The Computer Revolution/Software
What is software ?
[edit | edit source]Computer software, or just software, describes one or more computer programs (a set of programs, procedures, algorithms) and its related data, held, used or created in any form of computer storage (memory and media). Software is never physical.
Programs are created as a way to provide the instructions for the computer to perform tasks. The term is used to contrast with the term hardware (meaning physical).
Types of software
[edit | edit source]
The Operating System
[edit | edit source]The Operating System (OS) is the most important software in any computing device that is intended to interact with users (these include running applications from different creator than that of the OS). The OS is often a more complex System Software (SS), that is the most basic type of software that is required for a machine to operate, that often is even referred as Firmware (extremely reduced interaction with others than the creators, the firm).
Operating systems are much more prevalent than most people suspect. Most machines will be sold with some form of basic operative systems, some will bring it in installed form other will have it pre-loaded into read only memory (ROM). They requires it to function and so It is one of the most important software pieces on your computer. Without an operating system installed your computer becomes basically useless.
The operating system manages the hardware systems and software systems for your computer. It hides in the background of computer systems performing the small basic tasks that most people are unaware of, to translate applications code into instructions that the hardware can process.. There are some major tasks that most are aware of that the computer performs. These tasks include: Booting up the computer, organizing files, performing tasks (for example, reading from the hard drive), logging in, and managing security (firewall, permissions, etc.).
Today they exist not only in laptops or desktops, but in a wide variety of other devices. Operating systems have extreme versatility, especially with today's technologies. They also have large scalability, which means that operating systems can be simplified greatly or have features even the programmers may not be aware of. Operating systems are now used on routers, PDAs (Personal Digital Assistants), mobile phones, as well as a multitude of other computers including laundry machines and refrigerators. This does make sense as the computer in a typical modern cell phone is now more powerful than a desktop computer from 20 years ago. It also allows for customization of cellphones such as individualized rings and wallpapers.
The operating system interacts with the user in a form that can be understood by the user as it translates in computer form what is being entered by the user. This form can be text based or graphics based. For example, when you connect a device to your computer a pop up will come up on the taskbar explaining to the user what it is doing (installing the driver necessary to use the connected device). During the boot process the key component of the operating system called the kernel is loaded into memory. Unlike other components, the kernel is stored in the memory until the computer is turned off. The operating system can also configure and communicate with peripheral devices by installing the necessary device drivers needed to use that particular device.
The operating system controls the resources (memory, disk space) and makes them available as needed while you are using the computer. Also places in order which tasks need to be carried out. Storing files/documents in a specific location which can be fetched at a later time when needed. The operating system specific files are by default stored in its own folder (Windows Folder), and any applications which are installed their files will be stored the Program Files folder by default. Although there are default folders, users can create their own folders and name them accordingly to better organize. Each folder can hold multiple folders/files. File extensions should not be modified by the user as the operating system uses that information to open the file with the selected program. If the extension is modified the operating system will not know which program to use to open the specific file as a result the file will be corrupted and may not open.
The operating system has many security options to protect your computer from unauthorized users. Regular password that only you would know or using your finger print to log in. Another option would be setting up multiple accounts and making you the administrator on the computer while others would be standard users. Administrator users would have the ability to do anything on the computer, while standard users would be restricted from certain actions such as uninstalling/installing programs or modifying any settings.
The operating system has the ability to multitask, run multiple programs at once. The CPU is actually multitasking, going between different programs as it can only perform one task at a time. Multi-threading is the ability to perform multiple tasks within one particular program similar to multitasking which can perform between multiple programs. Both multiprocessing and parallel processing use multiple CPUs to perform tasks on your computer. Multiprocessing, each CPU performs on a different task than the other CPU. Parallel processing, multiple CPUs work on multiple tasks to speed up the process. Multiprocessing is used on most computers.
The operating system works to manage the memory being used by your computer by sending memory to programs being used and later retrieves it once the program is closed. Users can control memory use by closing programs which aren’t being used. Virtual memory is another way to enhance processing efficiency. Programs and data communicate between RAM and virtual memory as RAM is needed the information is copied to virtual memory and deleted from RAM. The process between RAM and virtual memory will continue until the program/data is complete. Using virtual memory can slower the process but it allows more memory use than what is available. To speed up processing on your computer, operating systems use a process called buffering and spooling. Buffering is space in the RAM or hard drive which stores the input and output. Spooling retrieves that information when needed. This will speed up processing as this particular task is not holding up the CPU from performing other tasks as it waits for one to complete.

Parker, D. M. (2011). Understanding Computers: Today and Tomorrow. Boston, MA: Course Technology. Cengage Learning.
Turning on
[edit | edit source]When booting up a computer there must be a basic operating system. There are multiple operating systems available for consumers to choose from; starting with the most common on desktop PCs, Windows, to common server operating systems, such as Linux. Windows is made to be user friendly, even those who know little about computers can easily master the basic commands. Linux comes in many different forms, some of them easy to use, and some of them meant more for those who are already aware of how computers operate, with complex codes and hard to use commands. The boot up information is usually stored in memory called ROM.
When the computer is booting up, several things will occur. First, the core of the operating system (known as the kernel) will be loaded into the computer memory. Then the computer identifies the hardware devices that are connected to the computer to confirm that all of the hardware devices are connected properly. Finally, there may be a login process or a security program launched via an instant message or login screen. These options can be customized by the user through the Windows Task Manager.

Parker, D. M. (2011). Understanding Computers: Today and Tomorrow. Boston, MA: Course Technology. Cengage Learning.
Basic functions
[edit | edit source]a major part of most operating systems, The file system, manages your files. It takes your files and puts them safely on your hard drive. It does the same function as you taking your papers and storing them in a filing cabinet until you need them next.
In addition to booting the computer, file management, and security, the operating system is also responsible for configuring devices. This is carried out with the plug and play feature, where devices become installed and accessed as soon as they are plugged into the computer, with the help of a driver, which is a small program that tells the operating system how to communicate with a specific device. Other responsibilities include communication with the user and managing and monitoring the computer’s resources. In a desktop computer, these resources are the processor, memory, disk space, etc. On a mobile phone, the resources include the screen, keypad, address book, battery, network connection, etc. The operating system’s overall goal is to provide a solid way for applications to work with the hardware.

Human machine interface
[edit | edit source]Command Line Interface (CLI)
[edit | edit source]
The CLI is non-graphical interface and uses typed commands only to perform. Although not as widely used as the GUI, the CLI can be used to accomplish many of the same feats - for those equipped with such programming skills. Through a CLI, one can encrypt files, create directories, navigate through directories, etc.
In Windows, the CLI used is called the Command Prompt. In Fedora, it is called the Terminal.
Graphical User Interface (GUI)
[edit | edit source]
The GUI (pronounced gooey) is a visual interface; convenient and preferred by most users, because of its simplicity and appeal to the eye. By performing simple, graphical tasks such as clicking on an icon, dragging a folder, or right-clicking files and navigating through choices, files can be opened, moved, renamed, saved, and so forth.
Modern computer operating systems often provide a desktop graphical user interface ("GUI") for displaying various graphical objects. Some examples of graphical objects include windows, taskbars, docks, menus and various icons for representing documents, folders and applications. If the GUI is touch sensitive, then a stylus or one or more fingers may be used to interact with the desktop. A desktop GUI could be two-dimensional ("2D") or three-dimensional ("3D").
A 3D GUI is being developed and will allow mobile devices like mobile phones and tablet pcs to work with proximity sensor arrays and is being develop to respond to hovering gestures. Modern mobile devices typically include a variety of onboard sensors for sensing the orientation of the mobile device with respect to a reference coordinate frame. For example, a graphics processor on the mobile device could display a GUI in landscape mode or portrait mode based on the orientation of the mobile device. Due to the limited size of the typical display of a mobile device, a 3D GUI could be difficult to navigate using conventional means, such as a finger or stylus. For example, to view different perspectives of the 3D GUI, two hands are often needed: one hand to hold the mobile device and the other hand to manipulate the GUI into a new 3D perspective.
The 3D GUI display environment for mobile device will use orientation data from one or more onboard sensors to automatically determine and display a perspective projection of the 3D display environment based on the orientation data without the user physically interacting with (e.g., touching) the display. In some implementations, the display environment could be changed based on gestures made a distance above a touch sensitive display that incorporates proximity sensor arrays.
Security
[edit | edit source]Most, as not to say all, software has 'holes' in their programming, operating systems are no exception. But in these case vulnerabilities make it possible for people to 'attack' and/or use your computer with, or more commonly without, your knowledge.
Microsoft more than any other commercial OSs has a long list of documented weaknesses, some fixed some not because they have not been classified as critical. In considering why as OS has more detected security problems that others one has to take into account not only the quality of the software but also the number of users, especially those capable of reporting the issues, and the amount of attention an OS receives from those attempting to take advantage of it's weaknesses (this also has to do with the OS market-share the bigger the more attractive to exploit).
There are methods to close these holes. One of the newer abilities of well known operating systems is the ability to update the software either manually or automatically. These updates are normally downloaded to your computer from the internet and installed on your computer, basically changing the structure of the programming to make the operating system more secure. Another option is a program like Norton Antivirus. It is one of the most common, but there are many other choices the consumer can choose from. Antivirus software protects your computer from outside dangers, such as hackers, scammers, and viruses. A hacker can log onto your computer and see all your personal information, and possibly have access to even your banking information. Viruses are common in today's world, they come from receiving files, downloading things from the internet, or even visiting certain sites. Antivirus programs work with your operating system and constantly check everything the computer does for anything that might be a threat.
Digital Rights Management (DRM)
[edit | edit source]Digital Rights Management (DRM) is that part or type of technology which are used by hardware manufacturers, publishers, copyright holders, and individuals with the intent to control the use of digital content and devices after sale. In short to prevent piracy, it controls access through technology. Examples can be cited like,
A company servers are programmed to block any forwarding of sensitive or restricted e-mail. E-book server is programmed to restrict copy of and printing of material as per the copyright holders contents. Software for DVDs limiting copies made.
Thus restrictions, encryption etc, are few methods. DRM runs from the time floppy disks were there.
A DRM scheme operates on three levels
Establishing a copyright for a piece of content. Managing the distribution of that copyrighted content. Restricting access via software once distributed on consumer level.
To accomplish this level of control, a DRM program has to effectively define and describe three entities-
The user. The content. The usage rights.
This it does by describing the relationship between them.
Graphical User Interface (GUI) V.S. Command Line Interface (CLI)
[edit | edit source]The command line and graphical user interface are two different ways a user can communicate instructions to the computer. For example, you can launch an application through the command line by typing in the command (path to where the program is installed) to open the application. Graphical user interface allows the user to physically search for the program via mouse click to open the application.
Although both methods are used today, GUI is the more common method used as it is much easier to grasp and people who are new to computers would find it extremely difficult to use the CLI method. With the GUI method it is much easier as you only have to learn how to point and click the mouse. With CLI it would be much difficult as you would have to memorize the path at which your file is located along with the different commands to open a file or launch an application. GUI is also a better way to go if you will be multitasking (using more than one program at a time) it is much easier to navigate to different windows using GUI. CLI does not offer an easy way to view multiple open applications or documents.
One good advantage about CLI is Scripting. CLI allows the user to use the command line to create what is called a script, which allows you to run a program without clicking through menus to find the program and run it. This is good for applications that should be run often say at a certain time. Although there are advantages and disadvantages to either option, it all depends on how good you are with the computer and if you have the patience to memorize all the commands and paths.
[http://www.computerhope.com/issues/ch000619.htm
Turning off
[edit | edit source]When you turn off your computer it writes any unsaved information to the hard disk. It will remember how your computer last looked and will reload that image next time you turn on your computer.
Operating System Classifications
[edit | edit source]Operating systems for personal computers are usually can be divided in several categories, in relation to a dedicated purpose, use or configuration.
On the personal computer most operating systems, are intended to be installed to a single computer and often, even if not restricted, will serve a single user. Today operating systems are subdivided into subcategories, such as desktop operating system, for mid and upper range machines and lighter versions for portables or legacy systems.
The server operating system is conceived to be installed as a network server, as to give several users access to its resources across a network. A server will often have no local users.
A network operating system, rests inside a server and serves to boot several client machines as its own personal operating system, often these client machines will not have any data storage device locally and will share the resources of the server machine.
There are also other factors that serve to distinguish operating systems, for instance the guarantees they provide in security or speed, for instance a real-time operating system will be dedicated to rapid processing of critical events, other relations can be formed about the structure of the OS, it can be monolithic or modular.
There are several types of Operating Systems which can be categorized. Multi-user operating systems are those in which one or more user(s) can run one or more program(s) at the same time. A Multiprocessing OS can allow one or more program(s) to run on more than one CPU. Most multiprocessing operating systems will run on single-processor machines, but it will be slower than a normal OS running on the same machine. Multitasking OS's allow more than one program to be running at the same time. Multithreading allows for different parts of the same program to be running concurrently. And finally, Real Time operating systems have an instant (as fast as possible) response to input. Most modern operating systems are a combination of several of the above types.
Mobile operating systems
[edit | edit source]
Mobile Operating Systems or Mobile OS have surged in popularity in recent years. With the development of so many mobile devices such as smartphones and tablets the need for high functioning mobile operating systems is a must.
Several companies, for example Microsoft, which provide personal or server network operating systems also offer mobile versions of their operating systems Windows CE, in fact most of last core changes to the Windows have been made in reducing its system footprint, MS hope is that Windows 8 with a specific packaging will be able to work as a Mobile Operating System. On the other hand some companies have developed strictly mobile operating systems (iPhone OS/Blackberry OS/Android).
Since the first release of the iPhone in June of 2007, Apple has been breaking records with their releases of the iPhone. It is not just the fun features of the phone, but the software that it runs on that makes it so revolutionary. iPhone OS is based on Apple's OS X operating system. It supports multi-touch input, and has thousands of applications exclusively created for the system itself. The versions since iOS 6 have voice command technology, where by simply talking to the phone, you can search on the latest version of Safari, find your way around on Bing driven GPS system, or call and text by voice command.
It seems that at as mobile device technology continues to gain in popularity and diversity, the mobile OS will continue to advance as well. Mobile technology has now infiltrated multiple areas of society from smartphones to IPADs used in classrooms and without mobile operating systems that would not be possible. To the consumer the demand of hardware vendors of a lighter operating system has been extremely positive, the path of optimizing resource utilization has been increasing in importance and the need to make the Operative Systems portable across different hardware platforms, alleviates the technological stronghold that has permitted some firms to dominate the hardware and Operative Systems fields for decades.
Cloud computing
[edit | edit source]

Many of the newer mobile device operating systems are taking advantage of the new meme "cloud computing". Cloud computing is really an mix of Internet technologies, storage, processing and social participation that is used as an off-site virtual service to gather,store and process information and allow you to share the information across machines to other persons. For example, let’s say you own an iPad, iPhone, and Mac computer. You schedule an appointment and put the appointment into the calendar application on your phone.
Cloud computing is in itself not an innovation, what has changed is the ease of access to the Internet, cost of storage (and improvement on storage technologies). It improved on usability of what previously would require some technical skill for instance to mount your own WEB and/or file server and incur in its operational costs. Those improvements became cumulative while you previous would then have to either repeat the input into your iPad and Mac, or you would have to manually sync all the devices with your computer. Now, using cloud computing, that synchronization of devices happens automatically whenever you are connected to Wi-Fi!
This of course has several implications, that are being exploited by corporations, that are not only willing to mine personal information from users of those services but will take the opportunity to control not only your data but your access to it.
Open-source Operating Systems
[edit | edit source]GNU-Linux
[edit | edit source]
GNU-Linux was developed by Linus Torvalds back in September 1991 using system tools and libraries originated in the GNU Project, initiated in 1983 by Richard Stallman. Since then, with help from around the world, Linux has become one of the world's most widely used operating systems.
The main difference between operating systems such as Windows and Mac compared to Linux is that both Windows and Mac are proprietary system, meaning that they have restrictions on them regarding usage and copying them. Whereas Linux is free software available for all to use, modify, and redistribute as they see fit.
Due to the nature of freeware there are literally hundreds of Linux distributions or versions, called Distros, available to users. These Distros vary greatly, some examples being hardware requirements, ease of use, stability, and appearance. When selecting a Distro, the idea is to find the one that meets as many of your needs as possible and is setup in your ideal fashion. After selecting the Distro that suits you best, you can finish customizing the operating system to make it truly unique to the user. Although all Distros are fully customizable they do have varying levels of technical competency requirements. A Distro such as Arch Linux that you install from scratch using a command line is not for a beginner compared to a Distro such as Linux Mint that is easy to install, has a GUI, and is packaged with application software common to many users.
Because of Linux's little to no cost, Linux is often found in micro-controllers or embedded computers such as PDAs, and cell phones. Linux is considered a unique operation system because it gives users the ability to customize it to a particular application. Linux is widely available over the Internet as a free download. It is available for both personal and server use and uses a much wider range of applications than Windows. Linux has a wide range of compatibility and many users are switching because they are finding it to be much more cost effective, and can get many different essential programs such as free or low cost office suites. [1][2]
Commercial and proprietary Operating Systems
[edit | edit source]When you purchase your computer this software may not show up on the receipt but you have paid for it.
DOS
[edit | edit source]In August 1981, IBM introduced to the world the "Personal Computer” including the operating system called MS-DOS 1.0. Prior to having any issues with DOS it was suggested that users take the time to create a boot disk:
1. Insert the blank floppy into the computer's drive. 2. Click the Windows "Start" button and select "Run." 3. In the text box that displays, enter "cmd" (= command) 4. Press the "OK" button. This opens your Windows command prompt. 5. Enter "sys (= system) x:" into the command prompt. 6. Press "Enter." 7. Replace "x" with the drive letter for your floppy drive. It only takes a few seconds to copy the boot files to the disk. 8. Reboot the machine with the disk in the drive.

With the very first use of computers, DOS, or Disk Operating Software was just about the only operating system used. It is very uncommon for computers to use DOS today because Graphical User Interfaces are much simpler to use for the average computer using person. This is because DOS uses a command line interface where the user inputs commands for the computer to process, instead of clicking on windows like many people do today. There are two types of DOS. Both were created by Microsoft and were used for IBM computers or IBM compatible computers. The two types are PC-DOS and MS-DOS.
UNIX
[edit | edit source]UNIX was developed in the 1960’s at AT&T Bell Laboratories for midrange servers. UNIX is a multiuse, multitasking operating system. Microcomputers, mainframes, and a diversity of other devices from different manufacturers can run UNIX. The flexibility gives UNIX a lead over competing operating systems. Although, UNIX is more expensive, requires a higher level of technical knowledge, and tends to be harder to install, maintain and upgrade.
OS X
[edit | edit source]Based off the UNIX operating System, Mac OS is seen in Apple computers and is very user friendly, including simple graphical user interfaces. Mac OS X Lion also make navigation more simple using new multi-touch gestures. Newer Mac OS can support dual 64-bit processors which is advantageous while multi-tasking. Mac OS X also has the capability of running Windows via BootCamp, so on restart, you have the option(by holding the "alt" key while the screen flashes white) of booting into Windows or Mac OS X. This function is not very well reciprocated by Windows at all. People have tried installing Mac OS X on Windows, commonly referred to as "Hackintosh's", albeit with loss of functionality and stability.
The term Hackintosh has become ever more popular as Apple starts to move to general purpose hardware technology that is easily accessible to anyone. 2005-2020 Mac hardware builds of Apple use the Intel i5/i7 second generation processor to offer the best performance with their operating system. The Apple software license of the Mac OS X does not allow it to be used on a computer that is not "Apple-branded. The hackintosh, a collaborative Kernel hacking project, works as the newer processors are now more compatible with the Mac OS X software and can be tweaked to work with current Gigabyte motherboards and second generation processors. Using information from tonymacx86.com you use iBoot and Multibeast to load kernels and drivers and install Mac OS X (Mac OS X Lion, with Mountain Lion in the works as of February 2012) on compatible hardware. The biggest attraction is the options outside of the processor and motherboard that could be easily changed to each persons style or interests.
.
Microsoft Windows
[edit | edit source]Microsoft Windows is the most popular desktop operating system, and has been for many years. As with technology in general, the Windows operating system has evolved over the years.
Microsoft has developed a wide range of Windows operating systems. In 1985, the original version of Windows was introduced as Windows 1.0, and later followed by Windows 3, which had several versions, such as 3.0, 3.1, and 3.11. They simply enhanced the DOS operating system, making it more user friendly, this trend continued with Windows 95 and 98.
The creation of the Windows NT and then the Windows 2000, Windows XP Professional, XP Home, Windows Vista and many more, were a large technological advance. While the first versions of Windows were simply add-ons to DOS. Later versions did not depend on DOS.
Windows desktop came in the footsteps of other OSs and enabled the customization of the GUI. That included changing skins, mouse keys function and the style of desktop, colors and etc. Until the release of Windows 98, free OS alternatives were not as attractive, by maintaining the GUI elements static across versions users feel comfortable and easily adapted to new releases. This was until Vista, since then the GUI of Windows has been in constant change.
Windows Vista version of windows had several improvements over Windows XP, it still has it's downside. Windows Vista had the following new features:
- 3D window viewing
- Capable of using flash memory as RAM rather than adding memory to the motherboard
- secure features than all previous windows versions
- side bar to allow quick access to commonly used gadgets
- Super-fetch feature.
The new Super-fetch feature knows what most commonly used programs/tasks are and keeps them in the memory to allow faster responsive times.
Windows Vista downsides:
- The system requirements for Windows Vista are extremely high compared to previous windows versions and even other modern operating systems.
- The integration of new forms of digital rights management (DRM), specifically the Protected Video Path (PVP).
- Poor hardware driver support.
- Legacy software incompatibility.
- Concerns have been expressed that Windows may be experiencing software bloat.
- Expensive compared to other modern operating systems.
Whether you should use Windows Vista largely depends on how you want to and need to use your computer.
The next operating system that Windows released was Windows 7. It was released in 2009. Windows 7 system requirements are about the same as Vista. Windows 7 was designed to start up and respond faster than Vista. It also focuses on making it more user friendly. An example of this you can drag taskbar buttons to have them the way you like it. Also, Windows 7 have a Device Stage. This was formed to make it easier to use and manage all your connected devices. Microsoft states Windows 7 runs well on netbooks, this was not always the case with Vista.
In 1995, Microsoft launched Windows 95, which was their first full-fledged operating system, and it was followed by Windows 98. Windows NT (New Technology) was the operating system developed for high-end workstations and servers. Following 98, was Windows ME (Millennium Edition) and Windows 2000, replaced Windows NT. These systems were followed by Windows XP, which replaced both Windows 98 and Windows 2000. Windows Vista replaced XP, and was the current version until 2009, when Windows 7 was released.
Windows 7 was available in four main editions and in 32-bit and 64-bit versions. The appearance is similar to Windows Vista but runs faster and is easier to use. It has many new features like rearranging taskbar buttons, pin locks on programs to the taskbar, arranging two windows side by side quickly and easily, or resizing windows to fill half of the screen easily.
- Windows 8
Windows 8 was the next operating system for PC developed by Microsoft. Some of the changes from the older OS include a new-look start menu, new password-protection methods, and a brand new Family Safety feature. The use of Windows 8 is available to desktops, televisions, laptops, and tablets. With a new OS comes new software applications, such as Internet Explorer 10 is which is said to run only on Windows 8. [3] Good news for parents. In addition of having integrated security software, Windows 8 comes with an optional app called Microsoft Family Safety. The software lets you set up accounts for your children. It monitors your child’s online activities, provides information on what they are doing as well as who they are communicating with. With Family Safety you can set up Web filtering, app restrictions, time limits, etc. A fresh desktop is another great feature of Windows 8. Small, static icons are replaced with big, beautiful tiles. Start screen of Windows 8 contains all the information and programs you care about, you just need to click on the appropriate tile to lunch it. Microsoft’s new operating system also provides a “real time” updates of your info and photos, therefore you can see how many new e-mails you are receiving, the latest pictures uploaded to Facebook and much more.
Source: Marc Saltzman, “Tech Connection”.
⇒Windows 8 Tablet.⇐
Microsoft released the new Windows 8 Tablet. It was equipped with the most advanced Microsoft Software. This tablet is touchscreen, though there is an option of attaching a special keyboard for the "laptop feel," for those who are more comfortable with an actual keyboard. The setup of the home screen is more advanced than the previous Windows Software. It is made up of rectangular shapes (a tiling window manager), each representing a different program or application. There is also an option of rearranging the applications and categorizing them in the order that you prefer. Not only does it provide you with a lot of features, but also free applications that you may download. If the new "start" window is too confusing, you have the option of switching it to the original desktop look, which will make it easier for you to maneuver.
Android
[edit | edit source]iOS
[edit | edit source]iPhone OS: Every iPhone has used a different variation of the same operating system since Apple first launched them in June of 2007. The latest versions support multitasking, video calling, picture messaging, the ability to cut, copy, and paste text, in addition to other features other phones have adapted in order to remain competitive in the smartphone market. To make applications for the iPhone OS one would need to learn how to program in Objective-C and be familiar with the Cocoa API.
- ↑ Morley, Deborah and Parker, Charles S. "Understanding Computers Today and Tomorrow 13th Edition"
- ↑ http://lifehacker.com/5889950/how-to-find-the-perfect-linux-distribution-for-you
- ↑ Marc Saltzman "Tech Connection"
System software
[edit | edit source]System software describes all files and programs that are not indispensable to the operating system functions but extend or guarantee the basic functionality of it to the user. When you install the operating system, the system software is also installed. Some system software may be necessary to ensure that the computer can perform basic functions in order to run other programs, that rely on it. It also can allows the operating system to communicate with the hardware of the computer in a modular way, that can easily be updated and configured to the existing needs. However, the end user does not run most of the system software, it runs in the background.
The main functions of an operating system are: interfacing with users(translating user instructions), booting the computer, (loading the kernel into the memory, determine and configure the hardware attached to the computer), configuring devices (using device drivers to communicate to computer peripherals), managing and monitoring resources and jobs, file management(organizing and keeping track of files), security (using passwords, firewalls to prevent intrusion). System software should not take up a great deal of the computer's memory in order to run efficiently and should be transparent to the user so that the user need not be aware of what the system software is performing in the background.
Another type of System software is represented by Utility programs having the role of managing and maintaining the computer system. They fall into several categories: file management programs (performing file management- file look up, copy, move, rename, delete), search tools (searching files), diagnostic and disk management programs (evaluate, diagnose and repair problems), Uninstall and cleanup utilities (deleting programs and temporary files), File compression programs, back-up and recovery programs, security programs (antivirus, antispyware, firewall).
Development Tools
Tools to help with the development of software used with computers have been available for a long time but tools for developing programs for devices that use embedded software which are called device software development tools, have not been available until recently. One example of this type of tool is Wind River Workbench, which is a collection of tools designed to speed up the development of devices that use this programs operating system or version of Linux.
Device Drivers
[edit | edit source]Device drivers, commonly just called drivers, are software programs that allow input and output devices to communicate with the rest of the computer system. Many device drivers come with system software when you buy a computer. Most new operating systems recognize new hardware devices on their own and automatically install them, but sometimes they require a device driver cd for installation.
Device drivers should be updated periodically. This can be done through the suppliers website.
Device drivers are very common for printers, scanners, video adapters and sound cards.
Zip Drive
[edit | edit source]A Zip drive is a useful asset to your computer as it allows you to back up your work. It is a little bit larger than the regular A: drive floppy disks and have the ability to hold 100 MB, 250 MB, and now up to 750 MB of data. They allow you to back up hard disks, information on your computer, and also enable you to transport large files from computer to computer. They range in reliability and speed in writing the disk and most Zip drives are compatible in drives with the same capacity ability. Most Zip drives are relatively durable and even come with write protection. Also, some Zip drives can be accessed only with a password so your information cannot be tampered with.
Software libraries
[edit | edit source]
Other basic utility programs
[edit | edit source]The following utility programs help to maintain your computer and keep the computer running with optimal performance:
Uninstall Utility -Removing programs that you are not using enables you to free up space on the hard drive. Simply deleting the program’s folder from your hard drive does not ensure that the program will be completely uninstalled since certain parts of the program may still be sitting elsewhere (such as shortcuts on the desktop) and can ultimately slow down your computer. Removing the programs using an uninstall utility ensures a complete deletion of the program. The uninstall utility may be accessed through the operating system or on the program that is being deleted.
Cleanup Utility -Another way to free up precious space on the disk is by using the Cleanup Utility. The Cleanup Utility deletes temporary files, such as files stored during a program installation, files sent to the Recycle Bin and temporary internet files. The registry cleaner deletes unnecessary information in the Windows registry, keeping the computer running efficiently.
Disk defragmenter -This program optimizes the hard drive by searching for files stored on the hard drive in fragments and assemble them to be stored in contiguous locations. This will make the hard drive run more efficiently since files are more organized and can be more efficiently located.

System Restore -System Restore is a very useful tool that allows a user to reset the current computer's system files to what they were at a specific point in the past. This tool is useful because if you ever install a program or a new driver that has an undesired effect on your computer and uninstalling it doesn't fix the problem, then you can simply use the System Restore tool to restore your computer's system files to an earlier date when your computer was functioning properly.

Network Utility
[edit | edit source]Provides basic tools for troubleshooting network communication problems.
PING Utility - One of the more common Network utility available on the more popular Operating Systems is the PING utility for network troubleshooting, this tool is to assess if a receiver (Host) is an integrated part of the Network. PING (for the sound that was made from sonar when detecting an object) incorporates the ICMP Internet Control Message Protocol, this protocol functions to report problems on the Network. When experiencing a problem accessing a Host, the PING utility is a good starting point for problem determination. Performing a ping can assist in determining if the Host is on a local network or the Internet. For example, from the Windows operating system CLI command prompt, type, for example ping 10.10.1.1 which is the IP address of the receiving host. A successful ping would display a response that will look like this “Reply from 10.10.1.1: bytes = 32 time < 1ms TTL=128”, a failed, ping will return a message like this, “request timed out”. http://www.ietf.org/rfc/rfc792.txt
Antivirus
[edit | edit source]
There are ways to counterattack against these malicious software - if one is well-equipped. Antivirus_Software, anti-spyware, firewalls, and other security programs are available to protect against these attacks.
Computer viruses are self replicating malicious software programs that can cause damage or perform other harmful acts to a computer system. Other than the virus, there are other security concerns in existence, such various types of spyware software similar to virus but not self replicating or worms that have as the only function to open breaches so that the infected machine is accessible from the network.
Though they are intentionally designed not to be destructive and evident in the infected computer system (or a network of computer systems) they can disrupt functions. The objective of the virus and spyware is to profit from the information and resources it takes control.
The term Spyware is used for software programs that secretly collect data and/or information, spying on the user's activities, without consent and then send it to an outside party, normally via the user's Internet connection. It can be as innocent as monitoring your web page visits so as to tailor the ads you are bombarded with, to logging keystrokes and all that may entail. The most serious implications of this practice are identity theft, and stealing sensitive information like credit card numbers etc.
Generally, they are installed without knowledge of the user when running other types of software, the most common way is to receive an infected e-mail message with an infected attachment or link to a site that promotes the execution of some other piece of software.

Lately, spyware use is happening more and more frequently and aggressively and it can damage your computer, causing it to work improperly or to slow down. Stealthware is a type of spyware that can deliver ads to your computer at any time, regardless of the activities it is engaged in. Browser hijacking is the act of spyware changing your browser homepage or other settings.
The worst type of spyware rewrites your computer's main instructions to change your browser settings back to their hijacked form every time your computer is rebooted, undoing any changes you may have made to your browser settings.
Importance of Anti-virus
[edit | edit source]To protect your system from viruses
- It is important to use Antivirus software [1] in preventing these unwanted programs from corrupting your information.
- Some of these viruses can corrupt your information, and some may overload your memories. In a lot of cases, virus can render your computer inoperable.
- It is also important to keep your antivirus software up to date as new viruses are created frequently.
There are many Anitvirus software programs available on-line such as Windows Live OneCare which helps protect your computer from many different kinds of threats. This software in particular also helps you back up your important documents in case of emergency and runs regular tune-ups to help your computer run smoothly.
Norton AntiVirus
[edit | edit source]Norton AntiVirus started in 1990. It is the most popular anti-virus program having over 100 million people worldwide using it.It has many valuable features. These features include detecting, blocking, and removing viruses, worms, and spyware.It also protects email and instant messages. For the computer's safety it will automatically renew your subscription. The current version is Norton AntiVirus 2007.
Comodo
[edit | edit source]Comodo Internet Security ensures 100% protection to the system for its users. This works as a package, which is in a combination of antivirus software along with an enterprise class firewall and an advanced host intrusion prevention system. All this can be used together or used separately for a specific purpose. To avoid and to prevent the attack of viruses Comodo offers Antivirus Software for Windows at its best.
McAfee
[edit | edit source]McAfee is also one of the worlds leading anti-virus programs. Similar to Norton, McAfee had been industry tested and reports 100% detection. It also has easy scheduling to keep the software and your computer up to date. McAfee software also scans e-mails and IM attachments as well as has a very idepth virus database. After surfing the McAfee site I really enjoyed how they have a section that explains what each of the viruses are and what the do in a language that the common user can understand. By being able to relate this to the user it allows the user to educate themselves and take action. On the down side, McAfee's e-mail monitoring creates a popup for every single e-mail outside of the preset limits. For someone such as myself that receives a lot of mail from unknown senders (some junk and some relevant) this can be a very time consuming chore. On the plus side, McAfee's price is a little less expensive so if your do not use your computer very much this is the program for you.
Virex
[edit | edit source]Virex is McAfees Macintosh Anti-virus software. This is very similar to the McAfee anit-virus for the PC with several key differences. Because of the Mac OS X platform you are able to drag and drop the files that you would like scanned which can really speed up your monitoring. The Virex interface is different from that of the PC interface it has been designed with the Mac user in mind. With operating Virex you will find that the program is the same user friendly Mac screen. As well with drop scan this makes it easy to run extensive searches through individual pieces or individual files. This can prove to be quite useful when running multimedia editing software where only portions need to be scanned.
Free disk utilities software
[edit | edit source]There are many free antivirus programs and windows utilities that are available for use on desktop and laptops I would like to introduce three in particular that are very useful. The first program you can use is from Piriform.com which is named C cleaner. This software supports Windows 7, Vista and XP also (there is also a version which supports Mac OS X 10.5 or 10.6). This will clean Internet Explorer, Google Chrome, Opera, Safari, and Windows Registry cleaner. C cleaner will clean temp files, history, cookies, and the auto complete form history. On Windows it cleans recycle bin, recent documents, and temporary files and again form history. On the Registry it cleans the unused and old registry history. The next is Auslogic disks defrag can be found on the site auslogic.com. The disks defrag “process reduces the amount of fragmentation's” it will organize storage devices into smaller fragments so to create more space.

The last software to introduce is Microsoft Security Essentials.. This can be found at the Microsoft.com site. Before you use this software the computer must have be installed with genuine Windows. This software will scan and do updates on scheduled times. I believe that antivirus software can be useful in keeping your computer running more effectively and free from viruses.
1.piriform.com 2.auslogic.com 3.microsoft.com 4.notionbit.com [2][3][4]
Firewall
[edit | edit source]
Zone Labs Security Software
[edit | edit source]Zone Labs is a brand of software which provides Internet security solutions. It protects PCs from spyware, personal data theft, identification information theft, and of course hackers. This software is derived from its own research center, which presents us with up-to-date security, anti-spyware and anti-virus information. It also alerts us of the most recent security threats. This software allows your computer to still run quickly and smoothly, due to its superior compatibility. Parents are advised to use this program, as it prevents children from access to inappropriate websites. While emailing, it is able to quarantine unknown attachments while stopping the spread of it by preventing outbound messages so you don’t send it out to everyone in your address book. It blocks out those annoying pop-up advertisements so you can surf the web without having to keep closing the boxes. Also, when you install new programs it will alert you of any dangers there may be.
Multipurpose
[edit | edit source]
Some features may be:
- Detect and automatically removes viruses, Trojan horses, and worms.
- Checks incoming and outgoing email attachments for viruses.
- Automatically scans incoming instant message attachments for threats.
- Checks compressed file archives for viruses.
- Keeps dangerous Internet worms out, blocking them before they infect your system.
- Automatically downloads updates to protect against new threats.
- Automatically scans for viruses upon completing a download.
- Using smart technology to detect emergent worms and other new threats without waiting for updates.
Norton
[edit | edit source]When it comes to anti-virus software Norton is the industry leader. Norton has been given praise for reports of to having 100 percent detection for virus. Norton easy scheduling scans which make it easy to keep your computer up to date. Norton does everything from scanning inbound and outbound e-mail to IM attachments. Essentially it monitors all information going into and out of your computer. One feature that makes Norton stand out is that in includes an inbound firewall protection. However, all these great features do come at a cost Norton is on the high side of the market and there are many other alternatives for a lower price. Norton includes spyware, firewall, security, systemrestore and ghost. All in all if you are looking for a sure bet with minimual hassel Norton is it.
Application Software
[edit | edit source]Application Software is basically a program that allows you to open, save, amend or program a file on your computer. A common type of application software that in offices is the software suite where are a number of programs all sold together and they are used for different purposes.
Desktop vs. Mobile Software

Notebook computers, tablet computer, UMPCs and other portable computers run the same application software as desktop computers. Mobile phones and other mobile devices typically require mobile software that is specifically designed for a specific type of mobile phone or other mobile device. A wide range of mobile software is available today. There are mobile compatible versions to popular programs like Word or Powerpoint, games, media players and business tools that record inventory data or keep track of your business expenses, calendars and programs that allow you to organize notes and voice recording, applications that allow you to broadcast your current location to friends and web browsers for accessing web sites.
Many mobile applications include features for easier data input, such as an on-screen keyboard, a phrase list, or hand writing recognition capabilities. Some mobile software is designed to be compatible with popular desktop software, such as Microsoft office.
With Mobile phone – we can do lot of things including accessing and searching the Web on most of today’s phones. Web searching is text based; mobile voice search is now available. Mobile voice search allows you to speak, rather than type, search term into your mobile phone and then see the results of that search.
With Mobile software application we can able to install Google search, Yahoo search programs into Mobile software and it is easier to use once it is installed in our mobile phones. With Mobile software application it is easier to use while on the go. Commonly requested information includes directions to local businesses, stock quotes, flight information, local restaurants, weather information etc. Both these applications are very useful and essential in today’s busy world.
Software Suites
[edit | edit source]Software programs that have similar characteristics are often purchased bundled together in a software suite. Software suites used for creating documents are referred to as office suites or productivity software suites. Examples include word processing software, spreadsheet software, database software and presentation graphics software.
Software suites offer advantages to users by providing programs that have a similar interface as well as its often cheaper to purchase the bundle versus each program individually.
It is well known that popular office suites like Microsoft Office is used by many individuals and businesses, there are also free and open-source alternatives to it like LibreOffice or even Google Docs for web users.
Desktop Publishing
[edit | edit source]
Desktop and personal publishing software are used to create attractive documents. The software can manipulate text and images to look as if they came from a professional printer. Although word processing programs can also create attractive documents, desktop publishing is solely designed for this purpose, and can be more efficient. Many people choose to use desktop and personal publishing software for this reason. Some of the documents that can be created are greeting cards, invitations, flyers, calendars, brochures, certificates, and announcements.
Spreadsheets
[edit | edit source]The spreadsheet program summarizes information from many paper sources in one place and presents the information in a format to help a decision maker see the financial "big picture" for the company. Over half of financial management reporting is performed with spreadsheets.
Because of the ease of use, flexibility, and power of spreadsheets, they support many critical business functions and often fill roles where other solutions would be too slow or costly to implement. Years ago accountants and payroll specialists used to input all of their information into long hardcopy documents. Now companies can get the work done with half the amount of staff.
Philip Howard (2005-04-22). Managing spreadsheets. IT-Directors.com. Retrieved on 2006-06-29.
Spreadsheets have come a long way over the years and are more user friendly so more people use them – not just accountants. Because of the large number of mechanical calculations that must be performed, payroll was one of the first functions to be computerized in most organizations.
Software packages allow users to create a large worksheet in which data and formulas can be entered to perform a variety of calculations and analysis. People used to have to work on multiple spreadsheets at the same time or in other applications when they needed to analyze large amounts of information. Now spreadsheets can be a lot larger in size.
Charts, tables and graphs can also be utilized. You can apply rich visual enhancements to your charts.
Another great benefit of spreadsheets is the fact that more than one person can manipulate a spreadsheet if they are on a shared database. They can input data from their own computers anytime they want. The advantage of this is that people can work in teams and help to protect and control access to their work.
Real Estate professionals use spreadsheets for financially analyzing income property for all types of real estate (amortization and appreciation). Once there is a spreadsheet created for one property the data can be saved for all investors’ presentations related to the building in one workbook. Later you can recall the input data for any investor. This makes work very convenient and saves a lot of time.
One spreadsheet document is referred to as a worksheet. Many worksheets can be saved together into a spreadsheet file called a workbook. The worksheets are divided into rows and columns that all have cell addresses. You can enter information into the active cell, which is the selected cell. In order to enter information into multiple cells all you do is select more than one cell with the cell pointer. Formulas may be used to perform mathematical functions to compute certain tasks. Using formulas can save a lot of time entering information.
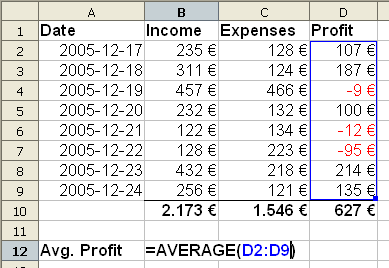
The Bad News about Spreadsheets
[edit | edit source]Spreadsheets are the most used program in accounting, finances, statistics and many other tasks in the daily activities of a company. However, spreadsheets have their downfalls when it comes to how the formulas are used within them. If the right output or input is not correct then a wrong answer will be generated, but sometimes it is not possible to know if we have the wrong answer. Also if the numbers in each cells are not formula generated, many mistaken would be generated when we try to use them. If a number is hand written in a cell, not generated by a formula, then that number will give the wrong answer when used within another formula, and in a large set of data it is impossible to know if we have the wrong answer. Another fact is that if we want to pin a cell within a formula a dollar sign is required in front of the cell, in order to be able to use that cell only, in cases where we need to perform calculations in multiple cells with the copy and paste function, instead of writing the formula for each cell. If we do not pin the cell we want to use for each calculation then Excel will perform the calculation for each cell numerically and we will have wrong answers. Spreadsheets are easy to use for large groups of data, but the input and output options have to be always correct in order to have the right answer at the end.
Microsoft Excel is the component of Microsoft Office which is used to create payroll analyses, reports, charts, queries, and forms for either personal or for a business.
One page of a book is called a sheet and a whole book is called a workbook.
The easiest way to calculate numbers is by using formulas. In order to create a formula you need to start one by using an equal sign (or a plus or minus sign). For example =sum (A1:B1). A1 = 1 B1 = 2 C1 would = 3. If you do not put a sign, the formula will be interpreted as text. The fastest way to add up a row is to use the Auto Sum function from the Home Tab.
The easiest way to sum up more than one row is dragging to the right and down the rows at once.
Some of the other features include Merging & Centering Data, Rotating Text, the ability to copy and paste data from one cell to another by the use of the Format Painter, and the use of an IF statement to test if a condition is true.
History of Spreadsheets
[edit | edit source]Spreadsheets have certainly aided the computer industry for business purposes, with the most popular example being the Microsoft Excel application.
Microsoft originally developed a spreadsheet program called Multiplan in 1982. However, it soon lost popularity to Lotus 1-2-3 when it came to MS-DOS systems. This heralded the development and release of Excel in 1985 for the Macintosh computer. The first Windows version was released in November 1987 which lined up with the Mac and bundled with a run-time windows environment.
By 1988, Excel had started to outsell 1-2-3 because Lotus was slow to bring it to Windows. This helped Microsoft become the leading PC software developer. Microsoft developed regular new releases every two years or so.
Another company was selling a software package named "Excel" in the early years of Microsoft's Excel development, which lead to a trademark lawsuit. This necessitated that Microsoft refer to the program as "Microsoft Excel" in all of its press releases and legal documents. Eventually this practice was ignored, particularly since Microsoft purchased the trademark to the other program. The Microsoft program was also referred to as "XL" as an abbreviation, and the file extension of the default Excel format is ".xls".
Excel allowed the user to determine the appearance of spreadsheets (fonts, character attributes and cell appearance). Until 1999, this was unique compared to other spreadsheets on the market. It also allowed only cells dependent on the cell being modified to update. Previous spreadsheet programs recalculated everything all the time or waited for user commands to update the spreadsheet. The icing on the cake for Microsoft Excel was that in 1993 when it was first bundled into Microsoft Office, Microsoft Word and Microsoft Powerpoint had their GUIs redesigned for consistency with Excel.
Microsoft also added the ability to automate tasks in Excel and to provide user-defined functions for use in worksheets. However, the automation functionality caused Excel to become a target for macro viruses.
The biggest threat to Microsoft Excel is the Free Software OpenOffice.org Calc and also Gnumeric, both of which can open and save Excel documents. love Greg work t.v. ps3
Personal Information Managers
[edit | edit source]A personal information manager (PIM) is a type of application software that functions as a personal organizer. As an information management tool, a PIM's purpose is to facilitate the recording, tracking, and management of certain types of "personal information".
Examples of PIM:
- Address Books
- Calendars
- Journals
Microsoft Outlook
[edit | edit source]Microsoft Outlook is a personal information manager from Microsoft, and is part of the Microsoft Office suite. Outlook is an e-mail client, an address book, journal, a calendar and many more PIM features.
Mac iCal
[edit | edit source]iCal is a personal calendar application made by Apple Inc. that runs on the Mac OS X operating system. iCal was the first calendar application to offer support for multiple calendars and the ability to publish/subscribe calendars to WebDAV server.
Reference: http://en.wikipedia.org/wiki/Image:ICal2.png February 27, 2007
Evolution
[edit | edit source] Evolution is a personal information manager made by Novell and the GNOME project primarily for Linux, although it is also available for Mac OS/X and may soon be ported to Microsoft Windows.
Evolution is a personal information manager made by Novell and the GNOME project primarily for Linux, although it is also available for Mac OS/X and may soon be ported to Microsoft Windows.
Vault 3
[edit | edit source]Vault 3 stores your information and photographs as an outline. Vault 3 organizes your information into categories and sub-categories that you specify. Vault 3's outline is easily and rapidly searchable. Vault 3 uses strong encryption to ensure the privacy of your personal data. Vault 3 can even run slideshows of your photographs. Vault 3 runs on 32 and 64-bit Windows operating systems, 32 and 64-bit Linux GTK operating systems, and 64-bit Mac OS X.
Reference: http://www.ericbt.com/Vault3
Vault 3 is also available for Android: https://market.android.com/details?id=com.ericbt.Vault3
Speech recognition software
[edit | edit source]Speech recognition has came along way in the last 10 years. I owned a copy of the first Dragon Speakeasy and not only was it slow, but it usually came out resembling some sort of Star Trek Klingon language. Over the years however significant advancements have been made. Speech recognition software has become so accurate that it allows authors and other desktop publishers to utilize it for all aspects of there work. Initially all the different commands take awhile to learn much like the character recognition of Palm pilots. However, after users become knowledgeable speech recognition software save the user a great deal of time and is highly efficient. Although there are a few different manufactures on the market today Dragon Naturally Speakeasy is credited as being the most accurate and is the industry leader. If you are someone who suffers from Carpal Tunnel Syndrome or spends a great deal of time with desktop publishing then speech recognition software is for you.
Accounting software
[edit | edit source]Accounting software is software that allows users to run their own books. This is ideal for small business owners who do not want to pay the high fees of hiring an accountant to run their books. Accounting Software such as Simply Accounting, QuickBooks or Microsoft Small Business all make it easy for the small business owner to run their own books right off of their home or work PC or Mac;) There is a lot of flexibility in this software and a lot of customizable features for your own business. If you are looking at purchasing this software it is highly recommended you speak to an expert who understand what the uses will be. The prices range from hundreds all the way as high as thousands for small business software. Accounting software can be picked up an any major electronics retailer.
Tax Software
[edit | edit source]Tax software has solved the headaches of millions! This was a time of year that everyone dreaded, however with the advancements made through the computer revolution, filing your taxes has become as simple as roasting a turkey. Because it is so easy to file taxes there are dozens of software manufactures on the market each with their own version. If you are still slaving away for hours on end remember in the time it takes you to roast a turkey you can have your taxes done with tax software!
Presentation software
[edit | edit source]Some ways to create a slideshow within Windows or Mac to create a presentation include Microsoft Power Point, Adobe Photoshop, or Corel Draw to produce professional presentations. Once you open any of these applications you have to create a slide on the screen to convey each portion of what you desire to present. Once you have created your text of a maximum of eight lines or less per slide you have to choose the options within the application to attract the viewer to what you are presenting. Some of these options include the Font Size, Color, Bullets, Shapes, 3D Appearance, and other features to maximize your presentation that you can place anywhere within the slides. Once you are finished creating the presentation you have to Rotate, Pivot, and use several Transitions to make your final project run smoothly.
Power Point
[edit | edit source]Microsoft PowerPoint Is a very easy to use presentations software designed and made for Microsoft windows and Mac OS operating systems. Power point is most commonly used by business people and students to create phenomenal presentations and projects. It can easily be used by Junior high student all the way up to senior's, with intermediate options to technically challenging options. Apparently the Microsoft corporation believes that thirty million presentations are made each day with the power point program.
There are many different options and abilities to use when working with PowerPoint, text, graphics, animation, movies and other objects are all possibilities within the program itself. It offers challenging components as well as easy to do elements that allows all levels off people to use it.
Presentation Graphics Concepts
The saying “a picture is worth a thousand words” is the cornerstone of Presentation Graphics. The basic concepts and features of presentation graphics is an image designed to enhance a presentation such as an electronic slide show or a printed report. A variety of software including spreadsheet programs, image editing programs, and presentation graphics software can be used to create presentation graphics. It takes the form of electronic slide containing images, text, video and more that are displayed one after other in an electronic slide show. Electronic slide shows are created with presentation graphics software and can be run on individual computers or presented to a large group of people in a conference room on a big computer projector; they are frequently used for business, Educational presentations. Today's most common presentation graphics programs are Microsoft PowerPoint, Corel Presentations, and Apple Keynote.

Creating a Presentation - A Presentation graphics program contains a variety of tools for creating and editing slides. For example, new slide can be added to a new or existing presentation. Charts can be added or edited in a new or existing presentation slide. Text, photographs, tables, shapes, charts and more can be added to slides using the Insert tab and formatted as needed using the Format tab. To create more exciting and dynamic presentation, multimedia objects and animation effects can be used. Video and audio clips can be inserted into a slide and set up to play automatically each time the slide containing those elements is displayed. Once the basic slides in a presentation have been created, the overall appearance of the entire slide show can be changed by applying a theme such as combination of colors, fonts, and effects that can be applied to an entire slide show at one time to the presentation using the Design tab. Transitions-special effects used between slides can be applied to specific slides. In PowerPoint, animation and transition are both specified using the Animation tab.
Helpful Rules When Creating a PowerPoint Presentation
[edit | edit source]Power Point presentations should be developed around 2-3 messages. The messages should summarize what you want the audience to remember. A rule that is good to remember when creating a Power Point presentation is KISS: keep it short and simple.
The slides should show key points, one idea per slide. For a presentation, it is good to remember 1 slide per minute. When using technical terms in a presentation, it is a good idea to give an explanation of the technical terms. This will help the audience to have a better understanding of the presentation.

On the slides use short phrases, but make sure to capture the important points. The only exception to this is when quoting something, and it can be cited in its entirety. A good rule to follow when preparing a Power Point presentation is the “6X6” rule. The rule is to use 6 words per line and 6 lines per slide, not including the title. Fonts should be large enough for the audience to see, font size 32-44 for titles and no smaller than 28 point for text or bullet items. Presentations should have a consistent look throughout each slide. So, it’s important to use the same font, size, color and capitalization format. Short, strong statements should be used, and the bullet point should open with a noun or verb in active voice. The same structure should be used for each slide.
Flash
[edit | edit source]Macromedia Flash can take the power of presentations to the next level. With the addition of movies, sounds, animations and more integrative options a flash presentations can be more advanced and powerful then a PowerPoint presentation, since Flash is not specific a platform for creating presentations. Though flash presentations are hard to make then PowerPoint presentations..flash really allows more freedom to everything to an artistic presentation. A company by the name of Impact Engine designs custom flash presentations for companies. www.presentationengine.com.
About Flash
Flash® Professional 8 is the industry's most advanced authoring environment for creating interactive websites, digital experiences and mobile content.
With Flash Professional 8, creative professionals design and author interactive content rich with video, graphics, and animation for truly unique, engaging websites, presentations or mobile content.
Why Flash Professional 8
Great ideas deserve great tools. Flash provides full design control to maximize creativity, resulting in a consistent end-user experience across a variety of platforms.
Build once, deliver anywhere.
Unleash applications to the web, Windows, Macintosh, Unix, PDAs, and even cell phones. Reach the widest possible audience via the Flash Player, installed on 98% of desktops globally.
Create rich and compelling 2D animations with the tool that brought animation to the Web. Take video where it has never gone before by taking advantage of the most widely deployed video platform on the Internet.
Occasional users may be interested in Flash Basic 8—a subset of Flash Professional 8 which includes all the core functionality needed to design simple motion graphics and interactivity for delivery to the Flash Player. Find out more.
Video editing and DVD authoring software
[edit | edit source]Video Editing: Video can be imported to a video editing program by connecting the camera to a computer or inserting the storage media containing the video into the computer through a DVD/CD drive. After it has been imported, the user can delete or change scenes, add voice-overs, or other special effects. Some editing software even allows you to edit the video in high definition format.
DVD Authoring: Organizing content that is to be transferred to DVD. This can involve importing videos, creating a playback menu to control the media, or burning data onto a rewritable DVD.
WEB Browser and WEB applications
[edit | edit source]- ↑ "Antivirus software". comodo.com. Retrieved 2016-04-25.
- ↑ microsoft
- ↑ auslogic
- ↑ piriform

