Living in a Connected World/Privacy in a Digital Age
Introduction
[edit | edit source]his chapter of Living in a Connected World will cover various topics relating to Privacy in a Digital Age. The notion of privacy in relation to technology is a discourse which has seen a number of challenges in recent years. There are ongoing debates surrounding data mining and mass surveillance from the revelation that Snapchat saves users images to very recent findings that smart TVs can be used to spy on people.
This chapter will explore the ways in which online privacy has evolved over the years with the following sections:
- Definitions and Theorists - this section will outline various definitions surrounding the idea of online privacy as well as the relevant theorists who have done extensive research into it. This will be an introduction to some of the ideas that will be covered further on.
- Public vs. Private Persona - this section will explore the privacy policies of different sites and apps and will explore how their privacy settings allow users to take control of their own information and determine who their audience is. There will be an additional sub-topic on the notion regarding the individual vs. collective.
- Location Services on Apps - this section will explain what location services on apps are and discuss the benefits and the negative impacts of them.
- Privacy Laws - this section will outline the Protect Intellectual Property Act and the Stop Online Piracy Act as well as the ISP blocking within the UK.
- Internet Censorship- this section will discuss the way governments in China and Myanmar use internet censorship to control and suppress users from viewing undesirable information.
- Surveillance - this section will outline data surveillance and discuss the Investigatory Powers Act 2016.
- Personal Information Online - this section will discuss the personal information available online, the dangers of the visibility of this information and the actions that users have taken to avoid potential threats. Security levels and risks of online shops and banking will also be explored in this section.
- Privacy and Leaks - this section is dedicated to exploring the social impact aspect of hacking. Firstly it will explain the technology behind hacking, namely spyware, and how this technology can be used to access private information. Then, it uses different celebrity and non-celebrity examples to demonstrate the social side of privacy breaches and how this impacts on people and our society.
- Privacy in relation to Living in a Connected World - this section will discuss how Privacy in a Digital Age relates to other chapters within the book with the main focus on privacy in relation to the Online/Real-Life Divide, Technology as an Extension of Self, Persistent Connectivity and the Fear of Missing Out, Digital Labour on Social Media Platforms, and Filter Bubbles and the Flow of Information.
Definitions
[edit | edit source]Private Sphere
[edit | edit source]
The concept of privacy is often discussed in relation to the public. Zizi Papacharissi defines the term private as:
“that which doesn’t become public, and thus remains under private ownership. In the realm of the personal or domestic, possibly considered unofficial, and involving action structured around the self.”[1]
The historical roots of the word can be traced back to the works of Plato and Aristotle regarding the idea of private property. There is an emphasis on the domestic domain of the household being the private space for individuals to wind down and relax after spending the day in public.
We come back to this idea of private vs. public in relation to the individual vs. the collective. The private space being an area (whether physical or virtual) for an individual to be themselves (although with developing technological tools such as blogging or vlogging, this idea is contested). The idea of the collective refers more to the public domain located in a public space, such as government institutions within the public sector and the management of public affairs being for the greater good of the city state.[2] Papacharissi argues that within this historical context, “private property ownership signified status and granted individuals participation rights which led to greater power leverage in public life.” Therefore, it is impossible to define one concept without the other.
One case study which highlights the divide between public and private is the graphic novel and film, Persepolis by Marjane Satrapi. She presents her life growing up in Iran during the Islamic Revolution and how in order to survive physically they had to publicly conform to the regime, whilst to survive psychologically they had to privately rebel by throwing secret parties. This divide between public and private, individual and collectivity is significant in relation to identity and visibility. While Persepolis is arguably an extreme example of the divide, identification and online portrayal is still prevalent in every Facebook profile. While Facebook is arguably both a public and private social networking tool, the way in which individuals engage with it indicates how it blurs the line between the two definitions.
Public Sphere
[edit | edit source]The Public Sphere is a concept that has been defined by many, but put most simply as:
“public is that which does not remain private, and thus can be shared in common.”[3]
The very term Public Sphere happens to be the English translation of the German term Öffentlichkeit, noted by Jürgen Habermas in 1962 in Strukturwandel der Öffentlichkeit (The structural transformation of the public sphere).[4] Historically, Greek and Roman philosophers associated the term public with principles of governance, democracy, and deliberation, “thus, the public man emerged as a citizen of the world, a member of a civil society with civic duties”.[5]
Ideally, the Public Sphere is often seen as private people coming together as a public entity and is often associated with ‘the greater public good’. Habermas noted that some important dimensions of the Public Sphere included the formation of public opinions, which all citizens have access to, and the freedom of conference in an unrestricted fashion.[6] For example, politics (in theory) is transparent and kept in the open for the public to witness and debate on. When a petition receives above 10,000 signatures from the public, the government must respond to it and when it receives above 100,000 they must debate on it in parliament.[7]
Today, both the Public Sphere and Private Sphere can be looked at in relation to the Digital Age we live in as with the introduction and advancement of technology, the spheres have gained an online presence. Not only that, but we, as a nation, are more literate and politically outspoken and the Public Sphere has expanded to almost the stage where it is no longer existent. Arguably, in this day and age, very little is kept in the Private Sphere of people’s lives and the Public Sphere is all encompassing, blurring the lines between the two spheres.
Digital Age
[edit | edit source]The Digital Age can be referred to the information age that has developed due to economic growth. The industrial revolution was a major factor in technological growth. The technical developments in such revolutionary machines, such as the steam engine was just a starting point to what we have now in terms of machinery and computers. The Industrial Revolution also was a pivotal point in society for allowing more work and trade unions. More people were learning new skills to cope with the technical developments. It can be seen clearly as to why the Information Age can also be called the Third Industrial Revolution. Both lend opportunities for society to organize itself and its economic activity. [8]
“There are claims of the new media will replace old media.” [9]
Burnett and Marshall describe the Internet having a “chameleon like nature”. It merges together and lends itself to suit every situation. The digital age allows a range of transmitted information regarding factual, entertainment and shopping. The development of technology means that the use and need for pen and paper is becoming obsolete. Since starting in the 1970s, the Digital Age was a catalyst for filmmakers and writers as they “danced between utopian and dystopian” worlds within their work. For example, Terminator and Matrix, where men manage in a machine world. Now in 2017, the ideas used in such films doesn’t seem to far away.
Global Village
[edit | edit source]Like the industrial revolution, according to Marshall McLuhan, technology recognises society. New skills, new ways of conversing and sharing information allowed McLuhan to coin the idea of the ‘global village’. The global village refers to society being able to easy transfer and share knowledge through technology. The community that is formed is maintained by the structure that the global village has created. “The community structure of exchange occurs at the level of transnational interest of communities who maintain their linkages through the internet” p18. It is this structure that has formed the notion of ‘collective intelligence’.
Collective intelligence “is a form of universally distributed intelligence, constantly enhanced, coordinated in real time and resulting in the effective mobilization of skills.” [10] The digital age has allowed a vast amount of information to be shared, learned and developed further. It is a never ending cycle as the digital age is continuing to grow as we become more advanced and so users knowledge can be enhanced. However, with all this information being sent back and to through transmitters, it is always recorded and coded into the system online. The privacy is not there, completely. There are always ways to trace back this information.
Web 2.0
[edit | edit source]Web 2.0 refers to a second wave of Internet that focuses on User Generated Content (UGC). According to Tim O’Reilly (2005) it is made up by the main characteristics of:
- Radical decentralization.
- Radical trust.
- Participation.
- Users as contributors.
- Rich user experience.
- Remixing data.
- Collective Intelligence.
- Better software by more users.
- Control of one’s data.
UGC has been increasingly popular in terms of media communications. Through social media sites such as Facebook and Twitter, organizations use it to attract views or customers. It has become apparent that users of the internet thrive off being able to share their knowledge or opinions. News organizations allow their readers to comment on social media, and share thoughts and opinions. Clothing brands allows customers to review their purchases which then informs other buyers as well as the company.
It was a term used after the dot.com crisis in 2000 when a large amount of internet companies crashed. By using the term Web 2.0, it suggested a new fresh idea of UGC, even though they were already in the process prior. O’Reilly states that Web 2.0 was needed for “identifying the need for new economic strategies for internet companies”. By suggesting that society and technology is driven by each other, it can be argued that the contemporary WWW is developing in a continuum. Fuch’s claims that the tech and informational structures of the Internet have to, a certain degree, changed in order to guarantee the continuity of the characteristics. [11]
Web 2.0 can also be seen as an "approach to the web", according to David Gauntlett and by collecting ideas, creativity can be enhanced in a way it hasn't been able to before. From this, it can be argued that Web 2.0 has a political aspect to it as users network and connect. [12]
Theorists
[edit | edit source]Danah Boyd
[edit | edit source] | |
| Born | Altoona, Pennsylvania |
| Nationality | American |
| Notable work(s) | Participating in the Always-On Culture (2012) Social Media: A Phenomenon to be Analyzed (2015) |
Danah boyd studied Computer Science at Brown University then went on to pursue her master's degree in sociable media and got a double BA in Economics and Media Studies at Mount Holyoke College in 1995. In 2009, she joined Microsoft Research as a Social Media researcher.[13] She is a frequent blogger and is involved in addressing issues surrounding youth and technology with articles focusing on the implications of social networks for youth identity.
In her chapter on ‘’Participating in an Always-On Culture’’, she outlines the ways in which we have become somewhat “tethered” to our technological devices. The statement “…those little devices in our pockets are so psychologically powerful, that they don’t only change what we do – they change who we are” effectively supports the underlying argument of this Wikibook in that we don’t really know how much these big Internet based corporations know about us; we just go along with the terms and conditions because we have been drawn into the addictive nature of online social media.
Her overarching argument is that the distinctions between online and offline worlds are becoming more and more blurred. That these practices of technologically communicating over a network emulate previous forms of communication. She argues that there is a challenge towards finding the balance between the two distinctions as they are increasingly shifting, that we should embrace this new 'always-on' reality and learn to find a balance between online and offline existence. The notion that we are constantly linked to the network in a state of persistent connectivity presents numerous problems in relation to privacy. The collection (or mining) of data from millions of users allows companies to build up a very detailed profile of user, even if they don't have a particularly broad online presence.
Christian Fuchs
[edit | edit source]Christian Fuchs is a Professor of Social Media at the University of Westminster, UK. He is a Director of the Communication and Media Research Institute and he is also a Director of the Westminster Institute for Advanced Studies.
In 2011 (until 2015) he was Chair of the European Sociological Association’s Research Network 18 (RN18), carrying out Sociology of Media and Communications Research.
In 2012 (until 2016) he became Vice-Chair of the EU COST Action “Dynamics of Virtual Work” that studied unpaid and paid forms of digital labour.
In 2015 he became a member of the European Sociological Associations Executive board and he is currently preparing for the 13th European Sociology Conference which will take place in Athens from August – September 2017.
His interest and expertise lies within social theory, critical theory, critical digital and social media studies and internet and society studies.
His 2014 work ‘Social Media: a critical introduction’ has provided a good base for the ideas which are explored in this Wikibook with a particular focus on his discussions of Web 2.0, Habermas’ concept of the Public Sphere and of his discussion of Google as a Surveillance Machine.
Helen Kennedy
[edit | edit source]Kennedy is a Professor at the University of Sheffield and joined the Department of Sociological Studies as a Faculty Research Chair in Digital Society in November 2014. [14] She first attended the University of Birmingham where she got a BA in English and American Studies, and after that a Masters in Cultural Studies. She worked in the University of East London for eleven years where she set up the one of the country’s first digital media programmes.
Her research focuses on:
- Social Media and Data Mining
- Big data, data visualisation, and data in everyday life
- Digital Media and Work Practices
- Digital and other inventive methods
Kennedy's research is very applicable to Privacy in a Digital Age as she outlines the practices of data mining in her recent book Post, Mine, Repeat: Social Media Data Mining Becomes Ordinary (2016). She has also published Net Work: Ethics and Values in Web Design (2011) and Cyborg Lives? Women's Technobiographies (2001) as well as a number of journal articles on the same topics.
In relation to this Wikibook, data mining is a very prevelent topic for the digital age. Kennedy's book Post, Mine, Repeat is very informative in showing how data mining fits into commercial monitoring and organisations. This topic will be covered further in the book in the sections on Policies and Settings and especially in relation to data mining and adverts tailored to individuals. She also outlines the role of data mining regarding activism and public sector services, how it is adapting and how it relates to surveillance.
Marshall McLuhan
[edit | edit source]Canadian Professor, Herbet Marshall McLuhan (21st July 1911-31st December 1980) was most well known for devising the term, “the medium is the message” and Global Village. His ideas on technical development and society made him a main figure in the media discourse in the 1960s. [15] In his book, The Gutenberg Galaxy, he argued that new technologies would move society from individualism to form collective identities and that “the world would become a computer, an electronic brain”. [16] Though his work was critiqued, McLuhan argued that he 'probed' other thinkers and gave tools to analyse the media and society.
Understanding Media: The Extensions of Man (1964) went to me his most cited work. Here, he suggested that media, in the form it comes in, has an effect on society, rather than the content the media offers. [17] He went on to publish many books and influenced many critics and thinkers on media as it has continued to develop.
Zizi Papacharissi
[edit | edit source] | |
| Born | Thessaloniki, Greece |
| Residence | Chicago |
| Nationality | Greek and American |
| Notable work(s) | A Private Sphere (2010) Affective Publics: Sentiment, Technology and Politics (2014) |
Zizi Papacharissi is one of the key theorists relating to Online Privacy. Papacharissi graduated from Anatolia college in 1991 and received a double BA in Economics and Media Studies at Mount Holyoke College in 1995. She then went on the achieve a Masters degree in 1997 for Communication Studies. She has continued to contribute her research and insight into online communications by focusing on the socio-political impact of new technologies in her book A Private Sphere. She argues that these technologies have seen a shift in the public and private divide and how this shift has altered our engagement in both. She focuses on the way in which the Internet can be used as a political medium to shape democracies. Papacharissi presents her argument around contesting the notion that new technologies can fix old democracy and how citizenship is exemplified in public, private or hybrid online domains.
She has gone on to have four books published, edited two collections and had over fifty journal articles published. She is currently a professor and head of the Communication Department at the University of Illinois-Chicago. She also serves as Editor of the Journal of Broadcasting and Electronic Media as well as being on the board for eleven other media journals. She has been consulted by a number of large conglomerates including Microsoft and Apple and even the Obama 2012 lecture campaign which she discusses in A Private Sphere. [18]
Private vs. Public Persona
[edit | edit source]Introduction
[edit | edit source]In this section of the chapter, the policy and settings of numerous popular social media apps and websites will be looked into in regards to their influence on the online persona of their users. The privacy settings of different social media apps and websites allow users to decide on their audiences. The opportunity to do so reflects the way in which users express themselves online. If a user can determine who their audience is with features and settings, they may be more inclined to be open with what they post and expose more about their true self, likewise, if they are not as in control of who can access their posts, they may be less likely to be as open. In the following section different apps and sites will be explored in relation to their privacy policies and the privacy settings that they offer to their users.
Policies and Settings
[edit | edit source]This section of the Wikibook will explore the privacy policies and different privacy settings that Google, Facebook, Facebook Messenger, Twitter, Snapchat and Instagram all have to offer to their users.

Collecting user data and information is an important aspect of most companies for numerous reasons and even the household name Google can be considered as a “surveillance machine” which [19], monitors its users’ use of its services and collects their data and information whenever they use access Google.
Google’s Privacy Policy states that “When you use Google services, you trust us with your information.” The policy highlights that Google collects information that its users provide, including any personal information used to set up accounts with Google such as names, email addresses, telephone numbers and credit card details. Google also collect any information and data about their users from the way that they use the different services that Google provide for them such as the device information that the users are operating, the log information and their location information. Through the use of cookies and other similar technologies, Google can also access information about the browsers and devices that its users are operating.
Search Engine
[edit | edit source]Google offer a range of different services that user data is collected on including Google’s most popular service, Google Search. Google is the most used search engine of the World Wide Web to date, followed by Yahoo and Bing[20], processing over 3.5 billion search queries daily.[21] As Christian Fuchs stated, “Google has become ubiquitous in everyday life – it is shaping how we search, organise and perceive information in contexts like the workplace, private life, culture, politics, the household, shopping and consumption, entertainment, sports, etc.”[22] Using an algorithm called PageRank, Google orders its search results based on how many links lead to a page. The organisation and ease of the Google search engine because of this algorithm makes it popular both for desktop use as well as mobile browsing. Each search conducted through Google’s search engine is recorded and allows Google to its users interests.
Google can “build a detailed dossier that describes virtually every aspect of your character, food preferences, religious beliefs, medical problems, sexual inclinations, parenting challenges, political leanings and so on”[23] – Robert Epstein, 2013.
Google has its own program called Google AdSense which tracks the browsing history of its users. Through the information Google gains from tracking users search habits, they can personalise the content the user sees and show ads that are specific and relevant to what the user has used Google to previously search for.
“We use the information we collect from all of our services to provide, maintain, protect and improve them, to develop new ones, and to protect Google and our users. We also use this information to offer you tailored content – like giving you more relevant search results and ads.”[24]
Although Google collect and store numerous information of their users and offer personalised content and ads based on this information, Google also states that “When showing you tailored ads, we will not associate an identifier from cookies or similar technologies with sensitive categories, such as those based on race, religion, sexual orientation or health.”
In 2008 Google launched its own browser in competition with other browsers such as Firefox and Safari. Google Chrome allows its users the option to use a private browsing mode called “Incognito”. Unlike a regular search session with Google, Incognito sessions do not save the cookies or the search and the browsing history of the user. [25]
Gmail
[edit | edit source]Google has an email service known as Google Mail or Gmail. Those who have Gmail accounts will need to firstly provide Google with their personal information to set up the account. Google can scan the content of emails sent from non-Google accounts so that it can target ads to its Gmail users.[26]
"Just as a sender of a letter to a business colleague cannot be surprised that the recipient's assistant opens the letter, people who use web-based email today cannot be surprised if their communications are processed by the recipient's ECS [electronic communications service] provider in the course of delivery."
As most Google services are free to use, the majority of Google’s income comes from selling advertisements [27]. As their policy states, Google has automated systems that analyse the content of emails to provide their users with “relevant” product features and tailored advertising. The analysis occurs as emails are sent, received and stored.[28]
Some disagree with this and many have criticised Google for intruding on the privacy of its users’ emails.
“Sending an email is like giving a letter to the Post Office. I expect the Post Office to deliver the letter based on the address written on the envelope. I don't expect the mail carrier to open my letter and read it. Similarly, when I send an email, I expect it to be delivered to the intended recipient with a Gmail account based on the email address; why would I expect its content will be intercepted by Google and read?"[29]

At 1.86 billion users on Facebook each month (as of December 2016)[30], the social networking giant lives up to its name with more monthly active users than other social networking giants Whatsapp, Twitter and Instagram combined.[31] The average Facebook user now has around 338 friends.[32], which is a fair few more than the 130 that Daniel Miller suggested back in 2011.[33]
“Every 60 seconds on Facebook: 510,000 comments are posted, 293,000 statuses are updated, and 136,000 photos are uploaded.”[34]
Despite it being created for the use of students to contact each other in college, Facebook now reaches far and wide across the world and is accessed by a range of age groups.
There is a detailed help page which Facebook has dedicated to explaining privacy settings. The page is very user friendly, accompanied by well organised sections with bold titles and graphic icons. While the page appears to be transparent in its bid to inform users of how their data is used, there are somewhat ominous undertones. It emphasises how much the user has control over who sees what with the heading in large font claiming “You’re in charge”. After looking through the privacy basics, there is a section about Facebook’s Data Policy. A lot of the way this policy is phrased is very biased towards presenting a particular image of Facebook: “We collect information about the people and groups you are connected to and how you interact with them”. This suggests that the collection of data is in the user’s best interest, in order to “provide, improve and develop Services”.
Facebook users can change the settings of their accounts to different levels of privacy so that, in theory, the audience seeing the information they post is controlled by them. A profile account which is set to private means that only friends can see the content that they post. Likewise, a profile account which is open can be viewed publicly. Facebook also allows its users to control the privacy of individual posts and individual information in their “about me” sections. A user can decide between sharing what they post “everyone”, with “friends of friends” and with just “friends”.
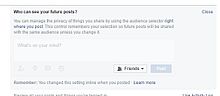

Some of the main features of Facebook’s user security can be found be going into the “Privacy Settings and Tools” page. In this page users can edit a number of things:
- Users can change who can see their future posts
- Users can also “Limit The Audience for Old Posts” on their timelines, which means all their previous older posts can be hidden from the public and from friends of friends and only be able to be seen by friends.
- Facebook allows its users to control who can search for them and contact them, too. Once again users can choose from “everyone”, “friends of friends” and “friends”.
- Users also have the option to keep their profile from appearing in search engines when people type in their names.
Not only can Facebook users change the privacy settings of their own posts to suit their desired audience, but if a friend tags them in a post, posts on their timeline or tags them in photos they can edit their settings so that they control who can see these things.
By going into the Timeline and Tagging Settings in their account Facebook users can:
- Edit who can post on their timeline and choose between their friends or limit it to just themselves.
- Review posts that friends have tagged them in prior to them appearing on their own timeline. This means they can filter which posts they want people to see that they’ve been tagged in and which ones they don’t want on their timeline.
- Aside from reviewing posts, users can also edit their settings so that no posts that they’ve been tagged in appear on their timeline at all and no posts that others have made to their timeline show either.
Facebook also let their users control who can add tags to their own photos so that other users cannot tag themselves or other people in a photo without the original poster’s permission.
Facebook Messenger
[edit | edit source]Released in 2011 as an app dedicated to instant messaging, Facebook Messenger now has over 1 billion users (as of July 2016), a seventh of the world’s population.[35] The app imports the user’s contacts from the Facebook service and can be used on a number of devices. Over the years, Facebook’s messaging service has adapted its features to show who is online, how long ago someone was last online and the time someone has “seen” a message. Interestingly, Whatsapp is the most popular messaging app (although it was bought by Facebook in 2014), while Facebook Messenger is the third most popular, a Chinese messaging service called QQMobile taking second place.
There aren’t any clear sections on the individual policies regarding private messaging data collection, but a Google search brings up this article which details their tracking practices breaching European law[36]. On the surface, Facebook’s privacy basics help page paints a picture of the user being in complete control of their data. The reality is that the network tracks the web browsing of everyone who visits a page on its site, even if the user doesn’t have a Facebook account or has opted out of tracking. There are two new options which Messenger has added to its service in relation to privacy - payments in messenger and encrypted messages.
- Payments in Messenger - This service was implemented in March 2015 in the US. It allows users to send money to their friends by tapping the '$' sign followed by the amount you want to send. The Facebook newsroom[37] has a guide on how to send and receive money along with information about security including the assurances that Facebook “uses layers of software and hardware protection that meet the highest industry standards.” There is a lot of scepticism surrounding this kind of service as there is no further information on the page about how their security works. The effectiveness of this service ultimately lies with the user’s own responsibility and trust with the system. The main concern would be people stealing user’s phones and sending money to themselves.
- Encrypted messages - In October 2016, Facebook released an end-to-end encryption option for messages. The function is an optional feature known as ‘Secret Conversations’. These encrypted conversations allow users to set messages to ‘disappear’ after a certain length of time. In theory, end-to-end encryption means only the communicating users can read the messages and the systems have been designed to defeat any surveillance attempts since no third parties can decipher the data being communicated or stored. However, for the strong encryption to work effectively, only the sender or receiver of a message can have the ability to decode that message. If Google or Facebook has the ability to process the messages, it’s hard to guarantee that only the two people messaging one another are the only two reading.

Twitter is an online news and social networking service where users post and interact with messages, "tweets," restricted to 140 characters. Twitter has a dedicated page explaining their privacy policy and how information is collected, used and shared. It states clearly that “when using any of our Services you consent to the collection, transfer, storage, disclosure, and use of your information as described in this Privacy Policy.”[38] It goes on to describe where the data controllers are located (in the USA, they’re based in San Francisco, outside the USA they’re based in Dublin).
They frequently reiterate that the user alone is responsible for what content they submit through their services. They state that “most of the information you provide us through Twitter is information you are asking us to make public”. They allow a great degree of control over privacy settings and what information is shared with third party services such as the ad tailoring suggestions; if you do not want Twitter to tailor suggestions based recent visits to websites that have integrated Twitter buttons or widgets, you can turn off this feature using the Twitter account settings or Do Not Track browser setting.
They also receive the following Log Data information when their service is used: IP address, browser type, operating system, the referring web page, pages visited, location, mobile carrier, device information (including device and application IDs), search terms, or cookie information. They emphasise that they use this information to analyse data trends (through Google Analytics) in order to improve the service they provide.
Like a number of websites, Twitter uses cookies to collect this data. They use cookies in the following ways: Authentication and security (log on details and security protection), preferences, analytics, research, personalised content and advertising. The information collected in relation to advertising is used to customize their services with more relevant content, like tailored trends, stories, ads, and suggestions for people to follow. There is an option in the user settings to opt out of this.
With the direct, private messaging service Twitter provides, they also store the user data. They say “When you privately communicate with others through our Services, such as by sending and receiving Direct Messages, we will store and process your communications, and information related to them. We do not use the content you share privately in Direct Messages to serve you ads.”
There is also a section on their website here which demonstrates the ways in which Twitter supports online safety and actively advocates for lobbyists who work on issues reflecting internet freedom, national security reform, ECPA reform and patent litigation reform. The information collected in relation to advertising is used to customize their services with more relevant content, like tailored trends, stories, ads, and suggestions for people to follow. There is an option in the user settings to opt out of this also.
With the direct, private messaging service Twitter provides, they also store the user data. They say “When you privately communicate with others through our Services, such as by sending and receiving Direct Messages, we will store and process your communications, and information related to them. We do not use the content you share privately in Direct Messages to serve you ads.” There is also a section here which demonstrates the ways in which Twitter supports online safety and actively advocate for lobbyists who work on issues reflecting internet freedom, national security reform, ECPA reform and patent litigation reform.
Snapchat
[edit | edit source]
Snapchat is an image sharing application that allows users to send one another pictures which "disappear" after a set amount of seconds. According to The Online Real Life chapter, the development of the app has introduced photographic and video filters that offer a voice alteration and the option of sharing pictures for up to ten seconds at a time. Pictures are also able to be saved to one's "memory" as well as posted on the user's "story" that is visible to all of the users in their Snapchat contactg list. It also offers the option to follow the stories of news, celebrities, and current events.[39] This on-going development in applications is a continuous and fluid process which allows user feedback to be implemented on the software.
The website has a section dedicated to the company's privacy polices which can be found here. There are four sections which outline the company's policies:
- Your Privacy Matters - an introduction to the privacy policies.
- Our Approach to Privacy - an outline of all their features and how privacy and security is applied to each.
- Transparency Report - a description of their bi-annual transparency reports in relation to judicial requests. This section covers requests from the government if they need information regarding a legal case.
- Privacy Policy - a list of what data Snapchat collects from users and why. This section has a very in-depth explanation of all the information the company collects along with this advice: "So, the same common sense that applies to the internet at large applies to Snapchat as well: don’t send messages or share content that you wouldn’t want someone to save or share."
The app has been criticised for its lack of transparency regarding user's privacy. Because Snapchat is commonly used for sharing sensitive and private images, the perceived promise of images "disappearing" forever was incorrect. According to this article from The Independent website, "Snapchat’s terms of service allow the company to look through your snaps and share them publicly."[40] The distinctions between public and private spaces is challenged here as users sign up for the service without being aware of their privacy being breached.

Instagram is a social media platform originally curated to provide a space to share photos which can be edited through the app itself. Through the developments of other apps, Instagram has seen an increase in features, most recently 'Stories" which now competes with popularity with Snapchat. Melson and Papachrissi claim that photographs can be a "mnemonic and symbolic device" [41] and by uploading them online, on whatever platform, they can record memories, and they are forever stored online. The idea that photographs can be used to portray a persona is stressed and Instagram, it can be argued uses this, as each photo, encouraged to crop and filter, can only capture the moments the user wants to share and remember. Users actively choose what to share and what to keep private, however, the body of the users are no longer hidden through the increase in visual communication, compared to 1970s-1990's, only when the webcam was introduced and became a strong feature in ways of communication online. [42]
According to help.instagram.com, “By default, anyone can view your profile and posts on Instagram.” Only by selecting the “Private Account” setting can the user make their account private. However, on the help page, it raises the issue that if the user shares their post to another platform, the post can be seen by non-followers and anyone can still directly send videos and photos. If anyone wants to follow a private account, it will have to be requested and approved or ignored by the account holder.
Boyd highlights the meaning behind the power of choosing your followers, referring to them as an ‘audience’ just as a television personality must tailor their content to a specific target audience. She argues that “privacy settings allow teens to limit their expressions to the people they intend to reach by restricting who can see what.” [43] This links back to Rettberg's idea that photographs are taken to preserve a memory that we want to see, and what we want others to see and perceive as a portrayal of a lifestyle or persona.
However, Instagram can be used by accessing it through a third party application, for example, flipboard. Instagram’s privacy settings highlights that posts can appear on Google through these sites, despite being a private profile. Instagram states that it “isn't directly associated with third-party apps that utilize our API such as web viewers, desktop apps or image printing services, and we can't assist you in speeding up the process to remove any Instagram images that may appear on Google”
Instagram is owned by Facebook which uses cookies to track data. Instagram introduced adverts to their feed and according to their help page, Instagram wants to “show ads that are interesting and relevant to you”. Due to Facebook being the parent company, the adverts are encouraged by what you search, ‘like’ and apps that you visit. Facebook also tracks the cookies that you search through your browser and so links that to Instagram.
Individual vs. Collective
[edit | edit source]This section will outline the ways individuals and their relationship to the collective has transformed since the advent of the digital age. The section will cover the historical context of the terms as well as an outline of the socio-political benefits that have been discovered.
The concept of privacy has varying definitions depending on the individual. In societal terms, property bought by an individual is deemed to be their private space which they own. Of course, there are historical buildings belonging to Kings and Queens which would have been closed off to the public, but are now open as a site of tourism. Public space such as parks and town centres are looked after by the community, either through council tax or volunteer work. Therefore, the concept of public and private in relation to the individual and collective is very fluid and often historically interconnected. The notion of shared space tends to revolve around maintaining it to a high standard for the benefit of all the community, something which has been translated to digital space. Papacharissi defines privacy in contrast to the public:
“What is individual, versus what is collective or affects the interest of a collectivity of individuals”.[44]
In relation to the digital age, the Wiki project can arguably be paralleled with the community projects of towns and cities, it’s just that the individuals contributing to the sites are from all over the world. This shift from local and regional to global interconnectivity has seen a transformation in the way communication occurs. Because users are anonymous on Wikimedia, people are no longer pre-judged based on appearance. They are now evaluated based on a level of engagement and specialist knowledge. Therefore, each individual’s input on an area of expertise allows the overall collective project to improve.
Papacharissi states that “civil society is conceptualised as distinct from the market or the bureaucracy of the state, either of which carry the potential of suppressing the will and actions of atomized individuals operating collectively”. This statement is very prevalent in today’s society, with the advent of “fake news” and “alternative facts”, individuals now have to carefully determine what is true and what is false propaganda. The use of petitions in order to accelerate change has been one of the oldest forms of collective public engagement with the state. In the digital age, citizens are now able to sign a petition online with an email address and post code. The ability to quickly share this petition via social media shows the speed at which communication has improved. The notion of the online world being a tool for political engagement is further discussed in the chapter The Hive Mind and Collective Intelligence.
One fictional case study which can be applied to the individual vs. the collective is the Borg in Star Trek. The Borg are a collection of species that have been turned into cybernetic organisms functioning as drones in a hive mind called "the Collective" or "the Hive". The show explores the benefits and drawbacks of collective intelligence. It challenges the ethics of freedom, individuality and creativity especially in relation to the character Seven of Nine, who was liberated from the collective and spends the rest of the series of Voyager attempting to rediscover her individuality. At first, she struggles to lead a life without the voices of millions of other Borg, but she eventually learns to work within the collective of the Voyager crew.
The Borg are a very effective example of how technology can be used to work together in order to improve efficiency, with their sole aim as "achieving perfection". Yet the show arguably foreshadows the challenges and dangers of this kind of technology. Dery argues that "our interaction with the world around us is increasingly mediated by computer technology, and [thus] bit by digital bit, we are being "Borged"...transformed into cyborgian hybrids of technology and biology through our ever-more-frequent interaction with machines".[45] This blurring between human and machine is further explored in Technology as an Extension of Self.
To sum up, the relationship between the individual and the collective depends on a distinction between public and private space. In the "real world", the distinction is made between ownership and community based spaces, but in the virtual world those distinctions become somewhat blurred. With Wikimedia projects, the community space is no longer limited to proximity; it is part of the global space with interconnecting contributors from all over the world taking part and engaging. In relation to privacy in a digital age, this topic highlights the notion of transparency in politics. Laws that affect the public are able to be discussed openly and with increasing interconnectivity through social media, people are able to organise petitions and marches to encourage positive change.
Location Services on Apps
[edit | edit source]As smartphones and the internet become more prominent in our lives, users are becoming more aware of the idea of having their search habits and locations tracked. Privacy in the digital age recedes further into the distance as the tech companies tell users it’s all in the interest of a better, faster and more efficient service. However, users may also find location services invasive, targeting you with local ads or letting apps track you when you don’t want or need them to.
What are Location Service Apps?
[edit | edit source]Firstly, what does location services mean? Well with the users’ permission, location services allow native apps such as, (iOS’s Maps, Weather and Clock), third party apps (Uber, Facebook), and also system services (Compass, Location-based alerts, Time Zone) to use information from cellular, Wi-Fi, GPS and Bluetooth to determine the approximate location of the user. The prime example of using a location service app would be Uber. The innovative taxi service requires the users to download the app, register and provide credit card information. When they request a car, the app uses GPS technology to find their location and alerts available drivers within a certain radius. If no driver responds then the radius grows.
Benefits of Locations Services
[edit | edit source]Location services help companies like Apple and Google, which may in turn help the user. They companies can learn which apps are most geographically relevant to people in your area, which can help track all the places you have recently visited for improved traffic routing. Another beneficial use for location services is, “Find My iPhone” or “Android Device Manager”. These apps rely on access to your device in order to locate and track your lost device.
Here are some examples of how popular iPhone and Android apps use your location information:
- Instagram: Requires your location in order to name it in your post.
- Facebook: Geotags your posts and photos to create a digital journal of all the places you have been. Location services also enables check-ins, tips about places you are visiting, recommendations and notifications about which friends are in your area.
- Twitter: Geotags photos and tailors trending stories to you.
- Tinder: The dating app which finds matches near your location.
- Foursquare: Suggests nearby businesses or products.
- Google Maps: The service offers turn by turn instructions from your journey start point to your destination. It can also inform you about nearby points of interest.
Use Apple as an example, they offer three location-based settings, “Never”, “While Using the App” and “Always”. These settings are put in place for users to choose what app they allow access to their location. The reality of it is, in order for consumers to share their information they need to give permission to do so. However, not everyone understands the real benefits of allowing their location to be shared and questions are asked about the privacy of users [46].
Negatives of Location Services
[edit | edit source]Location based apps are changing the way all sorts of industries interact with their consumers. While location services have upsides they have as many downsides. Despite draining your battery life, users find sharing their location information with certain apps discomforting. Having your location monitored comes with privacy and security risks. Sharing this sort of information can be advantageous to criminals, putting your security at risk. One of the most evident problems with using location based service apps is the ability to switch them off. There are obvious complications associated with using this technology.
There seems to be a fine line between convenience and privacy. At what point do users want their data hidden and what point do they want to take advantage of crowd-sourced data.
'Knowledge is Power'
[edit | edit source]As location based technology advances increased privacy concerns arise. Some location based apps require users to opt-in before sharing any information, but users are still uncomfortable with the idea of being tracked. Despite its conveniences, sharing any kind of information can also be risky. However, 'knowledge is power' and people should try and educate themselves so they can understand how their data is being used or know how to disable the features of location service apps [47].
Privacy Laws
[edit | edit source]Since 2011, the discussion of laws affecting and moderating the internet have grown significantly. Several laws of passed or attempted to pass in major nations such as the United States, the United Kingdom, and China, which have or would have seriously affected the use of the internet. These affects include blocking sites, legally restricting search engines from displaying certain results, blacklisting entire online services, and in general called into question the rights of individuals on the internet.
PIPA
[edit | edit source]One the first major law that dealt with online privacy, or at least the first one to meet massive criticism was PIPA or the Protect Intellectual Property Act. It came about in 2011 and was made to counter the massive amount of pirate sites on the web. It was heavily lobbied by corporations in order to more heavily enforce copyright law [48] which was a goal wanted to be achieved since the creation of websites such as Napster and LimeWire who helped popularize internet piracy, with one of the bigger problems now being that the servers for these new pirate sites where no longer in the US and were out of the Government's jurisdiction.
It key selling point was to be able to target specific sites who's activities were deemed illegal, and have a court order force search engines to not only blacklist those sites from the search results but also disable all hyperlinks to said websites, effectively cutting off access to torrent sites from anyway other than typing the URL in directly.
It was met with massive criticism with many people claiming it could be used as a stepping stone for harsher internet laws and that Corporations could abuse the Act, using individual acts of copyright infringement to target massive legitimate sites such as Youtube, Twitter, Facebook. There were also claims that this law could be used to target individual creators who could be hit with false claims that they could not afford to counter. There were many comparisons to China's massive firewall in this argument. Ultimately the bill was put on indefinite hold until its many flaws were rectified
SOPA
[edit | edit source]Much like its Sister bill PIPA, SOPA (Stop Online Piracy Act) was designed to target online piracy to help better enforce copyright in the face of an ever-growing world wide web filled with illegal torrent and streaming sites. It also had the angle that it was targeting piracy outside of the United States which it claimed would be hurting the US economy as well as weakened the strength of copyright. The bill received strong support from both the House of Representatives and the Senate, as well as the Better Business Bureau, and several other major Corporations who believed they were being seriously harmed by piracy.
The affects of the bill would have been almost identical to PIPA, removing blacklisted sites from search engines, blocking ISP addresses, ect. And much like PIPA, SOPA was met with mass negative backlash. Many people claimed that this bill actions would not only jeopardize the foundation of the internet by stifling creation and shared media due to how easy it would be to abuse Copyright claims, but the idea of forcing search engines to blacklist sites was seen as a violation of the first Amendment. Several websites, including Wikipedia participated in online blackouts to showcase the affects the bill could have on the internet. It aimed to remind people of the importance of a free and open web. [49]
Ultimately, much like PIPA, the bill was not put through, much to the disappointment of many of its supporters.
UK ISP Blocking
[edit | edit source]In the UK, with the introduction of the Digital Economy Bill 2016-17, a new law came into place that forced several Broadband supporters to automatically block any Adult sites as well as certain blacklisted pirated sites. The original idea for the law stemmed from the EU's discussion of new Net Neutrality laws. The aim of this was to prevent children from having easy access to pornography in the face of an ever-growing digital world where most devices can easily connect to the internet, as well as prevent access to pirated sites and crack down on any child pornography. There was also the option for the customers to opt out of the adult content filter though this had to be done manually.
This law was met with criticism because while its affects on piracy and child pornography was praised, many people felt it was being used to wedge the government's will into online rights via moral panic. Some members of the online community argued that by targeting pornography the UK government was able to make a first step towards further Internet censorship by going after something people were uncomfortable or less comfortable defending. Many people also called into question what would happen to a site if it was wrongly blocked, as well as what the term adult website would actually be categorized as? [50]
In the end however, the bill was tabled on November 24th and now it remains in the air as to what will become of it. [51]
Internet Censorship
[edit | edit source]Introduction
The Internet in the 1990’s was described by Jaron Lanier as being a space where users could promote individuality, as early web pages had “flavour of personhood” [52]. The internet also holds a vast expanse of useful information that can help users gain knowledge and has the capability to let users communicate with other users across the globe, sharing news or collaborating to create new forms of information. But what happens when the user’s individuality and the information being shared between users expresses conflict with the over-ruling government ideologies?
Internet censorship can be used to squash and decimate any conflicting information which is very concerning when discussing user privacy. For instance, the Government of the People’s Republic of China and the Myanmar (Burmese) Government have a long history of using extreme internet censorship as a method to control what information users can access and publish online [53]. In 2008, cybercafés in Myanmar (Burma) were required by state regulations to screenshot the user’s computer every five minutes and upload this information to the government every two weeks [54]. This example gives an idea on how intrusive governments can operate and track the publics usage of the internet.
Methods of Internet Censorship
Filtering is a key process for creating internet censorship. Most Web filters use blacklisting and keyword blocking techniques to filter out the undesirable web pages. (See above to view blacklisting Privacy Laws) A blacklist is a list of web sites that are deemed undesirable by the companies that make the software or the governments who use web filters. Keyword blocking filters examine the words searched by the user on search engines like Google or Bing to determine if the web pages are inappropriate. In 2017, most internet providers like Sky or BT offer the option of filtering through parental controls settings, users can decide to restrict access to dangerous sites like pornography, chat rooms or gambling. This filtering is used to control what children can view on the internet, censoring any inappropriate information. Government filtering shares the same principle as parental controls but on a much grander scale, the general population is portrayed as being the children in this circumstance.
With 721 million internet users in 2016 [55] the Government of the People’s Republic of China have an enormous job of keeping track of users viewing undesirable information. Hence the “Great Firewall of China” [56]. Firewalls act as a security system that controls and monitors the network traffic of users based upon the security rules of the company or government servers installed on [57] . It often acts as a barrier against any unwanted or potentially harmful websites. Due to the restrictive content of the internet by firewalls in China, a growing number of users rely on virtual private networks (VPN’s) to gain more freedom on the internet to visit sites like Facebook or YouTube which are often blocked by the government. However, the Chinese government in 2017 is reportedly stepping up the fight against illegal VPN’s in a bid to discourage the population from western media [58].
Pros and Cons of Internet Censorship
It is difficult to argue that there are positives for invading user privacy just because the information seems undesirable to government ideals who then make it inaccessible for other users to see or share. But there are some nonetheless.
Pros
• It creates a safe environment for children using the internet. With the average age of kids receiving their first smartphone at 10.3 years [59] old, access to the online world is becoming increasingly easy for children to reach. Censoring filters help eliminate any inappropriate information that could be viewed by kids.
• Strict censorship filters show potential in discouraging illegal activity online, as it makes it extremely difficult for users to illegally download movies and music. It also has a low risk of user accounts being hacked due to the level of firewall security.
Cons
• The main con about Internet censorship is that it discourages freedom of individuality and self-expression. The internet is a creative network with individuals coming together to create new ideas or expressing opinions, censoring these creative instincts will diminish any opportunity for cultural and social growth.
• Censoring information may lead to a stalemate of knowledge growth. The internet holds a vast amount of information in web pages and it can be complicated to decide what sites show useful or harmful content. So, governments will block and censor harmful content but in the same process might block pivotal information. For example, some keyword blocking filters have struggled to understand context. A simple search of “chicken breast recipes” will single out the word breast and deem it as an inappropriate search.
Top 20 Worst Countries For Internet Freedom[60]
| Countries | Ranking | Internet Freedom Score (the less the better) |
|---|---|---|
| China | 1 | 88 |
| Syria | 2 | 87 |
| Iran | 3 | 87 |
| Ethiopia | 4 | 83 |
| Uzbekistan | 5 | 79 |
| Cuba | 6 | 79 |
| Vietnam | 7 | 76 |
| Saudi Arabia | 8 | 72 |
| Bahrain | 9 | 71 |
| Pakistan | 10 | 69 |
| United Arab Emirates | 11 | 68 |
| Gambia | 12 | 67 |
| Thailand | 13 | 66 |
| Russia | 14 | 65 |
| Sudan | 15 | 64 |
| Kazakhstan | 16 | 63 |
| Egypt | 17 | 63 |
| Belarus | 18 | 62 |
| Myanmar | 19 | 61 |
| Turkey | 20 | 61 |
This table shows the top 20 worst countries in the world for freedom online. China tops the chart due to its extensive censorship and its crackdown on social media, discouraging many users [61]
Surveillance
[edit | edit source]For most of us, posting information online is a part of our daily routine. We use the internet to stay connected with our friends and update the people closest to us about what is going on in our lives. When we post something online we don’t assume that it goes further than the people we intended it to. However, this couldn’t be further from the truth. Our personal information, even that which we don’t make absolutely public, is being tracked and can be accessed by the government and third-party-marketers.
All of the information contained within the tweets we write, the emails we send or the photos we upload is comprised of metadata. Metadata is “increasingly a fundamental aspect of our modern existence, as it records the shape of our lives and then reshapes life accordingly”. [62] Metadata gives information about other data, so that includes the date, time and the IP address. With this in mind, through the information we post online whether it be via a laptop or mobile phone, we could be tracked down very easily and quickly.
Data Surveillance
[edit | edit source]Data surveillance can be defined as “the collection of information about an identifiable individual, often from multiple sources, that can be assembled into a portrait of that person’s activities.” Due to the fact that a majority of computers automatically store and track data our online activities leave behind what are known as ‘data trails’. These data trails make it simple for organisations to gather information about us, including our current location, without us being aware of it. Jay Stanley and Barry Steinhardt believe that it will soon be possible, due to data surveillance, to gather and combine information about an individual so that their online activities can be recreated “with such detail that it becomes no different from being followed around all day by a detective with a video camera.” [63]
Investigatory Powers Act 2016
[edit | edit source]Receiving Royal Assent in November 2016, the Investigatory Powers act legalises the most extreme surveillance in the western world. The act allows police and intelligence agencies to hack into mobile phones and computers regardless of whether the person under scrutiny is suspected of wrongdoing or not. The main purpose of the act is to counter terrorism and catch criminals however Julian Huppert, former MP and lecturer, states “some of the powers in the bill are deeply intrusive, and with very little possible justification. All of us want to be safe, and protected from terrorists and the like – but the evidence that these powers are all needed is thin indeed. However, the cost to all of our privacy is huge.” [64]
The act has come under scrutiny and privacy groups are challenging the powers set out by the act in the European court of human rights. These groups have argued that these powers are more applicable to a dictatorship than a democracy because citizens can be monitored and analysed closely. Chief executive of the Big Brother Watch, Renate Samson, stated "none of us online are now guaranteed the right to communicate privately and, most importantly, securely.” [65] Whilst the act is in place to monitor illegal activity and fight back against criminals, it opens up the opportunity for everyone to be monitored. Sometimes we post information online or search for topics which can be misinterpreted by someone who doesn’t know us. This could potentially put us in a difficult position if we are being watched so closely.
Personal Information Online
[edit | edit source]Nowadays, online users, without realising it, may be revealing a huge amount of personal information to other internet users. This of course can be advantageous but it also has many disadvantages. Personal information could be used against the user, which could be potentially dangerous or damaging to their reputation or status. While many users take particular precautions to prevent exploitation of their information, it remains extremely difficult for them to stay invisible online.
In July 2013, Princeton Survey Research Associates International conducted a survey along with Pew Research Center’s Internet Project, in which 1002 adults above the age of 18 were interviewed about their personal information online.
“For results based on the total sample, one can say with 95% confidence that the error attributable to sampling is plus or minus 3.4 percentage points and for the results from 792 internet and smartphone users in the sample, the Margin of error is 3.8 percentage points.”[66]
| Personal Information | % of adult internet users who say this information about them is available online |
|---|---|
| A photo of you | 66% |
| Your birth date | 50% |
| Your email address | 46% |
| Your employer/company you work for | 44% |
| Things you’ve written using your name | 38% |
| Your home address | 30% |
| Which groups/organisations you belong to | 29% |
| Your mobile phone number | 24% |
| Your home phone number | 21% |
| A video of you | 21% |
| Your political party/affiliation | 20% |
The survey continues to look at some of the users’ problems that they have encountered in terms of breaching of security. Their online visibility became inflicted and personal information had been stolen from a vast amount of the users. Email and social media accounts had been seized, Social Security/credit card numbers had been exploited, as well as stalking, harassment and victimization being taken place.
- 21% of internet users have had an email or social networking account compromised or taken over by someone else without permission.
- 13% of internet users have experienced trouble in a relationship between them and a family member or a friend because of something the user posted online.
- 12% of internet users have been stalked or harassed online.
- 11% of internet users have had important personal information stolen such as their Social Security Number, credit card, or bank account information.
- 6% of internet users have been the victim of an online scam and lost money.
- 6% of internet users have had their reputation damaged because of something that happened online.
- 4% of internet users have been led into physical danger because of something that happened online.
- 1% of internet users have lost a job opportunity or educational opportunity because of something they posted online or someone posted about them. [67]
The survey reveals that 86% of online users have tried to use the internet with different methods to minimalize their online visibility, whether it was from hackers/criminals, advertisers, certain friends or people from their past, employers, the government or from the people who run the websites they visit.
| Strategies people use to be less visible online | % of adult internet users who say they have done these things online |
|---|---|
| Cleared cookies and browser history | 64% |
| Deleted/edited something you posted in past | 41% |
| Set your browser to disable or turn off cookies | 41% |
| Not used a website because it asked for your real name | 36% |
| Used temporary username/email address | 26% |
| Posted comments without revealing who you are | 25% |
| Asked someone to remove something posted about you | 21% |
| Tried to mask your identity | 18% |
| Used a public computer to browse anonymously | 18% |
| Used fake name/untraceable username | 18% |
| Encrypted your communications | 14% |
| Used service that allows you to browse the web anonymously | 14% |
| Given inaccurate information about yourself | 13% |
Online Shopping and Banking
[edit | edit source]Online shopping is a type of electronic commerce that allows digital users to purchase goods or services online, on internet websites or applications run by retailers or vendors. This can be done on computers, tablets and smartphones.
Online banking is a digital payment system that allows users of a bank to make financial transactions through the banking website or application. This can be done on computers, tablets and smartphones.
Certified websites prove their security by including a ‘https’ at the beginning of the URL.
“Hyper Text Transfer Protocol Secure (HTTPS) is the secure version of HTTP, the protocol over which data is sent between your browser and the website that you are connected to. The 'S' at the end of HTTPS stands for 'Secure'. It means all communications between your browser and the website are encrypted. HTTPS is often used to protect highly confidential online transactions like online banking and online shopping order forms.”[69]
Some web browsers also display a yellow padlock on the toolbar to indicate security.
However, on some online shops, this ‘security’ isn’t displayed. While some companies may be completely genuine and moral towards customers and their personal information, other online users can exploit the websites and obtain this information. This information can be used unethically, and be sold to advertisers who contact their ‘new customers’ via email, text or post with ‘offers’ and company information. While this isn’t harming the victims, it can be seen as immoral and annoying. In alternative situations, people can steal personal information and commit Identity theft. No banks are completely secure and once a user’s information is compromised, it can take sometimes years to correct the damage, and can even cost a lot of money to fix.
Privacy and Leaks
[edit | edit source]Ess (2009) argues that “many people assume that their email communications are more or less private.” [70] However, he notes that although the emails we see don’t contain much information – just the content, the email address, a time stamp – they do in fact contain a lot of information about ourselves that we perhaps would not like to share.[71] As most people are not aware of the extent of personal information they’re sharing, this can lead to problems when they are hacked. This section will investigate case studies of celebrity and non-celebrity hacks in order to demonstrate the broader social consequences and impact of hacking private information.
Spyware
[edit | edit source]What is Spyware?
[edit | edit source]
In Adrian Athique’s Book “Digital Media and Society” he claims that at least 89% of computers and infected with spyware.[72] There are multiple kinds of spyware with varying objections, but spyware overall can be defined as a piece of software that was undesired by the installer. It falls under the category of malware, meaning it is designed to intrude the software and is of malicious intent. Spyware often “piggybacks” with instalments that the user chose to make, and can infiltrate a device undetected. It is used to gather information on the user, be it something as small as their browsing habits, all the way up to their security details and bank numbers. Spyware is the main culprit in the majority hackings, as it allows passwords and other such private information to be collected and stolen discreetly, most often unbeknownst to the victim. The first recorded usage of the term “spyware” was coined in 1995, contained in a post mocking Microsoft’s business model, and it was continued to be used in reference to the malware that was becoming more and more frequent.[73] Subsequently, the first anti-spyware (“OptOut”) was created in 1999 after Steve Gibson of Gibson research suspected that his software had been infected and was stealing his personal information.[74] Since then, anti-virus software has become a prominent part of internet usage. A study conducted by Microsoft in 2013 found that computers that browsed without anti-virus software were (on average) 5.5 times more likely to become infected.[75]
The Dangers
[edit | edit source]There are several consequences that can follow a device being infiltrated with spyware. Software that has been affected doesn't necessarily mean that this results will occur, as they are the most severe result and therefore the worst-case scenario, but each instance does still run the risk.

- Keylogging: Keylogging is the act of tracing what the user is typing, as it records each key as it is pressed and in what order. A lot of spyware is programmed to flag up any succession of numbers that resemble card numbers, but it is also used for finding out users password and other confidential account details. A device that contains keylogging spyware is unsafe to use for any form of money transaction, as well as anything password-sensitive.[76] Keylogging, however, isn't just restricted to spyware that sneaks in through other instalments, as it can be achieved through external hardware plugged into the computer itself. This form of keylogging is often committed by employers or parents that want to keep a track of what employees/children do with their time online. These hardware devices are commonly plugged into the USB port of the computer and are easy to recognise after being made aware of them.
- Identity Theft: This is when a real-life identity is stolen and used to commit fraud. Through spyware, enough personal information on the user can be gathered which then allows their identity to be stolen by another. Identity theft can be used for taking out loans, applying for jobs, catfishing other people and other high-risk acts that can leave the victim with irreversible damage. A recent study revealed that in 2015, 13.1 millions U.S citizens collectively lost over $15 billion as a direct result of identity theft, which averages to roughly $1,145 per person.[77]
- Loss of System Performance: When a device is infected with spyware, performance quality can take a massive as a result. This can cause difficulty connecting to the internet, a slower running speed, as well as frequent crashing. Spyware is the leading cause in trips to professional repairers, as it can cause a 50% decrease in performance[78] in the most severe cases, it even becomes an "invisible" cause, therefore very few understand why the loss of performance quality has even occurred.
Google AdSense
[edit | edit source]One potentially disturbing fact frequently gets lost amidst debates about the fate of privacy in the digital era and the crossfire between celebratory and critical claims about the online economy; namely, the emerging commercial model for the interactive economy has become reliant on the prospect that information-based target marketing and data mining will be increasingly effective in manipulating and channeling consumer desire
Google AdSense is designed to generate contextual advertising. Through the use of Google AdSense, companies and sites can pay to advertise a more targeted audience, as Google AdSense tracks the browsing history of the consumer and then presents them with advertisements that are relevant to their previous searches. This is turn produces a larger amount of clicks, and allows Google to charge more for displaying adverts as opposed to general advertising. As mentioned, this functions through the use of browser tracking. While this wouldn't be considered spyware, as Google AdSense isn't a separate feature installed into a device nor does it have malicious intent, this still causes discomfort among users as this form of advertising and the process behind it isn't considered common-knowledge and many are unaware of the search-tracking that takes place.
Due to many spyware programs being designed to: 1. Track browsing habits and 2. Cause pop-up advertisements, it is fair to be sceptical of Google AdSense. Benjamin Edelman is a professor at Harvard Business School who looks into how online markets function[80], and found that the "pay-per-click" function of AdSense was being exploited through the use of spyware. AdSense partners were paying a company (180solutions) that was considered spyware to project their advertisements through unwanted pop-up adverts, increasing the number of clicks and therefore their revenue. While Google was not actively encouraging the use of spyware in these situations, they failed to prevent it and allowed their system to be exploitable through spyware and inadvertently caused an increase.[81] It also can't be known if the spyware's function was solely dedicated to the creation of pop-up advertisements, or if they were simultaneously keylogging or stealing personal information, creating a potentially even severer scenario.
Celebrity Scandals
[edit | edit source]Some of the most popular scandals is Janet Jackson and Justin Timberlake’s in the 2004 Superbowl performance. [82] After announcing that it was "an accident" many people on the media started saying that was well planned and not an accident at all. Theories say that the reason it was planned is because it started bringing a lot of attention to the half time shows therefore it brings in more people to watch the Superbowl. Things that are contractual mostly happen in the half time show another example in relating with this is when Beyonce's halftime show in 2016 [83] many people started saying that it was a political statement about the "Black lives matter" movement and this brought a lot of controversy to the Superbowl. Some controversy is wanted to bring more attention to something however it only become a problem when the publicity is unwanted this can have negative effect on someones life if they are tying to live out of the light of fame.
Some of the famous people do not wish to share details about their private lives. For example Emma Watson stated many times that she wishes to keep her personal information about her life private.[84]
I don’t think it’s fair that, all of a sudden, intimate details of their personal life are public as a direct result of me…I wish I could protect them.”
However, some reporters do not respect that request and choose to publicize about her private life.
- That is not the only consequence of over sharing information. One of the most recent stories that made headlines is the Kim Kardashian robbery at gunpoint on the 3rd of October 2016, this was one of the most talked about news at the time. Kim Kardashian decided to stay out of the social media spotlight for a while to protect herself hand her children from future attacks, she also said that she would be a lot more careful of what she posts and shares with everyone. this was a huge wake up call to the whole family about oversharing personal information. [85]
Young Public Figures
[edit | edit source]This is especially a problem when it comes to younger celebrities. The best example that explains this point is how social media reacted to Malia Obama smoking as people thought that it was un-properer for the first daughter to do such action however it should have not even be reported on because even though she was the presidents daughter she is still considered a private citizen. Whatever she chooses to do in her private life even though they disagree with it. [86]
Another example is Macaulay Culkin who was the young boy who acted in Home Alone however, as he grown older some false accusations about him started to spreading that he got into doing some heavy drugs however he only experimented with some drugs but never got addicted or needed to go to rehab. This can corrupt to someones image in the public eye as many people judge others based on how the media presided them. [87]
Moreover, the son of action hero Will Smith and actress Jada Pinkett Smith has been the subject of cruel rumours that he has committed suicide, with a 'video' being uploaded to Facebook which claimed to feature him saying goodbye to his famous parents. [88]The hoax involves getting permission to post on the user's page on the social media site, and it has been spread for weeks now, with people noticing it on their news feed as more and more people click on the fake link. However, this kind of event will cause some seriously negative effects to children both psychologically and mentally.
Photo Scandal of Hong Kong Actor Edison Chen
[edit | edit source]In February 2008, intimate and private photographs of Hong Kong actor Edison Chen with various women, were illegally distributed over the Internet. The scandal shook the Hong Kong entertainment industry and received high-profile media attention locally and around the world. Edison admitted being the author and copyright owner of most of the photographs, and stated that the private photographs had been stolen and published illegally without his consent. He made a public apology, especially to the women involved, and also announced that he would "step away indefinitely" from the Hong Kong entertainment industry.
At this time I am not able to discuss matters related to the case, but I do feel it is my obligation to accept full responsibility and take action to help both the victims and those associated with them to heal their wounds.
In this regard, I plead with everyone to please stop forwarding the images on the Internet. Furthermore, to completely rid the images from your computer...
The news of the scandal received international media attention, notably on the Wall Street Journal [90], the BBC [91], The Guardian [92], and Der Spiegel [93].
- Impact and Consequences:
The scandal has shocked the general public and ignited debate about sexual morality. The blanket coverage of the local press, their reporting style, and the appearance of photographs has also been met with public complaints to television and entertainment licensing authority. This event had a great influence on celebrities and the society, which affected people’s life and seriously violated the privacy rights of the celebrities.
South Korean Stars Commit Suicide After Internet Rumours
[edit | edit source]In South Korea, the online libel cases rose to 10,028 in 2007 from just 3,667 in 2004. Iconic Korean actress Choi Jin Sil, who apparently succumbed to a suicidal impulse provoked by malicious online rumours, and police examining the case concluded that Choi, who told an interviewer that she "dreaded" the Internet, was driven to suicide as a result of the vicious web rumours, which also homed in on her bitter divorce and single- mother status. [94]
- Impact and Consequences:
While online rumours can prove fatal for some celebrities, malicious Internet rumours are being blamed for the rash of celebrity suicides in South Korea that has prompted its government to put forward a controversial new bill to punish derogatory online comments. "Internet space in our country has become the wall of a public toilet," commented Hong Joon Pyo, a senior politician in the South Korean government. For years, whether and how to regulate the Internet has been a hot topic in South Korea, where almost 80 percent of the households have broadband access. Here, most Web portals and online news sites have discussion boards where users can post uncensored, anonymous comments. Some news articles attract hundreds of feedback entries, ranging from thoughtful comments to raving obscenities. [95]
This issue was not only limited to South Korea, it was world wide, Celebrities who faced false accusations or got too much exposure about their lives not only go through depression but they also increase the intake of drugs.
iCloud hack 2014
[edit | edit source]In 2014, there was a hack into the iCloud system which, according to Apple, was “targeted” at celebrities’ accounts.[96] Apple was quick to announce in a statement that the attack didn’t compromise the iCloud system but rather solely the specific accounts of celebrities, however, Kovach (2014) notes that this doesn’t explain how the hackers were able to get into those accounts.[97] This hack therefore affected celebrities only and triggered a wide range of different responses and opinions. The information leaked that got the most attention was the nude photos of female celebrities including Jennifer Lawrence, Kate Upton and Kirsten Dunst.[98] Some of the photos circulating at the time turned out to be fake, presumably created by people jumping on the bandwagon in order to get recognition, but many were confirmed to be real.[99] The photos were spread all over the internet on sites like Imgur, Reddit and 4chan. This led to debates around privacy and whether viewing these photos and seeking them out, despite not having personally leaked them, made an individual complicit in the violation. For example, in this opinion piece from The Guardian, Badham (2014) argues that circulating the photos is “an act of sexual violation.”[100] She also argues that:
- “The need for privacy is not only a sacred place to work out who we are, what we do or how we think; it’s a psychological refuge from overwhelming public dissection necessary for anyone’s mental health, famous or not.”[101]
This argument ties into much of the dissent and outrage from many public figures, including celebrities and journalists. Emma Watson and Lena Dunham were among the female celebrities who spoke out, requesting that people not look at the photos and talking about how it was a violation of privacy.[102][103] Meanwhile, several publications spoke out against the public reaction towards the nude photos, calling for people to stop circulating them and stop using crude language to describe the breach of privacy. [104]
In the aftermath, Apple was keen to assure their users that their privacy was not in jeopardy. The BBC reported that Apple had added an extra step of log-in verification[105], while Forbes encouraged users not to delete their iCloud accounts and remove their information, but rather to up their security measures such as using more complex passwords.[106]
Non-celebrity hacks
[edit | edit source]Ashley Madison data breach
[edit | edit source]There was an attack on 15 July 2015, they threatened to reveal the identities of Ashley Madison's users.[107] This site was basically for those who were married or in relationships to cheat and have a safe place to contact one another without their significant others finding out about them. This was one of the most recent attacks of private citizens' privacy. Although many cheated the hackers and stood by them saying that cheating was wrong so sharing their personal information was not much of an issue as it seemed justified with many people. This resulted in many people to lose their families, jobs and relationships.[108]
Yahoo! hacks
[edit | edit source]Yahoo! is a technology company whose services include Yahoo! Search, Yahoo! Mail, Yahoo! Answers and many more. It also owns Flikr and Tumblr. Yahoo! users are able to access all Yahoo! services as well as to link with Tumblr and Flickr accounts. This means that when a user’s security is compromised, the hacker has access to the information provided by the user across several services, which may include bank details.
When Yahoo! was hacked in 2013, one billion accounts were accessed by a government hacking programme, according to several news sources. [109][110] Not much information has been provided from Yahoo! about who hacked them and why. [111] However, we do know that the hackers were able to access “names, email addresses, telephone numbers, dates of birth, hashed passwords.” [112] There was also a hack in 2014 by the National Security Agency (NSA) which the company allowed to happen. [113] The NSA used a similar programme to Prism, the surveillance programme revealed by Edward Snowdon and they also requested that Yahoo! search for a certain “set of characters” in the emails going through their servers. [114] According to Woolf (2016), this is the only known time that a company has agreed to letting a spy agency access their information. [115] After investigations of these subsequent hacks, the head lawyer of Yahoo! has resigned and their CEO has lost their bonus.[116]
Ess (2009) talks about breaches of privacy in relation to government intervention. He argues that "Governments may be (somewhat ironically) the worst culprits" for hacking private information.[117] Weber (2012) argues that “the most important objective of privacy is the prevention of improper use of personal information” [118] Therefore, these hacks carried out by government agencies must justify their surveillance programmes, however, we have yet to have an explanation of what they were looking for in Yahoo!. Conversely, so long as the agencies are managing that information securely and appropriately, the argument can be made that their intervention is justified.
PlayStation Network Hack
[edit | edit source]
In the early months of 2011, Sony's PlayStation Network went offline, and after seven days[119] they went on to admit that it was the direct result of a hacking. At the time of the hack Sony had an estimated 70 million users[120] registered under the network, resulting in the possible breach in security of the personal information of millions. Sony explained that in the hack, user details were potentially left exposed. This included names, date of births, addresses, as well as card details due to the network being used for the purchasing and distribution of games, music, films and software.
Due to the delay between the hacking occurring and Sony admitting that personal details were potentially compromised, this left an expanse of time where users were unaware of the breach in their privacy and were left exposed to the consequences. While they claimed there was no evidence of card details being stolen, Sony warned: "Out of an abundance of caution, we are advising you that your credit card number (excluding security code) and expiration date may have been obtained."[121] The hacking was considered one of the largest security breaches in history, as well as being one of the biggest intrusions within a store of credits cards, as only sites such as Amazon, PayPal and iTunes are known to store more.[121]
Privacy in Relation to Living in a Connected World
[edit | edit source]The Online/Real-Life Divide
[edit | edit source]As discussed in the full chapter of the same title, there is a new understanding of the way people present themselves online because of the rapidly changing and growing technological culture. But how well are we coping with the ability to remain private with these constant changes?
At first glance there would be an obvious divide between the online and real life divide, but with the rise of social networks and the technology to be on the internet at any time of the day and almost anywhere, the boundaries of online and offline privacy are starting to be minimised and potentially blurred. The privacy that some people strive to keep online sometimes isn’t as private as it should be because the privacy settings on some social networking sites are incredibly relaxed, and still reveal quite a lot about a person, whether via another account or not. This then leads to a question of security, whether people are online or offline.
Because a lot of people are able to access the internet and their preferred social networking sites via apps on their phones, their locations can constantly be pinged and their movements tracked, and no matter how private they keep their original pages a lot can still be seen by people who are essentially strangers. In real life, it is much easier to keep privacy especially if people are offline – it is much like living in a house, if privacy is truly wanted, it is just a case of locking the doors and closing the curtains. Online, this privacy is much harder to achieve as despite putting the privacy settings on to what could be considered as the optimum, for a lot of social media networks a lot of personal data can still be found online, and what is more shocking is that there are sites where information can be found which was gathered offline.
One of these sites is 192.com [[14]] where the electoral roll of people in the UK is stored and people are able to search and find anyone of interest to them. Before the internet, people had to register to vote by post (something which is still an option today)[[15]] but with the ease of applying online, anyone can sign-up and keep their addresses up to date with no problems whatsoever. As this service makes it easier to check the immigration statuses and movement of people throughout the country, it also means that the information uploaded can be searched for by any Tom, Dick or Harry on Google looking for anyone they want. As a funny pastime for a lot of primary school children, searching for each other or for family members was fun and not easy and would start a lot of laughs and giggles because of all of the random pictures that would appear which were clearly unrelated... little did those children know how quickly the change in technology would be and how easy it is for them (now as adults) to do the same search, but find more than they realised was available. Most of the information online is something that some people willingly share, but others who strive for the utmost privacy – online and offline – will be very surprised at the things they can find, especially when there are plenty of loopholes. For example on the same 192.com [[16]] website, typing in the name of a certain person might give search results of a few people and just a green tick next to the ‘home address’ box which, when clicked would lead to a sign in/ sign up page for further information, but type in said same name on Google, and clicking on the link to the same site will give you the rough address and list of other/ former occupants at the address too. If people are striving for privacy online and offline, here is a number one way to ensure that it is already lost to a certain degree, and without their permission.
Another way in which privacy between the online and real-life divide is challenged is the ease of access to the internet itself, and through the different platforms it is available. For some people, they prefer gaming and having more anonymous profiles which only their friends in real life can be friends with, though are able to connect with other people online and playing the same game, and for the rest, they may choose every available platform for social networks. The privacy is challenged here as a lot of people can also be at home when they are online which can mean that they can potentially be tracked through their activity too. Slightly linking to the surveillance section above – no form of the internet is not in some way being watched, especially via social networking sites which are free to sign up for. ‘These services are free because they are selling access to you’ [122], which means that the advertisements that appear are specifically tailored because of the search history or general activity related to anything shared, it also means that every conversation is monitored and that privacy is almost non-existent. This is different from the real-life divide as not everything will be monitored, and not all of the adverts passed will be tailored, but would rather just pass unnoticed - which is quite a feat considering that the average person is exposed to 3,000 to 20,000 adverts a day [123]. There is more freedom in the real-life rather than online, as there is also the possibility of being whoever you want to be, and either be noticed or not as privacy in reality (and being offline) means that there are infinitely less worries about someone hacking any devices used for socialising, or someone making sure that you are not some sort of terrorist spy.
Privacy in relation to the online/ real-life divide is by far and large something that is slowly vanishing with the technological advances modern societies are developing, which means that before long, there will be no privacy in the real life either, rather than just a false sense of privacy online.
Technology as an Extension of Self
[edit | edit source]As previously discussed in the chapter on Technology as an Extension of Self, users of modern day technology and social media are willingly and unwillingly giving out personal information and details more and more. Those with accounts on common social media sites such as Snapchat, Instagram, Facebook, Twitter and Youtube are becoming increasingly invested, and private lives and online lives are being further merged the more time is spent online.
Youtube
By far the most prevalent example of the blurring boundaries between private and online personality is the recent inflation of Youtube Vloggers. Arguably the most popular type of vlog (short for video blog) that is uploaded to Youtube is the day-in-the-life type montage, that can showcase the creator doing anything from making breakfast to snowboarding through New York City. This moving image, diary-entry style of content differs considerably from Facebook statuses or Instagram posts, the videos are typically around 5-15 minutes long, the most popular getting millions of views and provide a real insight into what for most people would be seen as a private day in the life.

Casey Neistat found filmmaking fame through the vlogs he uploaded to the site every day for almost 2 years, which earned him over 5 million subscribers and billions of views. He documented his adrenaline-filled lifestyle in New York with his family and friends and showcased his apartment, workspace, holidays, meetings and more to his growing audience online. An increasing number of viewers of his videos began turning up outside his office for a chance to be in the “vlog” as his following grew. Neistat stopped his daily videos in November 2016 and now focuses on uploading short films more sporadically.
Youtube stars and celebrity couple Zoe Sugg and Alfie Deyes, known online as “Zoella” and “PointlessBlog”, also vlog their daily lives. Both started on the platform over 5 years ago and have accumulated over 15 million subscribers between them. The majority of their vlogs take place in the home they share in Brighton, and although care is taken to not show the front of the house or the surrounding streets, often is the case, like with Neistat, that fans of their vlogs do turn up uninvited. In 2015 the couple took to Twitter to voice their complaints about a lack of privacy after the location of their house was revealed through their videos:
Although the majority of fans agreed with the pair, a lot hit back at them for not realising the price that comes with fame. Although not conventional celebrities, the amount of personal details Youtube creators intentionally and unintentionally upload online, particularly in the form of day-in-the-life videos, blurs the line between a private life and a public one excessively. Sugg often gets very personal in her videos, speaking out about her issues with anxiety and expressing how she often finds the lack of privacy and newfound exposure overwhelming.
Persistent Connectivity and the Fear of Missing Out
[edit | edit source]Both the concept of the Fear of Missing Out and privacy issues are described by Nancy Baym as “cultural anxieties”[124] caused by new media. Most of the popular understandings of privacy are related to the concept of isolation, or the ability to feel alone and cut off from others.[125] Missing out has direct links to privacy. Having strong privacy settings reinforces these ideas and feelings of solitude, and the subsequent concept of the fear of missing out on things. There is a sense of mass panic on not having a “window to the world”[126] through social media platforms, and this window shrinks even further when information becomes increasingly private. There is a sense of dissatisfaction when we aren’t allowed access to a certain page or account due to the privacy settings. Friends and followers influence others behaviour online, the more information that is open to each other, the more the fear of missing out is heightened. Michael Hogan Ph.D. notes that a decrease in personal privacy is a fundamental driver of the negative consequences of FoMO.
In an age where Facebook is the platform where the majority of planning, organisation and discussion for projects, events and clubs takes place, barriers of privacy have to be broken down in order to contribute. Often is the case where accounts will friend and follow people not necessarily known to them personally, in order to be invited into something, or joined onto a group chat. It is the simple logistics of the website, yet friending someone to communicate with them is also opening up to them everything that account posts, and all the information, photos and details already on the profile. This is particularly prevalent in students, where University project groups, sports clubs and societies often require them to be more relaxed in adding people on Facebook to stay in the loop. Focus group discussions with young people show that they have an increasing dislike for Facebook due to issues of people sharing excessively, yet keep using it because participation is an important part of overall teenage socializing.
The effects of oversharing on privacy controls
The 2008 word of the year according to Webster’s World Dictionary was “overshare”.[127] Too much self-disclosure is becoming an increasing problem in social media in the modern day, and the nature of it also has a direct effect on privacy controls. Sue Scheff explains that posting on social media “excessively” can increase the possibility for people, especially teenagers, to be negligent with their privacy controls, even if it is accidental[128]. Oversharing is more effective the larger an audience an account has, and privacy settings can determine the difference between the size of followings. Jaron Lanier suggests that users should never "post anonymously unless you really might be in danger", in order to stay as a "person" online and not a "source of fragments to be exploited by others"[129]. The more advanced technology becomes, the more its users become less private.
“if we became digitally abstinent tomorrow, the vast amounts of personal information already available would render us vulnerable for decades to come[130]
Out of the most popular social media groups; Facebook, Instagram, Snapchat and Twitter, Twitter is the platform in which user’s privacy controls are at their most relaxed. The data that Twitter stores from individual accounts is fairly comprehensive, but while Facebook profiles tend to have the most private settings enabled, Twitter users are much more likely to have a public account . A Pew Research Centre Study on teenagers and their privacy controls on social media concluded that whilst 60% of teen Facebook users have private profiles, 64% have public twitter pages. The number of teens using Twitter has also increased by 8% since 2011. Twitter is a platform in which information spreads the fastest and most easily, especially when privacy settings are at their most lax, due to its Retweet function. Retweeting allows someone else’s tweet to be shown on your account to all of your own followers, and only works if the original account who tweeted it, doesn’t have their account on private. Retweets are described on Twitter’s Help Centre as a re-posting feature that “helps you and others quickly share that Tweet with all of your followers”[131]. The retweet feature is not available for accounts that are protected.
“If you see the lock icon next to a user's name on their profile page or on their Tweets, their Tweets are protected and you will not be able to Retweet their content”[132]
In terms of | virality, a single tweet can rack up thousands of interactions in the space of a few hours if it’s been retweeted enough, but it wouldn’t be possible for an account with “protected tweets” to achieve as much recognition. Because protected accounts have chosen not to share their Tweets publicly, their Tweets cannot be Retweeted by anyone else. A non-private page allows further interaction and involvement with others on the site, whether this be with real-life friends or not. A protected account is one that can heighten feelings of FoMO more so than a public one.
Digital Labour on Social Media Platforms
[edit | edit source]Where would one be if one did not have access to social media? This question tends to be asked by many people nowadays as so many individuals rely on social media and the Internet so heavily. Social media plays a huge part on the majority of people's lives. The Internet as a whole, has become thoroughly embedded and routinized in the societies where it is most likely to be used, according to Frank Webster. This includes societies and environments such as workplaces and educational facilities whereby the Internet is almost second nature to its users. But the reality surrounding how this digital world is created is one in which seems to go unnoticed. Technologies altogether have played a huge part in the restructuring of capitalism since as far back as the 1970s. One would say the world of technology allows rapid communication which is required for organising international markets and value chains. Nick Dyer-Witheford therefore describes the value chain as “the dirty secret of the digital revolution”. The clean, immaculate and advanced surface of modern computer products hides the dirty reality of their production process. Concepts such as “digital sublime” [133] or “technological sublime” [134] suggest that certain myths and utopian ideals are attached to media and communication technologies. Maxwell and Miller argue that this has as a consequence that the “way technology is experienced in daily life is far removed from the physical work and material resources that go into it” [135].
To elaborate on the point made by Frank Webster, the Internet has not replaced older forms of media completely. He believes that people's information and communication environments have become increasingly more individualised. Throughout this Wikibook exercise, Dr Thomas Allmer posed a question which would make one "consider how do the constraints and emancipatory potentials of new media look like and to what extent can digital and social media strengthen the idea of the communication and network commons and a commons based information society? [136].
New media studies demonstrate a variety of ways in which a mass society has been transformed into a new and emergent environment of networks, dynamics, roles and relations. As Marisol Sandoval states "Conceptualizing digital labour only as mental and immaterial labour misrepresents the character of ICTs and digital technologies as it tends to downplay the physical and manual labour that goes into them" [137]. Sandoval's statement acknowledges the fact that in order for us, as social media and internet users, to be able to maximise the use and make the most of this digital world one is exposed to, one must realise that the process of this does not just happen without hard work. Dyer-Witheford states that the social factory is a "factory without walls" [138] as capital extends exploitation to networks, it also automates the entire social factory of human society. These developments within the social factory cause a restructure within the concept of traditional working-class. Dyer-Witheford proceeds to discuss that corporate social media platforms are social factories having extended logics of the factory to the Internet and have subsumed society and social activities into the capitalist process of the productions. Technological giants such as Facebook, Appleand Googlehave changed exploitative aspects from the workplace into cyberspace. Despite having said this, those who use social media belong to the social factory that work for free in their own time by fulfilling social and communicative needs. The entirety of anything regarding social life is subsumed under capital on the Internet. Despite the fact that productive forces of social media are shaped by value creation in capitalist societies, the continuous development and progression of productive forces signify the opportunities of the commons within different relations of production.
How does this relate to privacy?
How does social labour relate to anything privacy related one may ask? To conclude and address this question, it must be said that the client-server environment which is taking over the Internet is built as a control and a piece of surveillance technology (which will be addressed elsewhere within this Wikibook) which is submerged in the capitalist relations of production. This specific technology could increase the risks and dangers of people who may not know where their data and information is stored and what is happening with it. It runs the risk of strengthening the sense of 'uncontrollability' of personal data and files. This possible danger is reflected when social media users admit their fears of social networking sites.
Filter Bubbles and the Flow of Information
[edit | edit source]
Definition
So what is a filter bubble? According to Techopedia, "a filter bubble is the intellectual isolation that can occur when websites make use of algorithms to selectively assume the information a user would want to see, and then give information to the user according to this assumption". So effectively, information is extracted from the user in order to present the most 'relevant' information for the user. The algorithms tailor what is shown to the user online and consequently decide on what is hidden.
The image on the left is a graphic which has been created to demonstrate the concept of a filter bubble. Although a filter bubble is not truly a physical object, by creating a visual way of depicting how a filter bubble functions the concept should (ideally) become clearer. The inner circle (with the yellow outline) represents the filter bubble. The circles inside of this demonstrate the information which gets filtered into the user's view. The white arrows pointing towards the centre represent the algorithms of different search engines, sites and platforms which control what is filtered through to the bubble, and in turn, what is kept out. The other coloured circles outside of the bubble are sites and information which the algorithms reject. This may be because they are assumed to be of no interest to the user or they present new, different or opposing concepts to that of the user's common patterns. This can stifle knowledge and form the metaphorical concept of tunnel vision as the user does not receive a democratic perspective.
This YouTube video entitled The Filter Bubble: How the hidden web is shaping lives provides insightful information on the definition of filter bubbles. It also draws upon the effect it has on the flow of information which is presented to the user. The next section discusses how this affects online privacy. More information on filter bubbles and the flow of information can be accessed in the chapter Filter Bubbles and the Flow of Information in this WikiBook.
How this affects online privacy
So, why is the relationship between filter bubbles and privacy important to consider? Zizi Papacharissi evaluates the meaning of privacy using terms such as: ownership, personal, domestic, unofficial and (structured around the) self. [139] But is this an illusion online? Filter bubbles extract information from the user which cancels out/changes the meaning of these terms. Online privacy in relation to filter bubbles and the flow of information remains "structured around the self" but in a different way to that which Papacharissi intends. This is because it is no longer personal, the user loses control over what is structured for them. Algorithms in the form of filter bubbles structure what is presented for the user and simultaneously, what is hidden from the user. The algorithms structure information around the user's information.
Amongst other subjects, Google is discussed in the afore mentioned clip (The Filter Bubble: How the hidden web is shaping lives). The speaker, Eli Pariser, highlights that Google acts not only as a search engine but as a platform to extract information from the consumer. This information is used to tailor searches to make the results more "suited" to the individual. If people X, Y and Z all searched for the same thing, the results would be different. The algorithms of the filter bubbles display what the user is most likely to want to see. User interest is based on click behaviour, browsing and search history and location [140]. This function assists and helps the user by breaching privacy as the user does not have a choice against sharing what they search, browse etc. Does this demean the user's control? This is the first example of how privacy relates to filter bubbles and the flow of information.
A primary factor in the relationship between privacy and filter bubbles is the distortion problem [141]. Due to filter bubbles deciding what is 'best' or 'most suitable', the user becomes unaware of how they are viewing the world and in turn what they are missing. Thus their perception is distorted. In the opening definition of filter bubbles the stress on relevance is stated. The matter of relevance is utilised constantly online. For example, Netflix advertises and suggests what you might be interested in watching next. Filter bubbles use information from the individual (and others who follow similar viewing patterns) to determine what the user is most likely to want watch next. The bonus of this is that the user has direct access to more of what they have proven to enjoy. However, this stops the user from seeing everything else. So filter bubbles may help the user to continue clicking on the same kind of media, hence, encouraging the 'always on' culture (see glossary). For a democratic view, the user must be open to a multitude of different opinions and information. Although the user may oppose this information, by viewing new and different ideas they can build a stronger view of what they do believe as they learn more about everything in general.
Essentially, the tug of war between filter bubbles and privacy comes down to a matter of control. If technology truly is an extension of self, then the user should maintain control over the technology [142]. The user should at least be aware of what information is being used and how it is being used. Filter bubbles were created for user benefits but they can spiral out of control since, after all, they are simply algorithms. They have no ethics or human thought processes. However a human did create them. And the sites which own them can use them how they please. If websites can use filter bubbles to control what the user has access to, then companies could easily manipulate this information for commercialisation.
Summary: Conclusion and Possible Solutions
The works of Papacharrissi and Lanier have been drawn upon in this article however there are many other theorists who recognise the complicated concept of online privacy.
“In modern society, privacy is inherently linked to surveillance.”—Christian Fuchs, Social Media: A Critical Introduction
As Fuchs highlights, there will never be 100% guaranteed privacy online. Data trails can and will be followed and used for reasons which may not affect the user or may alter what they see. So there may not be a distinct solution but arguably because this is not a distinct 'problem' - it is more of a situation which has appeared within modern society.
After much debate through doing this work, two possible conclusions have arisen:
1. Creating transparency.
2. Being able to turn filter bubbles on and off.
By having a transparent relationship between websites and the user then it should be clear what results are personalised and on what basis. If the user is aware of what private information is being used (and realises that it is not as private as they possibly first assumed) then in the future they can take care with what they search, browse and click on. Secondly, by having the ability to turn the filter bubbles on and off then user can regain control. The user could search with the filter bubbles off in order to receive a neutral response and then adjust this at their leisure. More work and research on filter bubbles and the flow of information could allow development to further secure online privacy in the future.
- DISCLAIMER - the above 'possible conclusions' have not been academically proven and are simply proposed theories.
How the different Generations are dealing with her Privacy on Social Media
[edit | edit source]This chapter based on a study, published by the 23rd International Academic Conference in Venice. The sample of the study consisted of 736 participants. This participants were selected through stratified random sampling from the research population determined as "Individuals who live in the province center of Konya and use any of the social media tools"
The behavior of the generations on the social media platforms is quite different, also their meanings about which stuff is to private to share there.
The generations are based on the range of birth dates and the classification by Greg Hammill (Hammill, 2005)
| Generation | year of birth | age range |
|---|---|---|
| Baby Boomers | 1946 - 1964 | 53 - 71 |
| Generation X | 1965 - 1980 | 37 - 52 |
| Generation Y | 1981 - 2000 | 17 - 36 |
At first we are looking at the behavior with their "body privacy"
Question 1: I share my photos in a swimsuit taken on the beach.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 71,9 % | 18,2 % | 9,9 % | 0,0 % | 0,0 % |
| Generation X | 77,3 % | 15,0 % | 7,3 % | 0,5 % | 0,0 % |
| Generation Y | 68,8 % | 13,9 % | 12,2 % | 4,1 % | 1,3 % |
Here you can see that 31,5 % of the Generation Y is posting such photos while 22,8% of the older Generation X and 28,1 % of the Baby Boomers are doing this. Based on this you can not say that the younger generations are sharing these photos more frequently than the older generations. But you can see that the number of people who would never sharing these is in the Generation X on the lowest level. The Generation X takes more care about there privacy here than about there self presentation, which is a difference to Generation Y.
Question 2: I share my home and it's rooms (including the spaces such as the bathroom, bedroom, etc.) together with the furniture.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 75,2 % | 19,8 % | 5,0 % | 0,0 % | 0,0 % |
| Generation X | 77,3 % | 16,8 % | 5,5 % | 0,5 % | 0,0 % |
| Generation Y | 72,7 % | 16,7 % | 8,6 % | 1,8 % | 0,3 % |
Here you can see that there is no significant difference observed by the different generations who answered, that the would never share their home and it's rooms together. 72,2% of the Baby Boomers, 77,§% of the Generation X and 72,7% of the Generation Y never would do this. It seems like protecting their home is something all generations consider as important. Maybe this is because they want to be safe in their offline world and do not bring there online life into this.
Question 3: I share my activities about the members of my family in a controlled way.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 10,7 % | 10,7 % | 21,5 % | 40,5 % | 16,5 % |
| Generation X | 4,1 % | 10,0 % | 21,8 % | 44,5 % | 19,5 % |
| Generation Y | 17,2 % | 14,2 % | 22,5 % | 28,1 % | 18,0 % |
Based on this answers you can see significant differences. While 57% of the Baby Boomers and 64% of the Generation X answered this this question "usually" ans "always", only 46,1% of the generation ticked these answers. The reason can be that the Generation Y is quite young and many of them are single and do not have children they use to protect. The Baby Boomers are mainly connected with family members and want to communicate with them, so the are sharing family activities to other family members. The Generation X just started to have children and want to share how happy they are and also share the pictures with other family members and friends.
Question 4: I wear and photograph the clothes I like and present them to my friends' taste.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 62,2 % | 19,0 % | 19,0 % | 0,8 % | 0,0 % |
| Generation X | 48,6 % | 33,6 % | 11,4 % | 4,5 % | 1,8 % |
| Generation Y | 33,9 % | 26,6 % | 24,1 % | 12,2 % | 3,3 % |
You cam see that 66,2% of the Generation Y and 51,3% of the Generation X are sharing these photographs, only 38,8% of the Baby Boomers are doing this. The number of people sharing these pictures are rising with the younger generations. The baby Boomers are defined as a contented and less consuming Generation. They grew up after the Second World War and are not that interested in fashion aspects as the Generation X, which were the first who are shopped in shopping centers. For the Generation Y the clothes and their brands represents who they are. The clothes are a part of the self-representation as in Rettenbergs "Seeing Ourselves Trough Technologie". It is really important for the Generation Y to be seen from others in a controlled way.
Question 5: I share/can share the photos of private moments I have with my spouse or beloved.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 52,1 % | 21,5 % | 21,5 % | 5,0 % | 0,0 % |
| Generation X | 49,5 % | 23,2 % | 14,5 % | 8,2 % | 4,5 % |
| Generation Y | 40,0 | 23,5 % | 17,0 % | 14,4 % | 5,1 % |
You also can see in this table significant differences between the generation. The willingness to share the "Private Relationship Status" is increases withe the younger generations. 48 % of the Baby Boomer, 50,4% of the Generation X and 60% of the Generation Y are sharing private moments with their beloved persons. The Generation Y grew up with personal computers and smartphones. It is a part of their private practice to share personal moments. With that they are sharing their sex-orientation, which is maybe to private for the older generations. Today in the most societies it is allowed and OK to be homosexual which can be a factor that more people in the Generation Y are sharing this too. For the Baby Boomers and the Generation X this was not accepted by the society and a big taboo.
Question 6: I follow my friends lives on social media.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 7,4 % | 13,2 % | 33,1 % | 36,4 % | 9,9 % |
| Generation X | 4,5 % | 20,9 % | 38,2 % | 31,4 % | 5,0 % |
| Generation Y | 6,3 % | 18,2 % | 31,9 % | 33,2 % | 10,4 % |
With this table you can see that in all generations a very low number of persons do not follow their friends on social media. There is a conflict to the own handling of their private sphere and their urge to look into the private sphere of others. The number of people who are willing to share private moments is much higher than the number of people who want to see the private moments of others (as you can see when you compare table 5 and 6).
Question 7: Views on religion.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 37,2 % | 17,4 % | 24,8 % | 16,5 % | 4,1 % |
| Generation X | 28,2 % | 25,9 % | 24,1 % | 14,5 % | 7,3 % |
| Generation Y | 26,1 % | 28,6 % | 25,3 % | 12,9 % | 7,1 % |
As you can see in table 7 there are no significant differences between the generation, but you can say that the Baby Boomers are the generation with the highest number of people who would never share their views on religion with 37,2% the Generation nearest to this view is Generation X with 28,2% followed by Generation Y with 26,1%. Nevertheless you can say that the generations are acting very similar in this topic. This can be so because we are free to practice our religion in the western world, it even is protecting by laws.
Question 8: Agenda-political views.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 33,1 % | 20,7 % | 24,8 % | 19,0 % | 2,5 % |
| Generation X | 30,9 % | 25,9 % | 18,6 % | 16,8 % | 7,7 % |
| Generation Y | 27,1 % | 25,6 % | 26,1 % | 16,5 % | 4,8 % |
Also in table 8 are no significant differences, but you can say that with the younger generations the people who would never share their agenda-political views decreases. 33,1% of the Baby Boomers, 30,9% of the Generation X and 27,1% of the Generation Y would never share their agenda-political views. Today it is become an issue to discuss with others to form his own opinion and to manage the flood of information who is out there. But religion and the political views are belong to the private sphere as well. political elections in the western world are anonymous to save the private sphere of the electorate, so that nobody can judge by his opinion.
Question 9: Sexual preference.
Answers :
| Generation | Never | Rarely | Sometimes | Usually | Always |
|---|---|---|---|---|---|
| Baby Boomers | 92,6 % | 4,1 % | 3,3 % | 0,0 % | 0,0 % |
| Generation X | 92,7 % | 3,6 % | 1,4 % | 1,4 % | 0,9 % |
| Generation Y | 84,6 % | 7,8 % | 5,8 % | 0,0 % | 1,7 % |
With this table you can see that there is a difference between the two older generations to the Generation Y. 92,6% of the Baby Boomers, 92,7% of the Generation X and 84,6% of the Generation Y answered that they never would share their sexual preference.
The own sexuality is one of the most private issues of the private sphere. In the German law there are three spheres to save the general right of personality.
the Individual Sphere which includes: the right to informational self-determination, the Right to Re-socialization and the right to knowledge of one's ancestry.
The second deepest sphere is the Private Sphere which includes: the protection of private life as well as life in the home and in the family circle.
The last and deepest sphere is the Intimate Sphere as well as the most Intimate Privacy, this sphere encompasses the protection of the inner world of thoughts and feelings as well as the protection of the sexual sphere.
Based on the table for question 9 you can say that the youngest Generation Y is breaking the line of their own intimate sphere by their own. While the Generation X is careful about what they are sharing and they are aware of the consequences this can have for their professional lives.
The behaviors of the generations are similar in term of spaces of the home, relationships among individuals and religious ans political views. There are differences in terms of certain parts of the body, family, clothing, private relationship status and sexual preferences. The Generation Y is here the first generation who grew up with personal computers and smartphones. In some cases they are acting more freely with their private sphere than the older generations. The question is, will are there more differences with the next generation? The Generation Z which members are born directly after the Generation Y and who are the second generation who will grown up in a digital world.
Glossary
[edit | edit source]Please put the terms in alphabetical order when adding. |
- Always-on: A term relating to the notion of persistent connectivity to a shared global network.
- Authentication: Where an entity is proved to be valid or a user provides information to prove their identity.
- Collective Intelligence: A term to describe the sharing of knowledge and information in a collaborative for.
- Data Mining: The practice of sorting through data to identify patterns and establish relationships, in relation to online privacy, data mining collects data from users of social media to examine trends and target adverts.
- Digital Age: Also known as the information age that is considered to have started in 1970 with the development of technology such as television and computers.
- Encrypted Messages: Relating to Facebook's secret messaging service, encrypted messages allow end-to-end conversations to occur where only the communicating users can receive the messages.
- Filter Bubbles: The use of algorithms to display information which appeals to the specific user's interests.
- Fear of Missing Out (FoMO): A form of anxiety aroused by the fact that an exciting or interesting event may currently be happening from posts on social media.
- Global Village: Coined by Marshall McLuhan, a social organisation when society can easily transfer and share information as a collective.
- Hacking: Forced access to a closed, private system or device.
- Identity theft: The deliberate use of someone else's identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other person's name.
- Internet cookies: Small pieces of information in text format that are downloaded to your computer when you visit many Web sites. The cookie may come from the Web site itself or from the providers of the advertising banners or other graphics that make up a Web page.
- Keylogging: The act of tracking what the user is typing.
- Leaks: The public release and circulation of private information against the owner of the information’s will.
- Margin of error: A statistic expressing the amount of random sampling error in a survey's results. It asserts a likelihood (not a certainty) that the result from a sample is close to the number one would get if the whole population had been queried.
- New Media: The means of mass communication using digital technologies such as the Internet and social media platforms.
- Oversharing: The act of revealing too much personal information about oneself online.
- Privacy Policy: A privacy policy is that which states the ways a company gathers, uses, discloses, and manages a customer or client's data. It fulfills a legal requirement to protect a customer or client's privacy.
- Private Sphere: Often defined in opposition or parallel to the public sphere. The private sphere is a section of societal life in which an individual has a degree of seclusion from the public. The concept has become blurred since the advent of social networking as "private messaging" communications are often stored on databases.
- Public Sphere: Often defined in opposition or parallel to the Private Sphere. The Public Sphere is the section of societal life where private individuals come together to form a public entity. The ideology of the Public Sphere is that private people come together to discuss matters involving the greater good of the public.
- Retweet: A function on the social media platform Twitter that allows users to repost or forward a Tweet.
- Spyware: Software designed to give unauthorised access to a system.
- Vlog: A blog in which the postings are primarily in video form.
- Web 2.0: A development of the internet that focuses on user-generated content.
References
[edit | edit source]- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p26
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies" in A Private Sphere, p27
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p26
- ↑ http://www.encyclopedia.com/philosophy-and-religion/other-religious-beliefs-and-general-terms/miscellaneous-religion/public#3-1O88:pblcsphrvrssprvtsphrdstnc-full
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p28
- ↑ Fuchs, Christian. “Habermas’s Concept of the Public Sphere” in Social Media: a critical introduction, p181
- ↑ https://petition.parliament.uk/help
- ↑ https://infoscience.epfl.ch/record/146804/files/InformationSchool.pdf
- ↑ Burnett, Robet. Marshall, David. 2003. Web Theory, pg.1
- ↑ Levy, Pierre. Bononno, Robert. 1997. Collective Intelligence. p13
- ↑ Fuchs, Christan. 2014. Social Media, A Critical Introduction, p32-43
- ↑ Gauntlett, D. 2011. Making is Connecting: The Social Meaning of Creativity, from DIY and knitting to YouTube and Web 2.0
- ↑ http://www.danah.org/bio.html
- ↑ http://www.sheffield.ac.uk/socstudies/staff/staff-profiles/helen-kennedy
- ↑ Levison ,P. 1999. DIGITAL MCLUHAN, p2
- ↑ McLuhan, Marshall. 1962. The Gutenberg Galaxy, p32
- ↑ Levison ,P. 1999. DIGITAL MCLUHAN, p4
- ↑ http://zizi.people.uic.edu/Site/Thoughts/Entries/2010/11/23_A_Private_Sphere.html
- ↑ Fuchs, Christian. 2014. “Google: Good or Evil Search Engine?” in Social Media: a critical introduction, pg.132
- ↑ http://www.alexa.com/topsites/category/Computers/Internet/Searching/Search_Engines
- ↑ http://www.internetlivestats.com/google-search-statistics/
- ↑ Fuchs, Christian. 2014. “Google: Good or Evil Search Engine?” in Social Media: a critical introduction, pg.127
- ↑ https://www.usnews.com/opinion/articles/2013/05/10/15-ways-google-monitors-you
- ↑ https://www.google.com/intl/en/policies/privacy/#infouse
- ↑ Meikle, Graham. 2016. “TMI: Prism” in Social Media: Communication, Sharing and Visibility, pg. 106
- ↑ https://www.theguardian.com/technology/2013/aug/14/google-gmail-users-privacy-email-lawsuit
- ↑ http://www.bbc.co.uk/guides/z9x6bk7
- ↑ https://www.google.com/policies/terms/
- ↑ https://www.theguardian.com/technology/2013/aug/14/google-gmail-users-privacy-email-lawsuit
- ↑ https://investor.fb.com/home/default.aspx
- ↑ https://zephoria.com/top-15-valuable-facebook-statistics/
- ↑ http://bigthink.com/praxis/do-you-have-too-many-facebook-friends
- ↑ Miller, Daniel. 2011. Tales From Facebook, preface
- ↑ https://zephoria.com/top-15-valuable-facebook-statistics/
- ↑ https://www.statista.com/statistics/417295/facebook-messenger-monthly-active-users/
- ↑ https://www.theguardian.com/technology/2015/mar/31/facebook-tracks-all-visitors-breaching-eu-law-report
- ↑ http://newsroom.fb.com/news/2015/03/send-money-to-friends-in-messenger/
- ↑ https://twitter.com/privacy
- ↑ https://en.wikibooks.org/wiki/Living_in_a_Connected_World/The_Online_Real-Life_Divide#Snapchat
- ↑ http://www.independent.co.uk/life-style/gadgets-and-tech/news/snapchat-privacy-terms-of-service-legal-snaps-update-a6714686.html
- ↑ Papacharissi, Zizi. 2010. A Networked Self, edited by Zizi Papacharissi, Taylor and Francis, p315
- ↑ Rettberg, Jill Walker. 2014. Seeing ourselves through Technology, Written, Visual and Quantitative Self-Representations, p11-14
- ↑ boyd, danah. 2014. It’s Complicated: The Social Lives of Networked Teens, p32
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p27
- ↑ Dery, Mark. 2008. "The everyday posthuman: new media and identity", cited in New Media, p269
- ↑ https://support.apple.com/en-gb/HT207056
- ↑ http://searchcrm.techtarget.com/feature/Location-based-apps-bring-ease-and-privacy-concerns-to-consumers
- ↑ https://www.cnet.com/news/senate-bill-amounts-to-death-penalty-for-web-sites/
- ↑ Charlie Osborne, "Would a Wikipedia blackout be such a bad thing?", iGeneration on ZDNet, December 13, 2011, 11:04 am PST. Retrieved January 5, 2012.
- ↑ http://www.ispreview.co.uk/index.php/2016/11/uk-government-confirm-move-force-isps-blocking-adult-sites.html
- ↑ https://www.publications.parliament.uk/pa/bills/cbill/2016-2017/0087/amend/digital_rm_rep_1123.1-7.html
- ↑ Lanier, Jaron. 2010. You Are Not A Gadget, p48.
- ↑ https://opennet.net/research/profiles/burma
- ↑ https://opennet.net/blog/2008/07/burmese-regulations-cybercafes-stringent-expected
- ↑ http://www.internetlivestats.com/internet-users/china/
- ↑ Deibert, Ronald., Palfrey, John., Rohozinski., Zittrain, Jonathon. 2012. Access Contested : Security, Identity, and Resistance in Asian Cyberspace. p3
- ↑ Deibert, Ronald., Palfrey, John., Rohozinski., Zittrain, Jonathon. 2012. Access Contested : Security, Identity, and Resistance in Asian Cyberspace
- ↑ http://www.cnbc.com/2017/01/24/chinas-great-firewall-is-doubling-up-on-vpn-regulation.html
- ↑ http://influence-central.com/kids-tech-the-evolution-of-todays-digital-natives/
- ↑ https://freedomhouse.org/report/freedom-net/freedom-net-2016
- ↑ https://freedomhouse.org/report/freedom-net/freedom-net-2016
- ↑ http://www.newstatesman.com/politics/2014/07/deep-state-data-surveillance-about-power-not-safety
- ↑ https://www.aclu.org/report/bigger-monster-weaker-chains-growth-american-surveillance-society?redirect=technology-and-liberty/bigger-monster-weaker-chains-growth-american-surveillance-society
- ↑ http://www.newstatesman.com/science-tech/2016/10/everything-you-need-know-about-terrifying-investigatory-powers-bill
- ↑ https://www.theguardian.com/world/2016/nov/19/extreme-surveillance-becomes-uk-law-with-barely-a-whimper
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ Rainie, Lee. et al, “Anonymity, Privacy, and Security Online”. http://www.pewinternet.org/2013/09/05/anonymity-privacy-and-security-online/
- ↑ https://www.instantssl.com/ssl-certificate-products/https.html
- ↑ Ess, Charles. 2009. Digital Media Ethics, p31
- ↑ Ess, Charles. 2009. Digital Media Ethics, p32
- ↑ Athique, Adrian. 2013. Digital Media and Society: An introduction (1st ed.). Oxford: Policity Press, page 492.
- ↑ [1], Sharp, J. C., 2007. A short history of Spyware.
- ↑ [2], Lavasoft. 2017. The history of Spyware.
- ↑ [3], the official Microsoft Blog (2013, April 17)
- ↑ [4], Keyloggers Explained: What You Need to Know. (2017). Howtogeek.com.
- ↑ [5], Identity Theft Statistics in 2016 - Should You Be Worried?. (2017). ID Theft Authority.
- ↑ [6], What are the consequences of spyware activity? (2017). Computer-security-review.org.
- ↑ Andrejevic, Mark. 2011. Surveillance and Alienation in the Online Economy. Surveillance And Society.
- ↑ [7], Benjamin Edelman - Biography. Benedelman.org.
- ↑ [8], Is Google to Blame for Spyware?. Archive.oreilly.com.
- ↑ Janet Jackson and Justin Timberlake’s in the 2004 Superbowl
- ↑ Queen of cynicism: No stunt's too shameless for Beyonce, who was once accused of trying to look white but this week posed as a heroine of black power
- ↑ I don't date people who are famous', admits Emma Watson... but wishes she could 'protect' her beaus from the public eye
- ↑ Inside the Kim Kardashian Robbery: Everything We Know So Far
- ↑ chip off the old block: Did Malia Obama smoke MARIJUANA at Lollapalooza? Video shows the president's eldest daughter puffing on a suspicious cigarette (just like dad did . . .)
- ↑ Macaulay Culkin: ‘No, I was not pounding six grand of heroin a month’
- ↑ Carl Greenwood, (12 SEP 2016) Celebrity death hoaxes: The stars killed over and over again on social media.
- ↑ "Edison Chen's blog". CLOT. Archived from the original on 6 February 2008. Retrieved 4 February 2008.
- ↑ "Sexy Photo Gate' Mesmerizes Hong Kong, China and Sparks Police Crackdown, Backlash". The Wall Street Journal, Fowler, Geoffrey; Jonathan Cheng (15 February 2008)
- ↑ "China arrests over HK sex scandal", BBC News. 20 February 2008.
- ↑ "China riveted by stolen sex photos of Hong Kong stars". The Guardian., Watts, Jonathan (13 February 2008).
- ↑ "Chinas nackte Superstars", Der Spiegel. 27 February 2008.
- ↑ NewYorkDailyNews, Eloise Parker, (October 13, 2008) Choi Jin Sil, Ahn Jae Hwan, more South Korean stars commit suicide after Internet rumors.
- ↑ NewYorkTimes, Choe Sang-Hun, (12 October 2008) South Korea links Web slander to celebrity suicides.
- ↑ Business Insider, Kovach (2014), We Still Don't Have Assurance From Apple That iCloud Is Safe
- ↑ Business Insider, Kovach (2014), We Still Don't Have Assurance From Apple That iCloud Is Safe
- ↑ The Verge, Kastrenakes (2014), Apple denies iCloud breach in celebrity nude photo hack
- ↑ The Verge, Kastrenakes (2014), Apple denies iCloud breach in celebrity nude photo hack
- ↑ The Guardian, Badham (2014), If you click on Jennifer Lawrence's naked pictures, you're perpetuating her abuse
- ↑ The Guardian, Badham (2014), If you click on Jennifer Lawrence's naked pictures, you're perpetuating her abuse
- ↑ The Independent, Selby (2014), Emma Watson on Jennifer Lawence nude pictures leak: 'Even worst than seeing women's privacy violated is reading the comments'
- ↑ The Washington Post, Lubitz (2014), More stars react to the massive celebrity-photo leak
- ↑ The Telegraph, Sanghani (2014), Jennifer Lawrence photo leak: Let's stop calling this hacking 'The Fappening'
- ↑ BBC News, Kellon (2014), Apple toughens iCloud security after celebrity breach
- ↑ Forbes, Rogowsky (2014), Yes, Celebs Had Their iCloud Accounts Hacked. No, You Shouldn't Shut Yours Off
- ↑ Ashley Madison® - Affairs & Discreet encounters - Life is short - Official Ashley Madison website
- ↑ Rachel Hosie. "Ashley Madison hacking: What happened when married man was exposed"
- ↑ The Guardian, Thielman (2016), Yahoo Hack: 1b accounts compromised by biggest data breach in history, 2016
- ↑ New York Times, Goel (2017), Yahoo's Top Layer Resigns and C.E.O. Marissa Mayer Loses Bonus in Wake of Hack
- ↑ New York Times, Goel (2017), Yahoo's Top Layer Resigns and C.E.O. Marissa Mayer Loses Bonus in Wake of Hack
- ↑ The Guardian, Thielman (2016), Yahoo Hack: 1b accounts compromised by biggest data breach in history, 2016
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ The Guardian, Woolf (2016), Yahoo 'secretly monitored emails on behalf of the US Government
- ↑ Ess, Charles. 2009. Digital Media Ethics, p46
- ↑ Weber, Rolf H. 2012. "How Does Privacy Change in the Age of the Internet" in Fuchs, Boersma, Albrechtslund, and Sandoval (eds.) Internet and Surveillance: The Challenges of Web 2.0 and Social Media, p274
- ↑ [9], Stuart, K. & Arthur, C. 2011. PlayStation Network hack. the Guardian.
- ↑ [10], PlayStation outage caused by hacking attack - BBC News. (2011). BBC News.
- ↑ a b [11], Quinn, B. & Arthur, C. 2011. PlayStation Network hackers access data of 77 million users. the Guardian.
- ↑ Mogull, Rich. 2011. Protect your privacy: take control of social networking [[12]]
- ↑ Johnson, Sheree. 2014. New Research Sheds Light on Daily Ad Exposures [[13]]
- ↑ Baym, N. 2010. Personal connections in the digital age. Cambridge: Polity Press
- ↑ Miller, V. 2011. Understanding digital culture. London: Sage.
- ↑ https://www.sciencedaily.com/releases/2016/03/160330135623.htm
- ↑ Baym, N. 2010. Personal connections in the digital age. Cambridge: Polity Press
- ↑ Scheff, S. 2014. Are you oversharing on social media? Retrieved March 5, 2017, from http://www.huffingtonpost.com/sue-scheff/are-you-oversharing-on-so_b_5940996.html
- ↑ Lanier, J. 2010. You are not a gadget. New York: Alfred A. Knopf.
- ↑ Mayer-Schönberger, V. 2009. Delete : The virtue of forgetting in the digital age. Oxford: Princeton University Press.
- ↑ https://support.twitter.com/
- ↑ https://support.twitter.com/articles/77606
- ↑ (Mosco 2004)
- ↑ (Maxwell and Miller 2012)
- ↑ (Maxwell and Miller 2012)
- ↑ ( Allmer 2017)
- ↑ (Sandoval 2013)
- ↑ ( Dyer-Witheford 1999)
- ↑ Papacharissi, Zizi. 2010. "Public and Private Expression in Contemporary Democracies", in A Private Sphere, p27
- ↑ https://www.techopedia.com/definition/28556/filter-bubble
- ↑ Pariser, Eli.; Helsper, Ellen. 2011.The Filter Bubble: What The Internet Is Hiding From you,
- ↑ Lanier, Jaron. 2010. "Missing Persons", in You Are Not A Gadget, p3-23
| This page or section is an undeveloped draft or outline. You can help to develop the work, or you can ask for assistance in the project room. |
