communication protocols, and mode of transmission consists in the network architecture. The network architecture plays an essential role in today's society; therefore, one should be aware of the network architecture, and the different types of network topologies as well.[23] Network topology is how different nodes in a network are connected to each other and how they communicate. The five most common topologies are mesh topology, star topology, bus topology, ring topology, and tree topology. In a mesh topology, devices are connected with many excessive interconnections between network mode. In a star topology, the devices are connected to a central computer, and the nodes communicate across the network by passing data through the hub, which is the central computer. In a bus topology, it connects all devices on a local-are network called LAN. Bus networks are not very pricey, and they are easy to install. In a ring topology, it consists of a local area network whose topology is a ring. The messages travel around the ring. In a tree topology, it is considered a "hybrid" topology that combines characteristics of the bus and star topologies.[24]
Data Transmission Characteristics
[edit | edit source]Data Transmission
[edit | edit source]
Data transmission is the actual transfer of data over a channel. The types of channels are copper wire, optical fiber, wireless communication channels, storage media and computer buses. This data is transmitted via signals, which can be electrical, radio waves, microwave or infrared. Data can be transmitted analog by using both analog and digital signals. The modem can change and process the digital data it receives. The data transmitted can come from the keyboard, which is the data source. The data transmitted can also be analog, such as from a cell phone, and can be digitized using source code. The source code is the computer's instructions, which are read and interpreted by the computer.[25]
Bandwidth
[edit | edit source]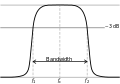
Bandwidth is the amount of data that can be transmitted in a given amount of time. Bandwidth is also referred to as throughput. The measure of bandwidth can be bits per second (bps), or thousands of bits per second (Kbps), or millions of bits per second (Mbps), or billions of bits per second (Gbps).[26] Bandwidth refers to the capacity of a connection. A network medium with a higher bandwidth will allow more data to pass through in a given amount of time. Therefore, the higher the capacity, the better the performance. This is not always true, however, because performance depends on other aspects as well. Text data requires the least amount of bandwidth, while video data requires the most.[27]
Analog vs. Digital Signals
[edit | edit source]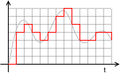
Analog and digital signals are used to transmit information, usually through electric signals. Analog signal is a continuous signal and has constant fluctuations where a digital signal is discrete time signals generated by digital modulation. Analog signals are denoted by sine waves that are smooth and continues whereas digital signals are square waves that are stepping and discrete.[28] Analog signals would be things like human voices in the air and analog electronic devices (AM and FM radio, old telephones). Digital signals have only two levels of voltage: high and low.[29] It is an electrical signal that is converted into a pattern of bits. It has a discrete value at each sampling point. Each sample is defined with a series of bits that are either 0s or 1s. Digital signals are for things like computers, CDs, DVDs, and other digital electronic devices. Analog signal processing can be done in real time and consumes less bandwidth whereas there is no guarantee that digital signal processing can be done in real time and consumes more bandwidth to carry out the same information. The advantages of digital signal are that the recording does not degrade over time and groups of numbers can often be compressed by finding patterns in them.[30]
Transmission Type and Timing
[edit | edit source]
For the transmission of data and network media, there are two ways to send information. Serial transmission is sending data in a single path, one bit at a time. An example of this would be a classroom with students lined up in a single line at the door and leaving one at a time. The advantage of serial transmission is that only one line is used, so the cost is lower, at least compared to parallel transmission using multiple lines. The disadvantage is the cost of the entire transmission. Serial transmission is also not as fast because the bits are transmitted sequentially.[31]
Parallel transmission sends data one byte (or 8-bit) at a time, but each bit takes a separate route. This is a more efficient way to send or receive data. For example, a parallel transmission can be identified as students walking through a large hallway in a school to reach their particular classroom. This approach involves more space to receive data more efficiently.
Synchronous, asynchronous and isochronous transmission are the three different ways of serial transmission. Synchronous transmission is the transfer of data in groups and blocks, one after the other. The advantage of synchronous transmission is that it is faster, but the disadvantage is that it requires buffering and ensures that the sender and receiver have the same clock frequency.[32] Asynchronous transmission is not as widely used as synchronous transmission because it is sent when it is ready. The advantages of asynchronous transmission is that this method is cheaper if the lines are short, due to the idle time being short. Each character being all independent will not be interupted in the process. The signals can halso ave different bit rates and the transmission can start as soon as possible. Finally, Asynchronous transmission can send data all at once. The disadvantage of asynchronous, however, is that it is less efficient and slower, because there are gaps between bits.
Data can also be transmitted in three main different ways. Simplex transmission is when data is transmitted in only one direction. Half-duplex transmission sends data in either direction, but data can only be sent in one direction at a time. Full-duplex transmission sends data back and forth in either direction and can be done simultaneously.
Delivery Method
[edit | edit source]Data is delivered by using circuit switching, which is a specific path between a sender and a receiver. A telephone system is an example of circuit switching because the path is dedicated to only those two people for the time being. Once they are off the phone, the path is free to use by whomever else. Sending data over the Internet is called packet switching. The messages sent are detached in “packets.” While traveling through the Internet, the packets contain all information going from the sender to the receiver. Once the transmission is complete, the packets are put back together to create the correct message.
Signature Characteristics
[edit | edit source]Characteristics include the physical transfer of data, or a digital bit stream or a digitized analog signal, through a point-to-point communication channels (copper wires, optical fibers, storage media and computer buses). Data is represented as an electromagnetic signal, such as an electrical voltage, radiowave, microwave, or infrared signal. Its messages are symbolized in one of two ways. The first, known as baseband transmission, is completed by a sequence of pulses using a line code. The second, passband transmission, utilizes a specified set of continuously varying waveforms, created using a digital modulation method. Regardless of which technique is used, the receiver must synchronize itself with the transmitter. There are two distinct types of transmission -- Asynchronous and synchronous. In asynchronous, the two devices are relatively close to each other in speed. This means that if only small bursts of data are sent at a time, its synchronization will be successful as long as the receiver is able to synchronize with the immediate beginning of the data burst. In synchronous transmission, a significantly larger amount of data is sent in each block, which either contains, is preceded, or accompanied by signaling, thus permitting co-synchronization of the devices. The majority of all network backbone traffic today is synchronous.[33]
Communications Protocols and Networking Standards
[edit | edit source]The definition and usage of TCP/IP
[edit | edit source]

Communications protocol and networking standards are necessary in order to determine how devices on a network communicate and what requirements are needed in order for hardware and software manufacturers to develop computing products that function with other products. Techopedia, an online source of computing devices, explains communication protocol as “formal descriptions of digital message formats and rules. They are required to exchange messages in or between computing systems and are required in telecommunications.”[34] Protocol deals with issues concerning packet size, transmission speed, packet sequence controls, routing, and address formatting. These are just some of the many things that protocol and standards deal with in computing devices. Some popular protocols include File Transfer Protocol (FTP), Hypertext Transfer Protocol (HTTP), and Post Office Protocol (POP3). There's little argument that the most popular communications protocol being used today is TCP/IP. The protocol that's used for transferring data over the Internet, TCP/IP is actually a combination of two protocols. The TCP part of the equation stands for Transmission Control Protocol and it is culpable for data delivery. IP stands for Internet Protocol and it provides routing information and addresses. There are several reasons for the continued popularity of TCP/IP. One of these reasons is the flexibility of the dual protocols, as the core has been able to remain largely the same over 25 years, even with the immense growth of internet popularity. Another reason is the routing design, as TCP/IP is designed specifically to facilitate the routing of information over a network of arbitrary complexity.[35] Pretty much all operating systems have built in support for the TCP/IP protocols so that is also a big factor in their popularity.
One potential controversy related to IP's in particular was the scare when the Internet had run out of Internet addresses. The original IP version, called IPv4, had used up all the potential number combinations so no new folks would have been able to connect to the internet... that is, until IPv6 came out. It uses 128 bit addresses, versus the mere 32 bits of IPv4, ensuring that it will be another long time to go until we risk running out of internet addresses again.[36]
Ethernet (802.3) is the most widely used standard for wired networks. It is typically used in local area networking (LAN) with twisted-pair, coaxial, or fiber-optic cabling. There are many standards of Ethernet and each of those standards reaches a maximum speed. Terabit Ethernet standard is the most current standard that is being developed and improved. It will be used to deliver video, digital X-rays, and other digital medical images. In order for a device to be connected to an Ethernet network, the device needs to have an Ethernet port built into the device or added with an expansion card. Power over Ethernet (PoE) allows for electrical power to be set along in the cables of an Ethernet network. This is what allows security cameras to get electrical power while also maintaining a network connection.
Wi-Fi Standards (801.11)
[edit | edit source]
Wi-Fi, which uses the IEEE standard 802.11, is a very popular wireless networking technology that uses radio waves to provide wireless Internet connection to devices. It is perhaps the biggest theme that today’s technological generation revolves around. With the continuous evolving technology, almost every single mobile device now requires an Internet access, or a wireless network standard like Wi-Fi. Due to this, Wi-Fi hardware is built into virtually all portable computers, mobile devices, and even other portable products like printers, digital cameras, gaming consoles, etc. Consequently, the popularity of a Wi-Fi network in houses, businesses, and public hotspots—airports, hotels, coffee shops—has grown steadily. Supporting “roaming,” devices connected to a Wi-Fi network are able to move from one access point to another, as long it is inside or around the actual building or area. The speed and strength of a Wi-Fi network depends on various factors like the Wi-Fi standard or the hardware being used. For example, the most widely used Wi-Fi standards today are 802.11g and 802.11n. The 801.11n, the newest Wi-Fi standard, is in fact currently the fastest standard today, which is able to transfer data five times as fast as the 802.11g standard.
However, even though Wi-Fi seems like the next best technological invention after computers and the Internet, it does have some minor disadvantages that limit the ultimate use of it. For example, Wi-Fi networks have a limited range; one will lose the connection to a network if they move out of the range of that network, usually 300 ft. away from the actual router. They would then have to connect to the next available Wi-Fi connection. Another limitation of Wi-Fi is that many businesses may be physically too large for a conventional Wi-Fi network to cover the entire area. However, there are special networking connections known as WiMAX or Fixed WiMAX, that provide Internet access for a longer radius, stretching from 2 to 6 miles. Using multiple WiMAX towers, similar to cell phone towers, it is even possible to provide coverage to an entire city or any geographical area! [37]
Cellular Standards
[edit | edit source]
It is no secret that the technology used for mobile phones has vastly evolved over the years. What started out as basically a mobile brick has quickly transformed into a compact, highly productive, and speedy cellular communication device. However, many people are unaware of the generational breakdown of these devices. When the first generation mobile phone was released decades ago in the 1980s, it was produced with only the purpose of voice communication in mind. It was not until the second generation came out years later, around the 1990s, that we started to see both data and voice combined into one device. This generation is best known for its access to both Global System for Mobile communications (GSM) and Code Division Multiple Access (CDMA) which greatly work to enhance speed and communication up to 14.4 Kbps. When the third generation came along in the 2000s, we saw companies start to use packet switching and access speeds as fast as 2 Mbps. This brings us to where we are today. Cellular companies across the globe are starting to utilize 4g technology and offer outstanding speeds of up to 20 Mbps. Though 20 Mbps is a lot faster than 3G’s speeds, which can be as low as 3.8 Mbps, it is not at the specified 100 Mbps that fourth generation phones are supposed to require. Fourth generation phones are using the LTE, Long Term Evolution, technology or the WiMAX technology, both of which allows for more capacity and faster speeds across the mobile network.[38] These two technologies are incompatible to each other and it depends on which mobile phone provider that you are using. Currently, Sprint is using 4G WiMAX, while Verizon and AT&T are using 4G LTE.[39] This is a necessity in today’s world as more and more people buy mobile smart phones and demand a very high amount of data to be transferred to and from their phones. These technologies use OFDM, orthogonal frequency-division multiplexing, instead of TDMA, time division multiple access, or CDMA, code division multiple access. This change in technologies is what the mobile phone market accepts as a difference between the third generation and fourth generation of phones because OFDM is significantly faster and more efficient, even though it is not as fast as the original specification.[40] Another plus for the fourth generation phones is that they can still access broadband Internet content that many consumers vie for. Hopefully in the near future, technology companies can actually provide mobile phone consumers with a phone that will reach speeds up to 100 Mbps. With technology constantly evolving and expanding, where will it take us next? Into what technological wonders is fifth generation technology going to bring us? [41]
Wireless Printers
[edit | edit source]
Wi-Fi is one of the most popular networking standards that uses wireless LANs. Certain devices come Wi-Fi enabled and some can be hooked up within the wireless network. One of the most popular devices being used today is the wireless printer. Not any printer can be used, however. Special printers nowadays have the Wi-Fi transceivers built into them to locate the available networks. The major advantage is that multiple computers can print to a printer in any location that you want. Another great advantage is that you can avoid the painful cable clutter that comes with all of the devices you could hook up to the computer. It takes much less time for a computer to connect to the printer through Wi-Fi then it does to download the software and connect it manually with a USB cord. One thing to consider though is how windows and doors might affect the strength of the signal. Security is something to think about as well. Some printers contain a WPA (Wi-Fi Protected Access) encryption that allows only special computers to connect if they activate the similar feature.[42] Believe it or not, these types of printers are actually reasonably priced compared to some of the other types of electronics out there on the market.
Networking Hardware
[edit | edit source]
Network adapters or "Network Interface Cards," (NICs) are used to connect a computer to a high-speed network. Most recently manufactured motherboards have them already built in. Otherwise, a NIC may be installed onto an open PCI expansion slot on the motherboard.
Modems are able to convert your computer's digital data to analog data that can be sent over telephone service lines and converts incoming analog data to digital data that the computer can work with. The better quality modems are able to do the work directly on the card. They are known to be faster and more efficient than a cheaper modem, go figure![43]

The term modem is short for modulator/demodulator. Modems are used to connect with internet services providers. They transfer data between the internet service provider and the computer. There are a few different types of modems available. Analog modems can be used with dial-up connections. Digital subscriber line or DSL and cable modems are used with high speed broadband connections. Integrated services digital network, or ISDN modems are used for even higher speed connections. [44]
Wireless routers have changed drastically in recent years. Once just a simple tool to broadcast the internet into a home or an office, today many wireless routers have additional functions and capabilities. They can offer multiple frequencies to help avoid interference. They can be setup to allow guest access to the network. Some even allow for the advanced security setup with enhanced features like parental control to limit access to certain websites. Another convenient feature is the addition of storage to the device. Some routers allow connection of external storage devices, while others have storage built in. Many routers also have mobile apps designed to control them. In the age of tablets and smartphones, the ability to control your network settings via a mobile device is key.
Hardware for Connecting Devices and Networks
[edit | edit source]
There are different configurations used in connecting devices to a network as well as connecting networks to other networks. An example of a configuration for a home network is a star topology where there is one central device that provides a connection for other devices. This central device, or hub, is not as efficient regarding the availability of bandwidth between the devices, specifically computers, that are connected to the hub. More exactly, the hub can lead to unnecessary traffic build-up because it repeats everything it receives to other devices. This may or may not be an issue depending on the size of the network. A small network will not have much issue with using a hub for a central device, but for other, larger networks a different device may be more practical. A switch is more suitable for larger networks. Like hubs, switches allow devices to communicate with each other. However switches contain ports that are designated for individual devices, which allows for a more efficient allocation of bandwidth for the devices as a whole.[45]
Routers are used to connect different networks together. [46] Because they maintain configuration information in a storage known as a routing table, routers can filter incoming or outgoing traffic.[47] Wireless access points are devices that allow a device access to the network. This, along with a switch, can be found in wireless routers. These routers connect both wired and wireless devices to a network, which then connects that network to the Internet. Another device is a bridge, which simply joins two LAN segments. An example of this would be connecting a game console to a home network.
Repeaters, Range Extenders, and Antennas
[edit | edit source]
Network repeaters regenerate incoming electrical, wireless or optical signals. Today, most data transmissions rely on Ethernet or Wi-Fi, both of which can only span a limited distance before the quality of the signal degrades. The goal of the repeater is to help preserve a tolerable signal over long distance while examples like Ethernet or Wi-Fi have trouble to.[48] While repeaters are available for both wired and wireless networks, repeaters for wireless networks are referred to as range extenders. Range extenders are commonly found in homes in order to eliminate "dead zones", or areas where the normal network doesn't offer coverage. A range extender will typically wirelessly connect to the network, then repeat the wireless signal. One of the most reliable and popular ways of increasing the range of a network is through the use of an antenna. Antennas are highly effective because of their ability to convert radio-frequency into alternating current, or vice-versa. The most common type of antenna is the dish antenna, which is used for satellite communications. An example of antennas being used can be seen on an everyday home rooftop, where dish-like antennas are often used for television signal [49]
Review
[edit | edit source]Review Definitions
[edit | edit source]Analog signal: A type of signal where the data is represented by continuous waves.
Bluetooth: A networking standard for very short-range wireless connections; the devices are automatically connected once they get within the allowable range.
Bus Network: A network consisting of a central cable to which all network devices are attached.
Coaxial Cable: A networking cable consisting of a center wire inside a grounded, cylindrical shield, capable of sending data at high speeds.
Ethernet (802.3): A widely used wired LAN networking standard.
Extranet: An intranet that is at least partially accessible to authorized outsiders.
Fiber-Optic Cable: A networking cable that utilizes hundreds of thin transparent fibers over which lasers transmit data as light.
Intranet: A private network that is set up similar to the Internet and is accessed via a Web browser.
Local Area Network (LAN): A network that connects devices located in a small geographical area, such as within a building.
Mesh Network: A network in which there are multiple connections between the devices on the network so that messages can take any of several possible paths.
Modem: A device that enables a computer to communicate over analog networking media, such as connecting to the Internet via telephone lines.
Private Area Network (PAN): A computer network for interconnecting devices centered on an individual persons work space.
Parallel Transmission: A type of data transmission in which bytes of data are transmitted at one time, with the bits in each byte taking a separate path.
Router: A device that connects multiple networks together; routes packets to their next location in order to efficiently reach their destination.
Serial Transmission: A type of data transmission in which the bits in a byte travel down the same path one after the other.
Virtual Private Network (VPN): A private, secure path over the Internet that provides authorized users a secure means of accessing a private network via the Internet.
Wide Area Network: a computer network in which the computers connected may be far apart, generally having a radius of half a mile or more.
Wireless Network: A network in which computers and other devices are connected to the network without physical cables; data is typically sent via radio waves.
Review Questions
[edit | edit source]1.) Third generation computers became smaller and more reliable than earlier computer generations, incorporating multiple transistors and electronic circuits on a singles tiny silicon chip by utilizing ______________.
2.) A small business needs a computer that can act as a server for a number of PCs and handle a number of users running different applications. The class of computer best suited to its needs would be a(n) __________.
3.) Programs designed to perform specific tasks or applications, such as computing bank-account interest, preparing bills, or creating letters, are contained in ____________.
4.) An example of system software is __________________.
5.) PC-compatible and Mac are the two major personal computer ____________.
6.) The purpose of a computer network is to allow computers to _____________.
7.) Computers and the traditional devices that we use every day- such as the telephone, TV, and home entertainment system- have begun to merge into single units with multiple capabilities; this trend is referred to as ____________.
8.) Having a basic understanding of computers and their uses is called _______________.
9.) The four main computer operations are input, output, storage, and _________.
10.) A mobile device based on a mobile phone that can be used to access the Web and e-mail wirelessly, as well as other capabilities such as taking digital photos, is often referred to as a(n) ___________.
Review Answers
[edit | edit source]Answers 1.) Integrated Circuits 2.) Midrange Server 3.) Application Software 4.) Windows, Osx, and Linux 5.) Platforms 6.) Communicate with each other, share software, and share hardware 7.) Convergence 8.) Computer Literacy 9.) Processing 10.) Smartphone [50]
- ↑ http://www.aopa.org/News-and-Video/All-News/2009/January/22/Whats-up-with-121-5-MHz-ELTs
- ↑ http://www.webopedia.com/TERM/N/network.html
- ↑ http://voip.about.com/od/glossary/g/PacketDef.htm
- ↑ http://www.rfidjournal.com/articles/view?11093
- ↑ http://electronics.howstuffworks.com/gadgets/high-tech-gadgets/rfid.htm
- ↑ http://www.caranddriver.com/features/vehicle-tracking-systems-and-data-recorders-tested-gearbox
- ↑ http://www.americantelemed.org/learn
- ↑ http://www.surgeryencyclopedia.com/St-Wr/Telesurgery.html
- ↑ http://computernetworkingnotes.com/network-security-access-lists-standards-and-extended/network.html
- ↑ http://www.webopedia.com/DidYouKnow/Hardware_Software/Networking/tree_topology.html
- ↑ http://en.kioskea.net/faq/2761-what-is-network-architecture
- ↑ http://compnetworking.about.com/od/basicnetworkingconcepts/g/network_servers.htm
- ↑ https://en.wikipedia.org/wiki/Peer-to-peer
- ↑ http://therealping.wordpress.com/2008/01/30/network-sizes/
- ↑ Understand Computers Today and Tomorrow 14th Edition Comprehensive
- ↑ Understand Computers Today and Tomorrow 14th Edition Comprehensive
- ↑ http://www.ciscopress.com/articles/article.asp?p=31276&seqNum=3
- ↑ http://www.ciscopress.com/articles/article.asp?p=31276&seqNum=3
- ↑ Understand Computers Today and Tomorrow 14th Edition Comprehensive
- ↑ http://smallbusiness.chron.com/disadvantages-wired-technology-17833.html
- ↑ http://www.computerweekly.com/feature/Wired-vs-wireless-in-the-enterprise
- ↑ http://www.firewall.cx/networking-topics/cabling-utp-fibre/112-network-cabling-utp.html
- ↑ http://en.kioskea.net/faq/2761-what-is-network-architecture
- ↑ http://www.webopedia.com/DidYouKnow/Hardware_Software/Networking/tree_topology.html
- ↑ https://en.wikipedia.org/wiki/Data_transmission
- ↑ http://searchenterprisewan.techtarget.com/definition/bandwidth
- ↑ http://compnetworking.about.com/od/speedtests/g/bldef_bandwidth.htm
- ↑ https://www.diffen.com/difference/Analog_vs_Digital
- ↑ http://en.wikibooks.org/wiki/Analog_and_Digital_Conversion/Analog_vs_Digital
- ↑ https://www.diffen.com/difference/Analog_vs_Digital
- ↑ http://ecomputernotes.com/computernetworkingnotes/communication-networks/data-transmission
- ↑ http://ecomputernotes.com/computernetworkingnotes/communication-networks/data-transmission
- ↑ https://umuc.equella.ecollege.com/file/d0edbbfc-0779-4cd5-8203-51719a5ffc2e/1/CMIS435-1109.zip/Modules/M5-Module_5/popups/Data.html
- ↑ http://www.techopedia.com/definition/25705/communication-protocol
- ↑ http://www.tcpipguide.com/free/t_TCPIPOverviewandHistory-3.htm
- ↑ http://mashable.com/2011/02/03/ipv4-ipv6-guide/
- ↑ http://www.britannica.com/EBchecked/topic/1473553/Wi-Fi
- ↑ http://www.mmfai.org/public/docs/eng/MMF_LTE%20Brochure.pdf
- ↑ http://www.mobileburn.com/definition.jsp?term=4G
- ↑ http://searchmobilecomputing.techtarget.com/definition/4G
- ↑ http://bpastudio.csudh.edu/fac/lpress/471/hout/3G.htm
- ↑ http://www.hp.com/global/us/en/wireless/wireless-basics.html
- ↑ http://www.kitchentablecomputers.com/nic.php
- ↑ http://www.techradar.com/us/reviews/pc-mac/networking-and-wi-fi/modem-routers
- ↑ http://www.darron.net/network/secondpage.html
- ↑ http://whatismyipaddress.com/routers
- ↑ http://compnetworking.about.com/cs/routers/g/bldef_router.htm
- ↑ http://compnetworking.about.com/cs/internetworking/g/bldef_repeater.htm
- ↑ http://searchmobilecomputing.techtarget.com/definition/antenna
- ↑ http://coursemate.cengage.com/CPReader/View/9781133114598/default.aspx?eISBN=9781133114598#da32b353-ffd5-4a88-91a8-c28f124d2211
